Published on 09.19.2022
Part 1: Redis
Takeaways
- There are 39,405 unauthenticated Redis services out of 350,675 total Redis services on the public internet.
- Almost 50% of unauthenticated Redis services on the internet show signs of an attempted compromise.
Preface
In this new series of posts, we decided to answer the question: “What is the state of databases on the Internet?”. We can answer this question in extreme detail using our dataset.
This report is the first of several. Over the coming months, we will release a detailed analysis of several different database technologies, and we will begin our journey into “Databases. EXPOSED!” with the popular in-memory database: Redis
But before we go much further, let’s talk about what it means for a database to be “exposed” on the Internet. Our scanner will attempt to speak the native language of whatever service we are trying to enumerate. For example, our scanner will construct a packet that only a MySQL server knows how to handle, and in return, we get a response that gives us more information about that running service.
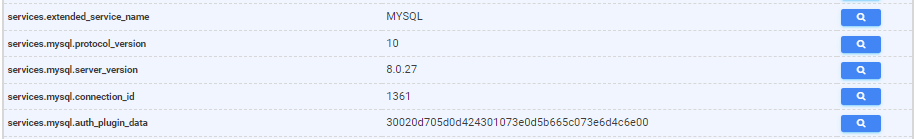
A MySQL server’s handshake response.
Censys will never attempt to authenticate with any of the database services we find. We establish a handshake with the remote server using the native protocol and parse the responses into a set of fields, making searching easier.
At the time of writing, there were 220,010,967 hosts with one or more exposed Internet services. Of those, 5,889,954 hosts (2.6% of the total) are running one or more of the twelve database technologies we will discuss throughout this series. Below is a graph showing our top databases ordered by the number of services.
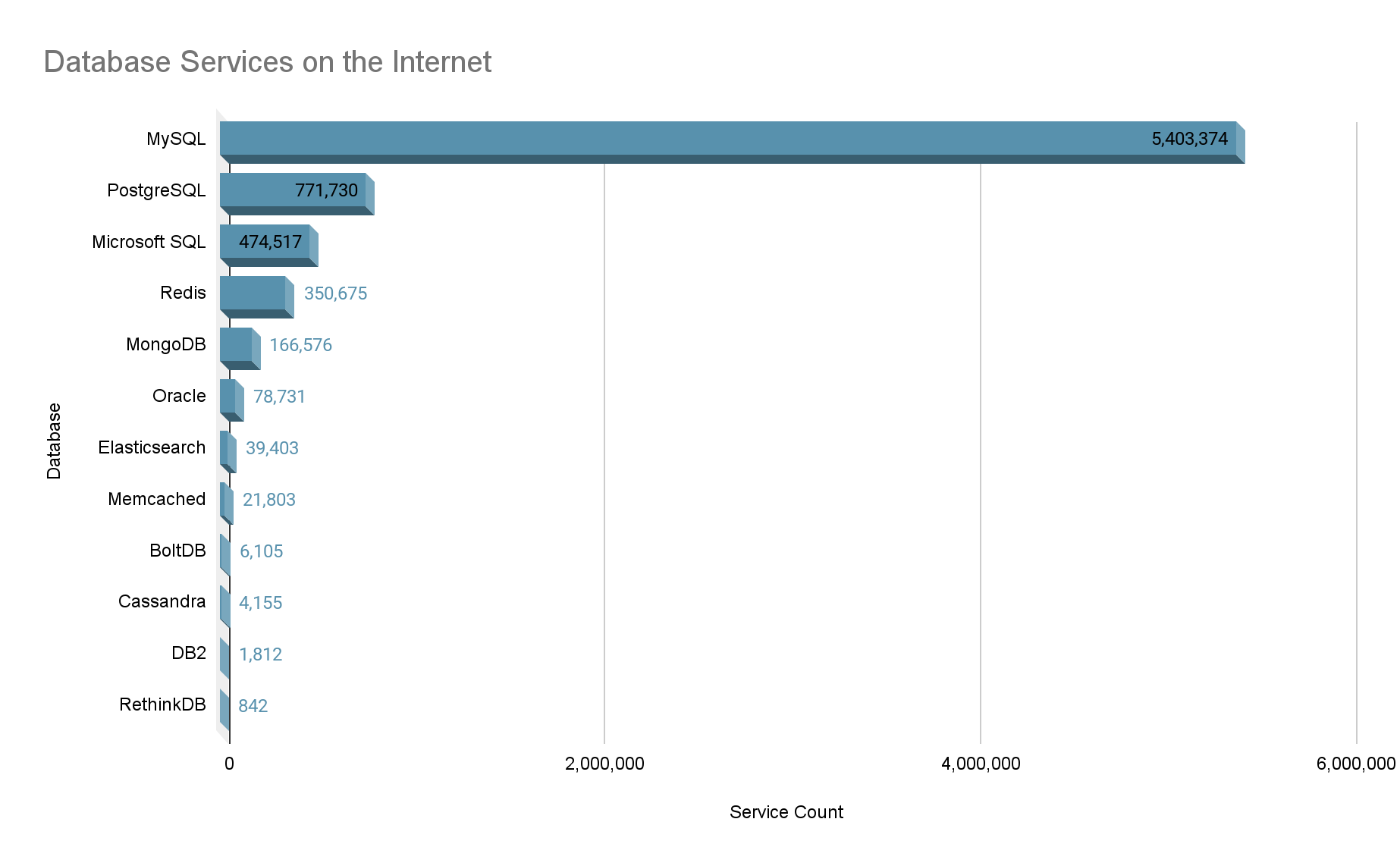
(Database services found by Censys)