Summary
- A critical path traversal vulnerability was discovered in the Muhttpd server used by many Arris gateway routers which was assigned CVE-2022-31793.
- If successful, an attacker could obtain access to the device’s configuration, including access to passwords.
- Several major ISPs have been identified as using this vulnerable software.
- Arris devices can be found using the following Censys search query.
Introduction
On July 29th, 2022, Derek Abdine, a security researcher, disclosed multiple vulnerabilities in Arris routers, the most critical being CVE-2022-31793. This vulnerability allows a remote, unauthenticated user to access and download any file on the device’s filesystem using a simple path traversal exploit. A more sophisticated attacker can download the device’s system settings, including the WiFi and administrator password settings.
Commonly found in residential networks and small businesses, these routers are the only thing separating the internet from individuals who thought themselves safe from external threats. Since these devices are given to customers by their internet provider, the known and potential exposure is vast. However, the culprit of this vulnerability lies within the underlying software that handles HTTP requests for a network administration page: Muhttpd, an embeddable HTTP daemon written in the C programming language. It is important to note that this vulnerability has existed in the source code since the first commit back in 2006, meaning any device using this software has been potentially exploitable for over sixteen years.
Identifying
At the time of writing (Aug 2nd, 2022), Censys observed 20,081 unique hosts that seem to be running an internet-exposed Arris router administration interface. And while Censys can only monitor devices that have been configured to accept external connections, it is estimated that millions of devices may have been vulnerable to this particular exploit:
“There are millions more that are not Internet-facing or not easily identifiable from the Internet (depending on aggregate ISP deployment footprint).” – Original Advisory
Although, as part of the responsible disclosure, multiple ISPs were notified and have since patched a majority of the vulnerable devices.
Using a simple Censys search query, we were able to determine that the majority of these devices can be found in the autonomous system ATT-INTERNET4 (AS7018) with over 15,000 devices, followed up by WINDSTREAM (AS7029) with 2,300 hosts.
| Autonomous System |
Host Count |
| ATT-INTERNET4 |
15,760 |
| WINDSTREAM |
2,300 |
| FRONTIER-FRTR |
1,122 |
| SNET-FCC |
793 |
| ZIPLY-FIBER |
26 |
Since the installation of these devices seem to be isolated to only a small number of ISPs (albeit giant ISPs), the majority of them are located in the US, with a few hosts here and there in Canada. Below is a geographic map of all observable Arris routers as seen by Censys.
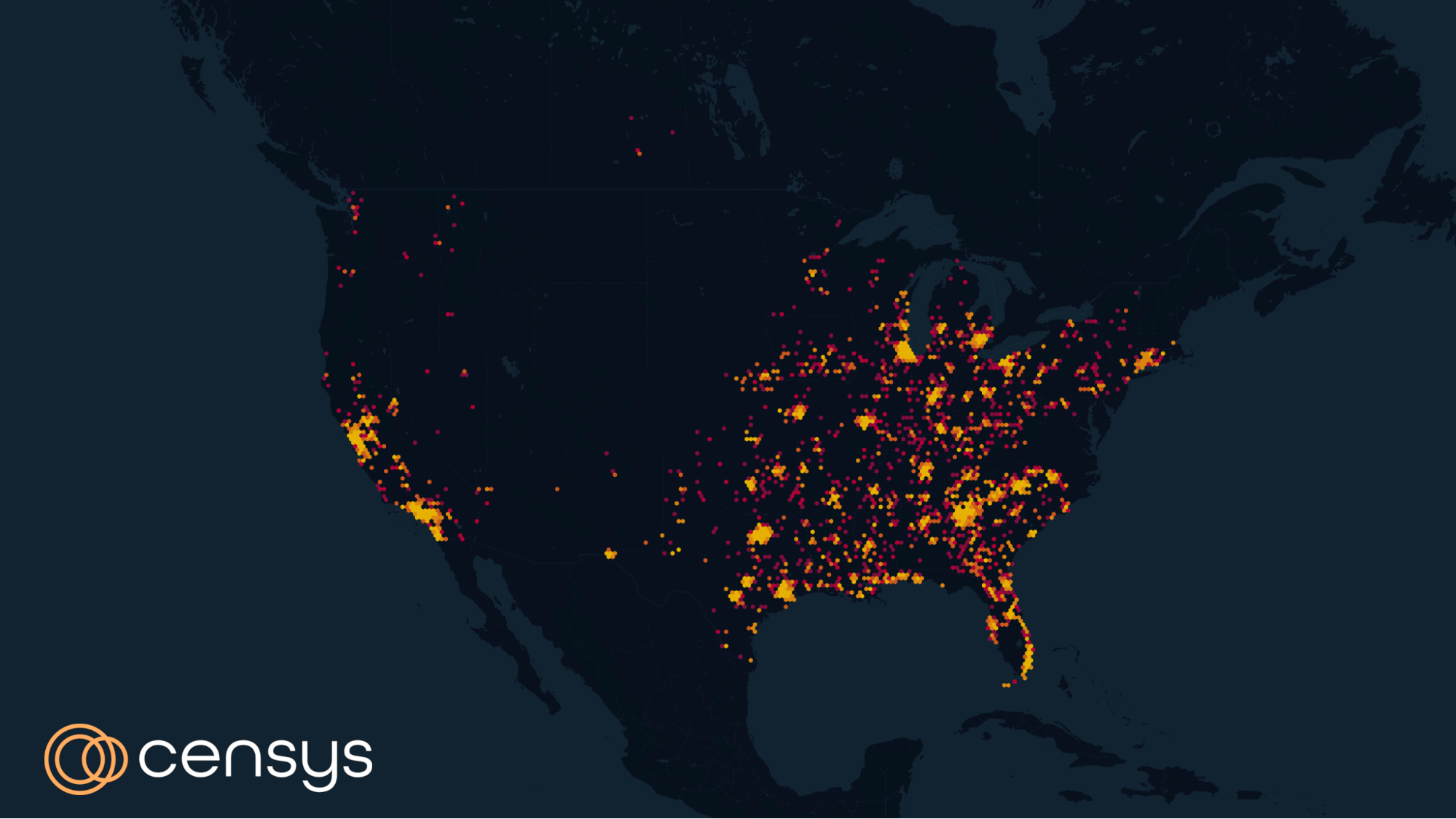
As stated in the original blog post, a complete list of affected devices has not been made public; the security community has been attempting to validate vulnerable devices by issuing a simple GET request to their own Arris devices. Along with verified models listed on Derek’s blog (NVG443, NVG599, NVG589, NVG510, BGW210, and BGW320), Censys has found NVG443B and NVG578HLX also to be exploitable.
Below is a simple command one can use to validate whether a device is vulnerable or not by fetching a non-invasive file from the server.