What does your organization’s digital attack surface look like in terms of access control and vulnerabilities? Accurate?
Security teams may think they have a full view of everything connected to their organization. However, in reality, most are dealing with visibility gaps caused by Shadow IT, ephemeral cloud instances, and other digital assets spun up outside their purview.
In fact, Censys finds that up to 80% of an organization’s attack surface is unknown (more on what makes up an attack surface, below). Additionally, nearly 70% of organizations said that they’ve experienced an attack that resulted from an unknown, unmanaged, or poorly-managed external attack surface.
These digital assets are problematic because security teams can’t monitor and defend their network if they don’t have a complete understanding of what they own. Maintaining an effective security posture requires knowing how many assets you have, who within the organization owns them, where they live, and which might be vulnerable to a social engineering attack, phishing attack, or other attack.
This need to document and continuously refresh the organization’s digital attack surface is what makes attack surface mapping such an integral part of any security strategy.
Securing Your Network with Attack Surface Mapping
Attack surface mapping is the process of identifying, monitoring, and managing all of the external-facing assets belonging to an organization that are exposed to the public internet (and in turn, threat actors). Effective mapping allows organizations to understand their attack surface, including any hidden or unknown assets that may have been overlooked or misconfigured.
What Do We Mean By Attack Surface?
There are various types of attack surface, including:
- External Attack Surface: Assets exposed to the public internet, such as domains, IP addresses, and web servers.
- Internal Attack Surface: Assets within an organization’s private network that could be exploited if attackers gain internal access.
Understanding the different types of attack surface is essential for implementing effective security strategies.
When we talk about the external attack surface, we’re referring to all external-facing assets that could potentially be exploited by attackers to gain unauthorized access to a system or network. These assets include any publicly-exposed digital resources that interact with the outside world.
Typical components of an attack surface include:
- IP addresses
- Domains
- Web servers
- Cloud resources (such as storage buckets or virtual machines)
- Web applications (a key focus of application security)
- IoT devices

Additionally, TLS/SSL certificates, APIs, and even DNS records can be part of an attack surface that requires vulnerability scanning. As organizations expand their digital attack surface through cloud environments, SaaS applications, and distributed infrastructures, their attack surface grows, increasing the risk of vulnerabilities and cyber threats.
The Evolving Attack Surface
Attack surfaces are anything but static. In fact, there’s a good chance that what your attack surface looked like yesterday isn’t what it looks like today. Most attack surfaces are constantly evolving as new assets are deployed, outdated assets are retired, Shadow IT assets make their way online, and cloud instances continuously change.
All of this change means that traditional, point-in-time efforts to map an attack surface aren’t sufficient. Manually taking inventory of assets on a monthly, bi-monthly, or even weekly creates security risks, as in between these mapping efforts, assets may become exposed, vulnerable, and targeted by threat actors.
Alternatively, an attack surface mapper solution provides a real-time view of the evolving attack surface, giving security teams the visibility they need to close gaps and reduce the attack surface.
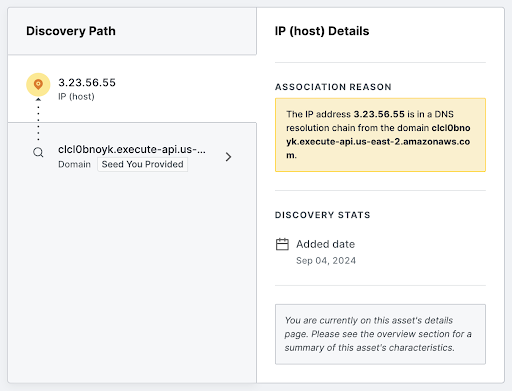
The Importance of Attack Surface Analysis
Understanding and managing the attack surface is critical for security teams and developers as it enables them to mitigate risks associated with exposed assets. Attack surface mapping, facilitated by tools like external Attack Surface Management, gives teams a way to achieve this objective on an ongoing basis.
How Organizations Benefit from Mapping Attack Surfaces
- Improved Risk Awareness: By using attack surface mapping tools, security teams can gain visibility into exposed assets, helping them understand potential entry points for attackers. This awareness allows for proactive risk management.
- Early Detection of Vulnerabilities: Continuous security testing and attack surface analysis helps identify potential threats in real-time, allowing teams to address misconfigurations, outdated software, or exposed services that could be housing sensitive data before attackers can use them as potential attack vectors.
- Enhanced Incident Response: With a well-managed attack surface, security teams can respond more efficiently to security incidents, as they have a clear picture of all exposed assets and their potential risks.
- Prioritization of Critical Assets: Attack Surface Management tools help prioritize vulnerabilities based on the likelihood of exploitation and business impact, ensuring that the most critical risks are addressed first.
- Protection Against Shadow IT: Developers often deploy cloud resources or services that may not be formally tracked by IT departments (aka: Shadow IT). Cloud attack surface discovery identifies these assets, ensuring they’re properly secured.
