Executive Summary:
- On April 19, 2024, CrushFTP patched CVE-2024-4040, a zero day virtual file system escape vulnerability in its WebInstance software that is undergoing active exploitation in the wild.
- If successfully exploited, this vulnerability would allow an unauthenticated actor to potentially access any sensitive data a customer managed with the FTP client and achieve full system compromise.
- As of April 23, 2024, Censys observed nearly 4,900 hosts running over 5,700 unique CrushFTP WebInterface instances exposed on the public internet. Nearly half of these are based in the U.S.
- These numbers remain largely consistent with the host and service counts of exposed CrushFTP WebInterfaces observed one week ago (April 16th), suggesting that either instances are being remediated and left online, or there may not be broader action taken in response to this vulnerability yet.
- Remember our earlier research about deceptive hosts? We’ve observed approximately 2,500 hosts online that all display a CrushFTP WebInstance favicon, yet lack any signs of genuinely running the software.
- File sharing software, especially web-based tools exposed on the public internet, remain prime targets for threat actors given the often sensitive nature of the data they transfer
- Censys Attack Surface Management customers can search their workspaces for affected instances using this query: risks.name: ‘Exposed CrushFTP WebInterface
- See our official Rapid Response advisory for more context
Background
On April 19, 2024, developers of the file transfer tool CrushFTP patched a zero day vulnerability in its WebInterface software, tracked as CVE-2024-4040. The vulnerability, discovered by Airbus security engineer Simon Garrelou, is a virtual machine escape flaw that could allow an unauthenticated user to break out of CrushFTP’s virtual file system (VFS) and access system files. When it was reported, the vulnerability affected all known versions of CrushFTP. The issue is now patched in version 10.7.1 for v10 releases and 11.1.0 for v11 releases.
Sources at CrowdStrike have detected instances of this exploit being attempted in the wild. This vulnerability didn’t get assigned a CVE identifier until 4 days later, on April 22, with a CVSS score of 7.7 (“High” severity). This delay is likely due to the ongoing challenges faced by NIST in processing their growing backlog of CVEs.
CrushFTP is an “enterprise grade” file transfer tool that supports FTP, or File Transfer Protocol, as well as its more secure variants (SFTP, FTPS). FTP is a standard network protocol widely used to transfer digital files between hosts. An FTP client serves as a user interface for connecting to remote FTP servers and managing files. While the first FTP clients were simple command-line programs, they’ve since evolved to include web-based applications, enabling users to access FTP functionality directly from a web browser. These tools have gained popularity because of their more user-friendly interfaces. However, integrating any web-based interface with other services can potentially expand a system’s attack surface. Any vulnerabilities or authentication weaknesses within these web-based components can be exploited to compromise adjacent systems or underlying services – as demonstrated in this case with CrushFTP’s WebInterface.
Given the potentially sensitive data they often interact with, file sharing tools continue to be an appealing target for malicious actors.
Advisory Confusion
While it’s commendable that CrushFTP promptly patched the issue after it was disclosed, this is one of the more confusing security advisories we’ve seen. There are multiple inconsistencies between the wiki pages intended for customers running version 10 compared to those using version 11, and both seem to have undergone edits to key information independently of each other.
Since the time of disclosure, the v10 wiki page has stated that customers using a DMZ in front of their CrushFTP instances were safe from this vulnerability.
