Vulnerability Description:
CVE-2026-24061 is a critical remote authentication bypass vulnerability in GNU Inetutils telnetd that allows unauthenticated attackers to gain root-level access to affected systems. The vulnerability stems from improper sanitization of the USER environment variable before passing it to the login(1) process. An attacker can craft a USER value of “-f root” to bypass authentication and automatically log in as the root user, resulting in remote code execution with full system privileges. The flaw has been present since version 1.9.3 (released May 12, 2015) and went undetected for approximately 11 years.
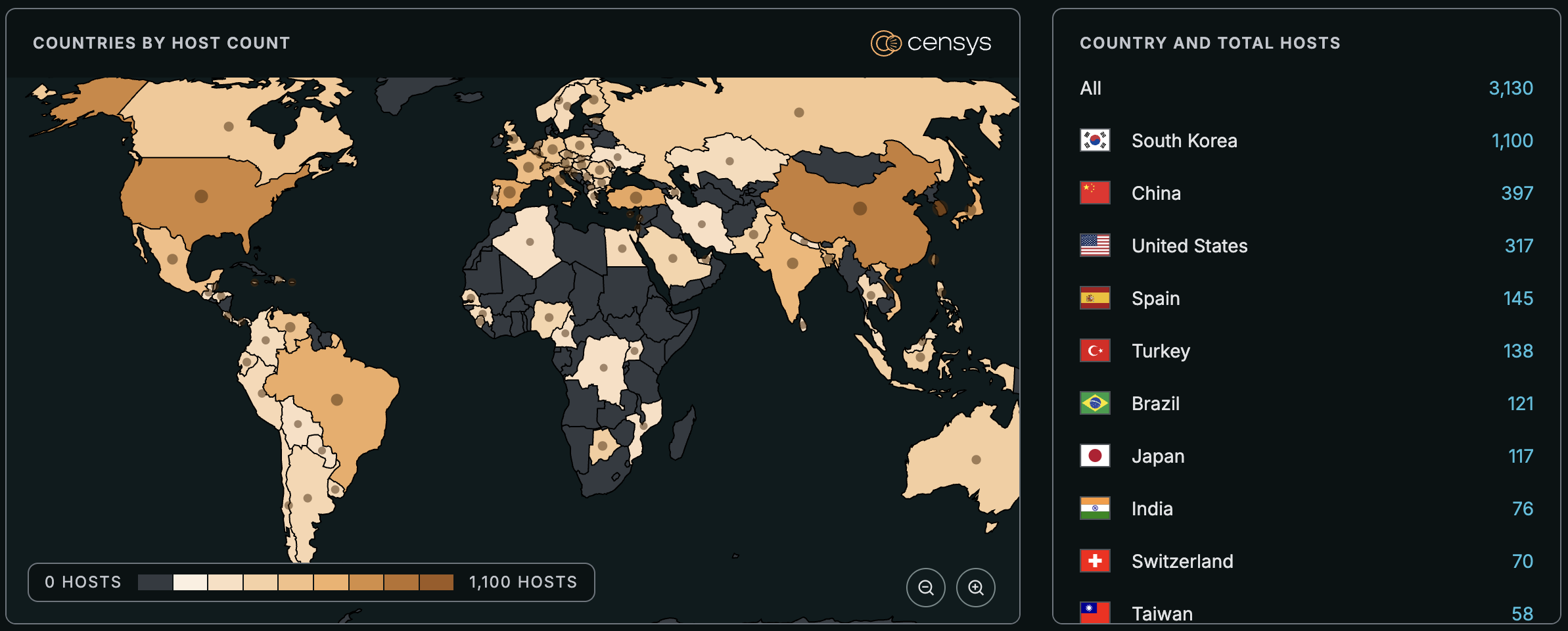
See the full breakdown by country in Censys Platform →
| Field | Description |
| CVE-ID | CVE-2026-24061 — CVSS score: 9.8 — assigned by MITRE |
| Vulnerability Description | A critical remote authentication bypass vulnerability in GNU Inetutils telnetd allows unauthenticated attackers to gain root-level access to affected systems. An attacker can craft a USER value of “-f root” to bypass authentication and automatically log in as the root user, resulting in remote code execution with full system privileges. |
| Date of Disclosure | January 21, 2026 |
| Affected Assets | Any system running GNU Inetutils telnetd version 1.9.3 up to and including version 2.7 with the telnet daemon exposed to the network. Systems running telnetd from inetutils that allow login sessions via the login utility are at high risk. Notably, telnetd compiled with PAM or other hardening mechanisms may not be vulnerable depending on system configuration. |
| Vulnerable Software Versions | GNU Inetutils telnetd version 1.9.3 up to and including version 2.7 |
| PoC Available | Yes. Multiple public proof-of-concept exploits are available demonstrating unauthenticated root login using USER=-f root via Telnet. The attack is simple and requires no special tools. |
| Exploitation Status | GreyNoise observed opportunistic scanning and exploitation attempts within hours of public disclosure, with attackers deploying post-exploitation payloads and system probes targeting embedded and poorly maintained Linux systems. Several honeypots have captured exploitation behavior attempting root logins via -f flag abuse.In total as of Monday, January 26, 2026 they have observed 183 distinct IPs targeting this vulnerability (source: GreyNoise) |
| Patch Status | A patch has been merged upstream in GNU Inetutils 2.8, and the issue was officially acknowledged in GNU’s bug tracker. Distributions such as Debian, Arch, and NixOS have issued updates. Users are advised to upgrade immediately to a patched version or disable telnetd entirely, especially if exposed to the internet.As a workaround, removing -f support from login(1) or firewalling Telnet services can help reduce exposure. |
Censys Perspective
At the time of writing, Censys observes 3,130 exposed hosts, trackable with the following queries:
host.services: (protocol: "TELNET" and banner=~"w+s+[0-9]+.[0-9]+(.[0-9]+)*(-[w-]+)?s+([^)]+)s+([^)]+)")ASM:
host.services.telnet.banner: /.w+s+[0-9]+.[0-9]+./services: (service_name= "TELNET" and banner:/.w+s+[0-9]+.[0-9]+./) 