- Compliance and Regulatory Adherence: Maintaining a current inventory of internet-facing assets through attack surface mapping helps organizations meet compliance requirements and reduce the likelihood of violations.
- Reduced Attack Window: By continuously mapping the attack surface, organizations can reduce the time vulnerabilities remain exposed, shrinking the window of opportunity for attackers.
- Proactive Ransomware Defense: By managing exposed assets that could be targeted by ransomware, organizations can mitigate risks early, reducing the chances of a successful ransomware attack. Exposed, public-facing assets are the number one point of entry for ransomware groups.
Best Practices for Attack Surface Mapping and Analysis
Now that we’ve established why attack surface mapping is important, let’s talk about what your attack surface mapping efforts should look like to ensure maximum effectiveness. As mentioned, security teams can turn to an attack surface mapping tool, like Attack Surface Management, to gain a complete view of their digital footprint. When evaluating Attack Surface Management mapping and analysis options, look for those that give you the ability to:
- Continuously Discover and Inventory Assets: Update your inventory of all internet-facing assets, including servers, IP addresses, cloud environments, and IoT devices on a daily basis. This ensures that newly deployed or modified assets are tracked and secured against security breaches. Continuous monitoring is crucial, as assets can change frequently, especially in dynamic environments like cloud services.
- Automate Asset Discovery: Use automated tools to scan and discover assets regularly. Automated asset discovery ensures no gaps are missed in the attack surface, especially when dealing with complex environments where assets might be unknown or unmanaged, such as those involving subsidiaries and acquisitions.
- Prioritize Risks Based on Impact: Not all vulnerabilities are created equal. Use risk-based prioritization to focus on assets that are most likely to be targeted and exploited. This involves considering factors like the business value of assets, known vulnerabilities, and the likelihood of exploitation.
- Monitor Cloud Assets and Ephemeral Resources: Ensure that your attack surface management includes visibility into cloud-based assets and dynamic resources like containers, serverless functions, and cloud storage buckets. These assets can be spun up and decommissioned rapidly, creating new risks if not monitored continuously.
- Leverage Attribution for Accurate Asset Ownership: Use attribution techniques to ensure that assets discovered are properly assigned to the right organization, especially in environments with complex ownership structures, such as subsidiaries or cloud service providers. This reduces false positives and ensures accurate attack surface representation.
- Implement Strong Security Controls and Patch Management: Limit access to critical systems and apply patches regularly. Ensure that publicly exposed services have proper authentication and are up to date to prevent exploitation by attackers scanning the internet for unpatched vulnerabilities.
- Track and Manage Certificates and TLS Configurations: SSL/TLS misconfigurations are a common attack vector. Regularly scan and update certificates, ensuring they are valid and properly configured to prevent attackers from exploiting expired or weak certificates.
- Regularly Validate Remediation Efforts: Conduct continuous scans to validate that vulnerabilities have been patched correctly and that new exposures haven’t been introduced. This helps confirm that previous issues are fully remediated and secure.
Attack Surface Mapping with Censys
Censys Attack Surface Management goes beyond traditional asset discovery and mapping by offering daily updates and real-time visibility that mitigate challenges in attack surface mapping. This proactive approach ensures that organizations can reduce their attack surface, respond quickly to changes, secure new assets, and maintain a comprehensive understanding of their attack surface, preventing attacks like ransomware and other exploits from succeeding.