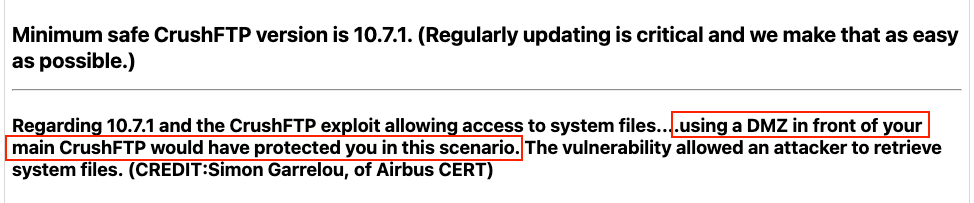
The “Crush10wiki” page, last updated April 19
The v11 page, however, has been reflecting slightly different information, stating that the DMZ only “sort of” provides safety:

The “Crush11wiki” page before April 22
The next day, the same v11 page read:
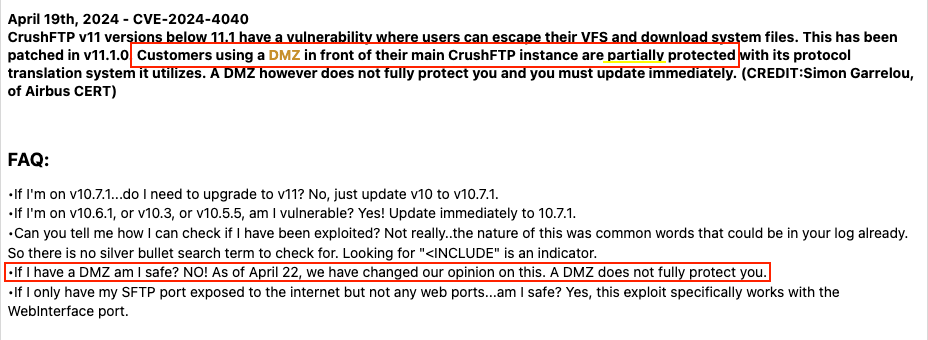
The “Crush11wiki” page after edits made on April 22
As of the morning of Tuesday April 23, the v10 page still displays the following, apparently outdated information at the top:
Regarding 10.7.1 and the CrushFTP exploit allowing access to system files….using a DMZ in front of your main CrushFTP would have protected you in this scenario.
There are other peculiar statements in here that are less than helpful. As the screenshots above show, a bullet point on the FAQ reads:
“Can you tell me how I can check if I have been exploited? Not really..the nature of this was common words that could be in your log already. So there is no silver bullet search term to check for. Looking for “<INCLUDE” is an indicator.”
Checking your logs is always a good first step, but the hesitant tone in this response does not inspire much confidence.
Censys’s Perspective
On April 23, 2024, Censys observed 4,899 hosts running 5,704* unique CrushFTP WebInterface instances. Just under half of these services are hosted in the United States.
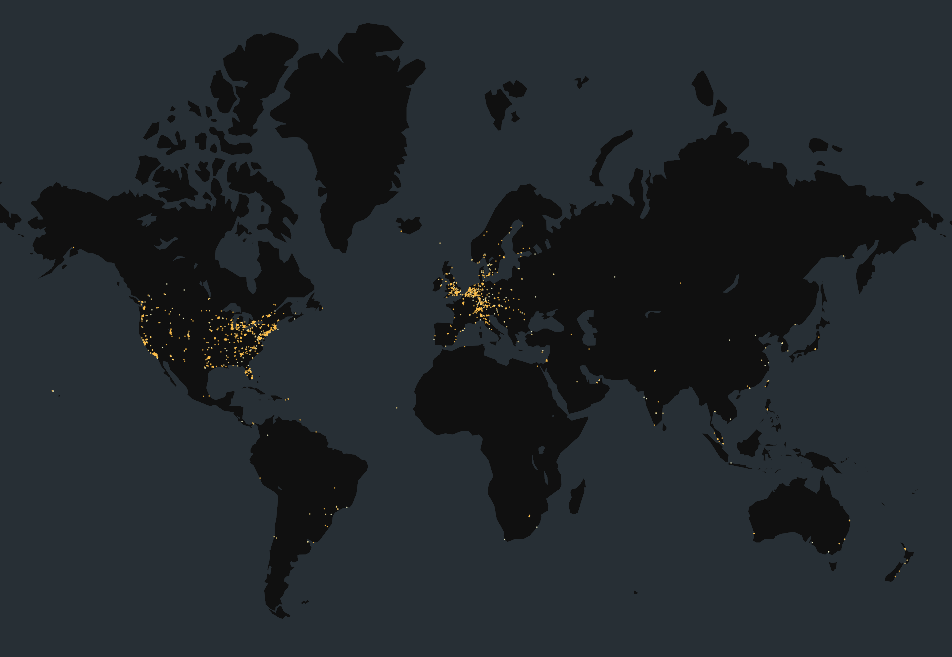
Map of global Censys-visible Exposed CrushFTP WebInterface services on April 23, 2024
This is comparable to the levels of exposure observed a week ago on April 16, 2024, with minor fluctuations of around 50 to 60 instances. Censys does not have visibility into the versions of CrushFTP software in use, so there could be various scenarios unfolding here. Considering how recently the patches were released, it’s likely they haven’t been widely deployed yet, although this is speculative.
