Date of Disclosure (source): February 5, 2025 (PoC made available on February 23, 2025)
CVE-2025-20029 is a high severity vulnerability affecting the iControl REST interface and TMOS Shell (tmsh) components of F5’s BIG-IP system, with a CVSS score of 8.7. Successful exploitation allows an authenticated attacker to execute arbitrary system commands, potentially leading to root-level access of the BIG-IP platform.
There is currently no evidence of this vulnerability being actively exploited. However, a publicly available proof of concept (PoC) has been published here on GitHub, increasing the likelihood that this vulnerability may be exploited by threat actors in the future. The PoC shared above demonstrates how an attacker authenticated as a low-privilege account (e.g., auditor role) can execute arbitrary system commands as the ‘root’ user. The exploit leverages tmsh commands, such as save, which can then be run with elevated privileges that allow an attacker to make changes to the underlying system. This vulnerability has been patched by F5 through multiple version releases. Additionally, the vendor’s advisory recommends that users consider implementing one or more of the mitigation steps below for securing access to the iControl REST interface and the tmsh:
- Block iControl REST access through the management interface to trusted users
- Restrict access to the BIG-IP command line through SSH
- Block SSH access through self IP addresses
- Block SSH access through the management interface
| Field | Details | |||||
|---|---|---|---|---|---|---|
| CVE-ID | CVE-2025-20029 – CVSS 8.7 (high) – assigned by F5 Networks | |||||
| Vulnerability Description | A command injection vulnerability in all modules of F5’s BIG-IP platform that targets the iControl REST interface and tmsh components. A low privilege user can leverage commands to bypass restrictions, inject arbitrary commands, and perform actions as the “root” user of the target system. | |||||
| Date of Disclosure | February 5, 2025 (PoC published on February 23, 2025) | |||||
| Affected Assets | iControl REST interface and tmsh components of F5 BIG-IP Platform (all modules). | |||||
| Vulnerable Software Versions |
The following versions of F5 BIG-IP (all modules) are affected:
|
|||||
| PoC Available? | A PoC is publicly available here. | |||||
| Exploitation Status | We did not observe this vulnerability on CISA’s list of known exploited vulnerabilities or in GreyNoise at the time of writing. | |||||
| Patch Status |
F5 Networks has introduced a fix in each of the following versions:
|
|||||
Censys Perspective
At the time of writing, Censys observed 1,124 (excluding virtual hosts) exposed instances of the F5 BIG-IP Configuration Utility, 30% of which are geolocated in the United States. Note that not all instances observed are vulnerable as we do not have specific versions available.
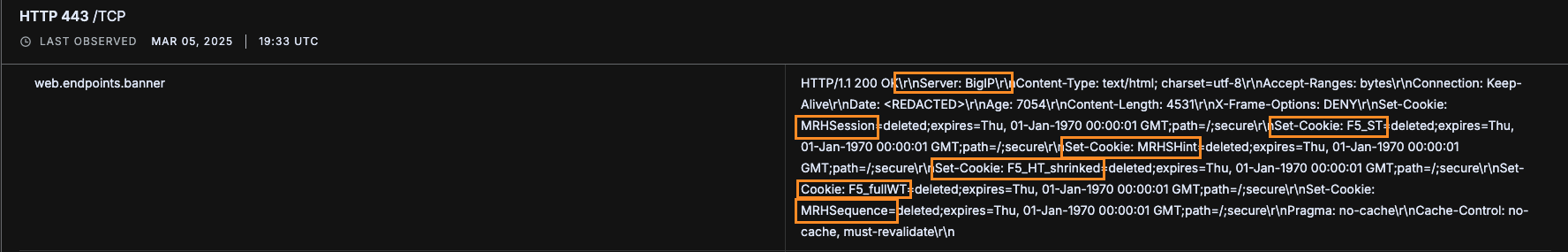
Additionally, we saw that 437,204 devices appear to be using BIG-IP for load-balancing and other modular services provided by the BIG-IP platform. These devices were associated with BIG-IP based on session cookies identified in the response headers that are indicative of BIG-IP usage. These devices are not necessarily exposed to the vulnerability though, as BIG-IP often functions as a proxy between the client and server.
host.services.software: (vendor: “F5” and product: “IP Configuration Utility”) and not host.labels.value: {“HONEYPOT”, “TARPIT”}
services.software: (vendor= “F5” and product: “IP Configuration Utility”) and not labels: {honeypot, tarpit}
host.services.software: (vendor= “F5” and product: “IP Configuration Utility”) and not host.labels: {honeypot, tarpit}