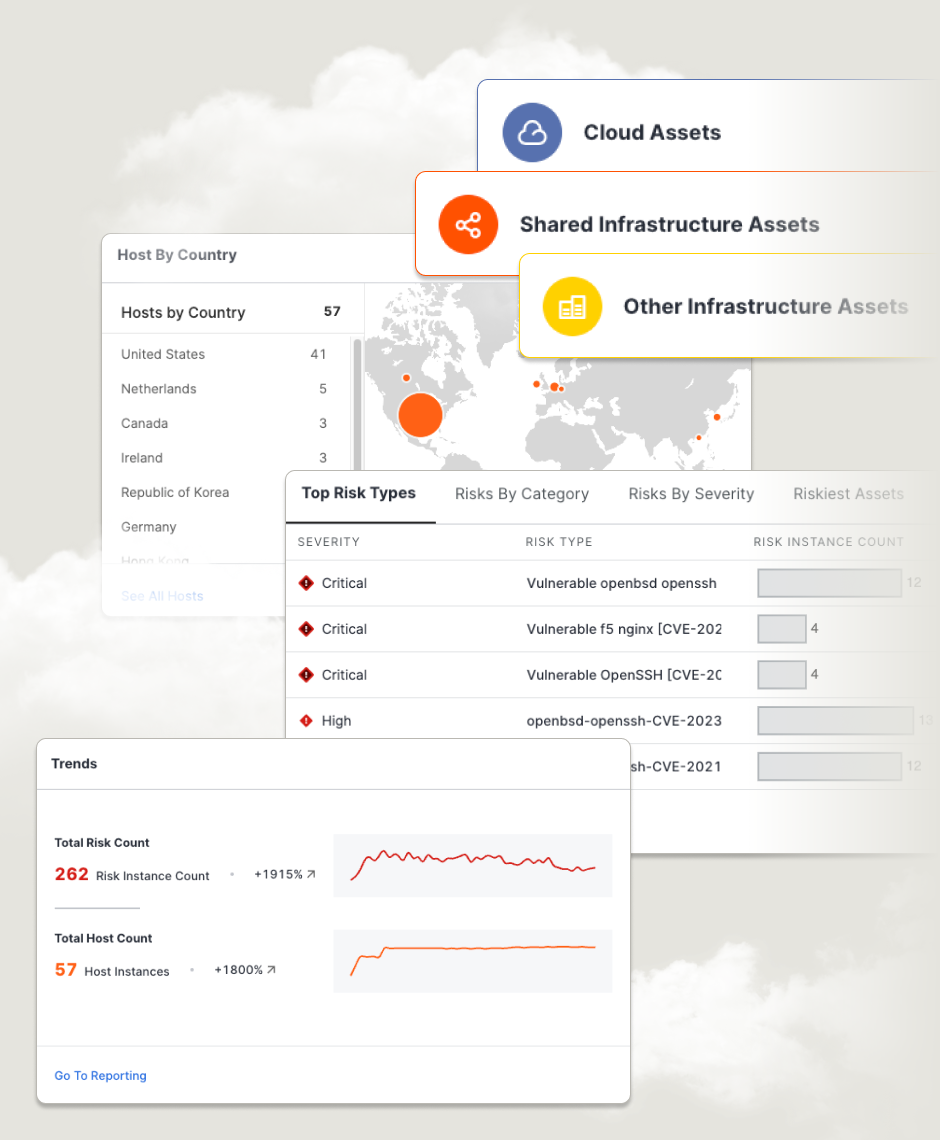
With Censys ASM, teams looking for an attack surface mapping solution benefit from:
Continuous Asset Discovery Censys continuously scans the internet to discover and attribute all public-facing assets associated with an organization. This includes traditional assets like domains, IP addresses, and certificates, as well as ephemeral assets such as cloud storage buckets and dynamic cloud resources. Censys’ internet-wide scanning ensures that any new or changed assets are identified in near real-time, allowing organizations to stay ahead of potential exposures.
Daily Updates and Automated Seed Refresh One of Censys’ core strengths is its ability to perform daily asset discovery updates. This includes scanning all 65,535+ ports and processing updates for hosts, domains, certificates, and web entities. Automated seed refreshes ensure that new assets—whether introduced by mergers, acquisitions, or new subsidiaries—are quickly discovered and added to the attack surface, ensuring continuous coverage.
Risk-Based Prioritization Censys helps security teams prioritize their response to vulnerabilities by providing rich context around discovered assets. The platform highlights the most critical exposures based on factors such as CVE data and likelihood of exploitation. This allows teams to focus on the assets that present the highest risk to the organization.
Comprehensive Cloud Visibility Censys offers deep integration with cloud environments, including AWS, Azure, and GCP, through its Cloud Connectors. These connectors update multiple times per day, ensuring that any newly spun-up cloud resources are discovered quickly and monitored for security issues.. This is particularly important for managing the security of cloud-native and ephemeral resources that change frequently.
Advanced Attribution for Accurate Mapping Censys’ attribution process is a key differentiator in attack surface mapping. The platform uses advanced techniques, including data from certificates, DNS records, and WHOIS data, to accurately attribute assets to their rightful owners. This reduces false positives and ensures that all assets within an organization’s attack surface are correctly identified.
Comprehensive Port and Protocol Scanning Censys’ scanning capabilities are unparalleled, covering all 65,000+ ports and using predictive scanning to identify services running on non-standard ports. This level of depth ensures that even hard-to-detect services are discovered and mapped, providing organizations with a more complete view of their attack surface.
Real-Time Alerts and Integrations Censys provides tailored security alerts, allowing organizations to receive notifications based on their priorities—such as changes to critical assets or emerging vulnerabilities. These alerts are integrated into existing workflows and security tools (e.g., SIEM, SOAR, and ticketing systems) to streamline incident response and remediation.
Deep Search Capabilities Censys’ platform includes a powerful search functionality that allows users to query their asset inventory using over 2,000+ scan data fields. This gives security teams detailed insights into their assets, including open ports, services, HTTP response data, and cloud provider details, helping to uncover any hidden exposures.
Map It, Manage It, Secure It
By leveraging attack surface mapping tools, security teams can gain continuous visibility into exposed assets, detect vulnerabilities in real-time, and prioritize risk management efforts. Whether you’re monitoring cloud environments or defending against Shadow IT, solutions like Censys provide the necessary attack surface insights to stay ahead of advanced cyber threats.
Interested in more resources about mapping and managing your attack surface? Check out our ASM 101 whitepaper, Think Like an Attacker ebook, or our ASM Buyer’s Guide.