UPDATE 2023-06-28: A section of the second paragraph of this article describing the FCEB hosts we examined for this analysis was edited for clarity.
Executive Summary
On June 13, CISA released BOD 23-02 with the objective of mitigating the risks associated with remotely accessible management interfaces that might allow configuration or control of federal agency networks from the public internet. These internet-exposed devices have long been the low-hanging fruit for threat actors to gain unauthorized access to important assets, and it’s encouraging that the federal government is taking this step to proactively improve their overall security posture and those of their adjacent systems.
Censys researchers conducted analysis of the attack surfaces of more than 50 Federal Civilian Executive Branch (FCEB) organizations and sub-organizations. Throughout our investigation, we discovered a total of over 13,000 distinct hosts spread across more than 100 autonomous systems associated with these entities. Examining the services running on these hosts, Censys found hundreds of publicly exposed devices within the scope outlined in the directive.
Findings
Censys conducted a search specifically for publicly accessible remote management interfaces associated with networked devices including but not limited to routers, access points, firewalls, VPNs, and other remote server management technologies.
In the course of our research, we discovered nearly 250 instances of web interfaces for hosts exposing network appliances, many of which were running remote protocols such as SSH and TELNET. Among these were various Cisco network devices with exposed Adaptive Security Device Manager interfaces, enterprise Cradlepoint router interfaces exposing wireless network details, and many popular firewall solutions such as Fortinet Fortiguard and SonicWall appliances.
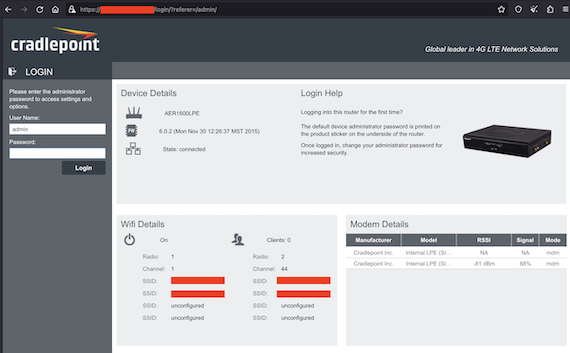
Publicly Accessible Cradlepoint Router Web Interface attributed to an FCEB organization
Over 15 instances of exposed remote access protocols such as FTP, SMB, NetBIOS, and SNMP were also found running on FCEB-related hosts. These protocols have a history of security vulnerabilities, and exposing them to the internet raises the risk of being targeted by threat actors trying to gain remote unauthorized access to government infrastructure.
Multiple out-of-band remote server management devices such as Lantronix SLC console servers. Per CISA’s directive, “These out of band interfaces should never be directly accessible via the public internet.”
Beyond the scope of BOD 23-02, we also identified other noteworthy security concerns on these hosts, including:
- Multiple instances of exposed managed file transfer tools, such as MOVEit transfer, GoAnywhere MFT, VanDyke VShell file transfer, and SolarWinds Serv-U file transfer. Managed file transfer services are often targeted in data theft attacks due to the sensitive nature of the data they handle.
- Over 10 hosts running HTTP services exposing directory listings of file systems, a common source of sensitive data leakage
- Exposed Nessus vulnerability scanning servers, which are designed to pinpoint weaknesses in internal networks and thereby become a target as a source of network intel and springboard for future attacks
- Exposed physical Barracuda Email Security Gateway appliances, which recently made headlines after a critical zero day was discovered being actively exploited to steal data
- Over 150 instances of end-of-life software, including Microsoft IIS, OpenSSL, and Exim. End-of-life software is more susceptible to new vulnerabilities and exploits because it no longer receives security updates, making it an easy target
Next Steps
FCEB agencies are required to take action in compliance with BOD 23-02 within 14 days of identifying one of these devices, either by securing it according to Zero Trust Architecture concepts or removing the device from the public internet. While this mandate directly applies to FCEB organizations, it’s recommended that all organizations regardless of size take steps to identify and harden these interfaces within their networks, as these are often easy targets for threat actors.