*These numbers account for both virtual and physical hosts, with duplicates removed so as not to artificially inflate the state of exposure. There may be variations compared to figures reported directly in Censys Search results.
Over 2,750 of CrushFTP exposures are observed within the United States, making up nearly half of all exposures we see.
As expected, cloud networks emerge as a popular choice for hosting these services. Currently, nearly 18% of all exposed WebInterface services are hosted on platforms such as Microsoft Cloud, Amazon AWS, or Google Cloud. It’s also expected that we find some internet service providers like Comcast and UUNET in this mix. This is likely a reflection of small businesses and consumers using this software. The presence of Hetzner and OVH, two major hosting and data center providers, is unsurprising, considering that FTP tools are commonly deployed for web hosting purposes.
Deceptive Hosts
As of April 23, 2024, Censys identified around 2,500 hosts in our dataset returning CrushFTP WebInstance favicons, but without evidence of actually running the software. These hosts were exclusively based in AMAZON-02 or AMAZON-AES. These findings mirror our earlier observations on “deceptive hosts”.
Many open-source software detection frameworks use unique favicon hashes to identify specific software products. The CrushFTP rule in question that triggered on these deceptive hosts checks for a favicon with an md5 hash of `297a81069094d00a052733d3a0537d18`, as defined in rapid7’s Recog database.
These deceptive hosts typically trigger many of these software detection rules – and it’s likely intentional. Considering that many of the software products we’ve observed them emulate are linked with recent critical security vulnerabilities, this behavior is likely aimed at vulnerability scanners and internet scanners. In one case, we found a host presenting both a CrushFTP favicon and a PAN-OS GlobalProtect artifact in the HTTP response body. In other cases, some of these hosts presented an Ivanti Connect Secure HTML title. Both PAN-OS GlobalProtect and Ivanti Connect Secure have been associated with significant vulnerabilities in recent months.
