Two months ago, in January of 2022, Censys reported on the spread of a new variant of ransomware dubbed Deadbolt. This ransomware targeted a series of network-attached storage devices (NAS) for consumers and small businesses running the QNAP QTS (Linux-based) operating system. What makes this particular variant unique is its communication with the victim. Instead of encrypting the entire device, which effectively takes the device offline (and out of the purview of Censys), the ransomware only targets specific backup directories for encryption and vandalizes the web administration interface with an informational message explaining how to remove the infection.
Due to how this ransomware communicates with the victim, Censys could easily find infected devices exposed on the public internet via this simple search query. Along with general information about what hosts were infected with Deadbolt, we could also obtain and track every unique bitcoin wallet address used as a ransom drop.
At its peak on January 26th, 2022, Censys observed 4,988 Deadbolt-infected services out of the 130,000 QNAP devices currently on the internet. If every victim had paid the ransom, this attack would have netted the hackers about $4,484,700. Fortunately, QNAP jumped into action with a forced firmware update that allegedly fixed the issue (which had its own set of problems), and for the next few months, the infections declined to less than 300 devices. It was looking like this problem was behind us.
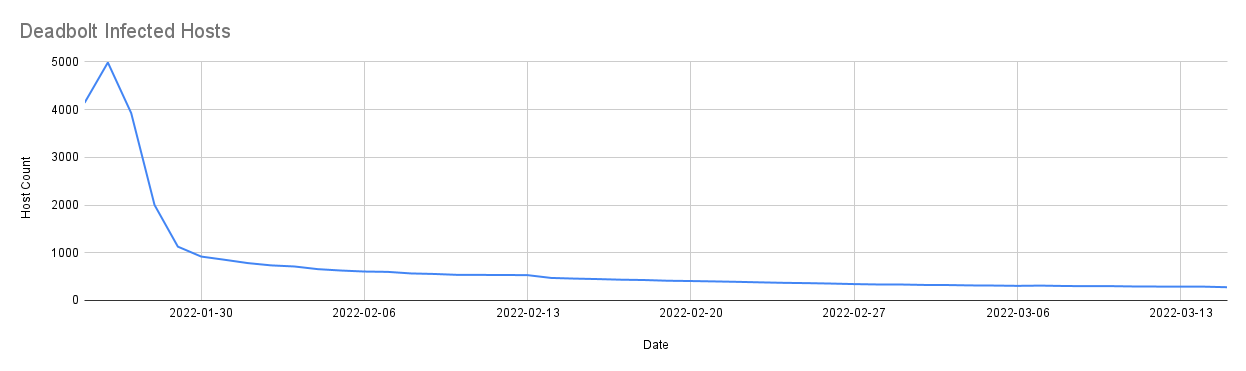
Then, in mid-February, it was reported by users on Reddit that Deadbolt began targeting ASUSTOR ADM devices. Apparently, the same indicators of compromise could be seen in the ASUSTOR attack, but Censys could not find a single instance of this specific compromise within our dataset. By this time, Censys was still observing a steady decline in the number of QNAP infections.
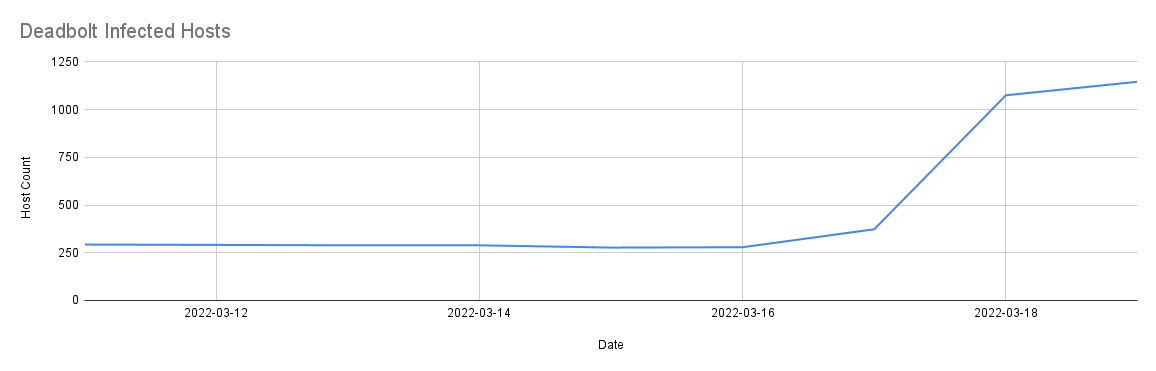
But fast forward to March 2022, and Censys was surprised to see a sudden uptick of new infections targeting the same QNAP QTS devices. This recent attack started slowly, with two new infections (a total of 373 infections) on March 16th, and over the course of three days, Censys observed 869 newly infected services. By March 19th, the number of Deadbolt-infected services had risen to 1,146!
Except for the BTC addresses used to send ransoms to, the attack remains the same: backup files are encrypted, the web administration interface is modified, and victims are greeted with the following messages:
At this time, Censys cannot state whether this is a new attack targeting different versions of the QTS operating system, or if it’s the original exploit targeting unpatched QNAP devices. But this is what we know right now:
- The ransom for victims is the same as before, 0.030000 BTC for a decryption key (about USD 1,223)
- The ransom for QNAP is the same:
- 5 BTC for information related to the vulnerabilities (USD 203,988)
- 50 BTC for a master key to unlock all affected victims (USD 2,039,885)
- A majority of these devices were identified running the QNAP QTS Linux kernel version 5.10.60.
- The new infections do not seem to be targeting a specific organization or country, infections seem to be evenly split between various consumer internet service providers.
Censys will continue to monitor this new Deadbolt infection and update this post accordingly.