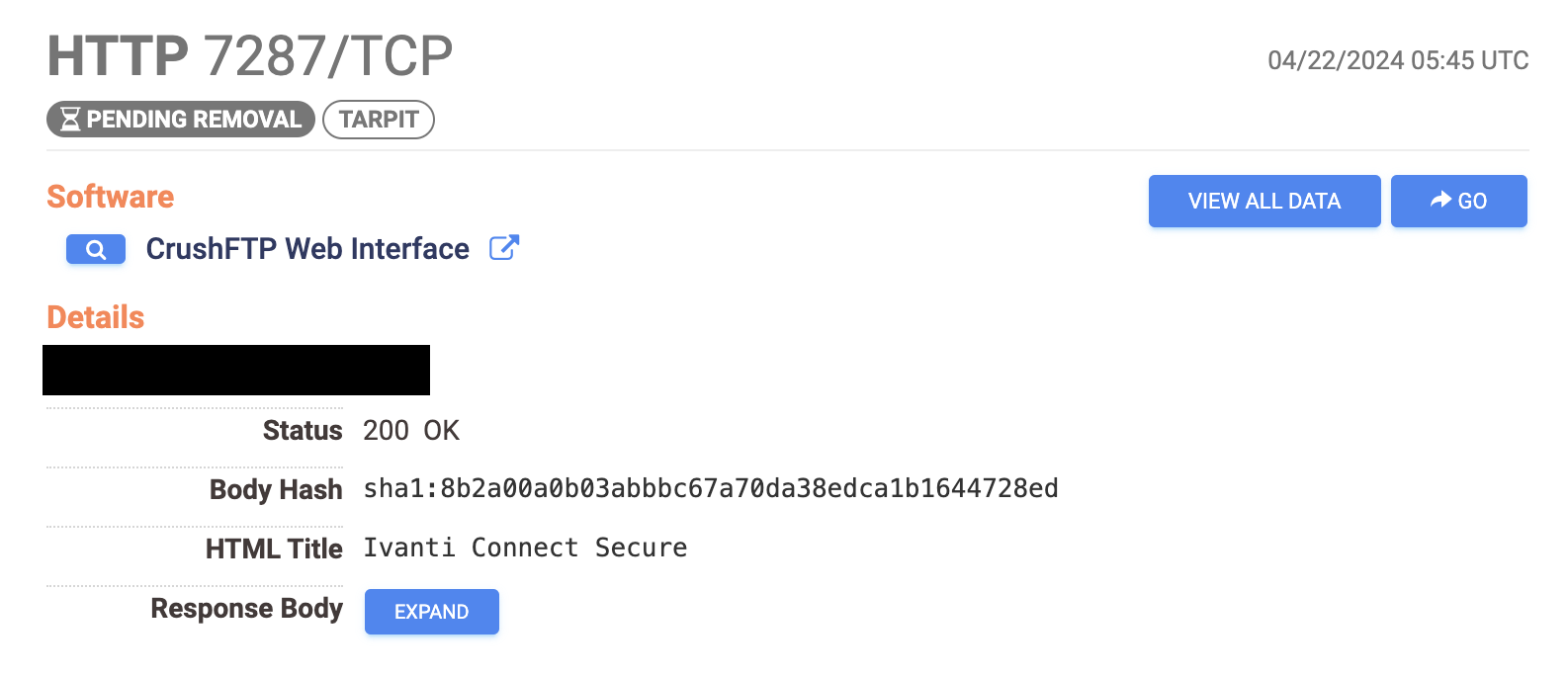

Let’s be clear: this is highly unusual. Crafting a favicon to imitate another product or service takes effort– you have to obtain the image, then ensure it’s correctly displayed by your web server. While it’s too early to draw definitive conclusions about these host’s intentions, it’s clear that whoever is behind them is no amateur.
As a heads up, you can exclude these hosts from your Censys Search results by adding and not services.labels=”tarpit” to your query.
What Can Be Done?
- Upgrade your CrushFTP instances ASAP if you have not already done so. Here are instructions for how to do so for v10 and v11.
| Version | Patch |
| 11.0.x | 11.1.0 |
| 10.x.x | 10.7.1 |
| Earlier than 10.x.x | 11.1.0 |
- Please be aware that initial suggestions that using a DMZ would protect your CrushFTP instance from this vulnerability aren’t fully accurate. It’s recommended to upgrade your software versions to effectively mitigate this vulnerability.
References:
- https://nvd.nist.gov/vuln/detail/CVE-2024-4040
- https://www.crushftp.com/crush11wiki/Wiki.jsp?page=Update
- https://www.crushftp.com/crush10wiki/Wiki.jsp?page=Update&version=27
- https://www.reddit.com/r/crowdstrike/comments/1c88788/situational_awareness_20240419_crushftp_virtual/
- https://www.rapid7.com/blog/post/2024/04/23/etr-unauthenticated-crushftp-zero-day-enables-complete-server-compromise/