Censys takes seriously its mission to be a good steward of the internet. We are actively reaching out to the organizations that we determined could be impacted by the following findings. As part of our duty of care, all Censys research is conducted and shared in a way that prioritizes public safety. This means that we withhold highly-sensitive information from our public reports, and never name organizations that could be negatively impacted by our findings.
Introduction
Industrial control systems (ICS) are a vital part of critical infrastructure, responsible for regulating power, water, and other essential resources delivered to municipalities. Given the essential services they facilitate, it’s incredibly important that these systems run without any disruption to service.
As such, these devices and systems are increasingly attractive targets for threat actors, particularly state-backed actors, who are seeking to cause chaos or lay the groundwork for future strategic attacks. As new Censys research into water ICS and other operational technology (OT) devices highlights, some internet-facing devices are making it all too easy for adversaries to take action. These vulnerable ICS reflect larger security issues facing internet-connected critical infrastructure systems throughout the United States.
The Aliquippa Municipal Water Authority Hack
On November 25, 2023, the Municipal Water Authority of Aliquippa, Pennsylvania discovered it had been compromised by an Iranian Islamic Revolutionary Guard Corps (IRGC)-affiliated hacking group. The group, known as the CyberAv3ngers, took control of a water pressure monitoring and regulation system at a remote pumping station, defacing the system’s interface with an anti-Israel message. According to CISA’s advisory,“The threat actors compromised Unitronics Vision Series PLCs with human machine interfaces (HMI). These compromised devices were publicly exposed to the internet with default passwords and by default are on TCP port 20256.” The CyberAv3ngers began targeting Israeli-made Unitronics PLCs in the wake of conflict in the region, claiming responsibility for multiple attacks on Unitronics devices globally.
While recovery from the attack in Aliquippa required manual work from Water Authority employees, there was reportedly no effect on customers’ water service or quality. However, the implications of such an attack loom large, especially considering how many of these and other ICS devices are exposed to the public internet.
Given the potential impact, Censys set out to identify other exposed Unitronics devices and services associated with water, wastewater, and energy systems in the United States.

Screenshot from an affected device via VNC
Unitronics Exposures
Censys observed a total of 149 internet-exposed Unitronics devices and services in the United States, running a combination of the following:
- 39 PCOM services
- 94 API endpoints
- 96 Web Admin panels
- 95 with VNC exposed, 3 of which didn’t require authentication
Most of these internet-exposed PLCs are remote devices connected via LTE or 5G. While in some cases it may be reasonable for these devices to be internet-connected, they should always be protected by a Virtual Private Network (VPN) or behind a firewall with restricted access.
CISA has advised that organizations disconnect these devices from the internet. However, if remote access is required, CISA states that administrators should:
“Implement a Firewall/VPN in front of the PLC to control network access to the remote PLC. A VPN or gateway device can enable multi factor authentication for remote access even if the PLC does not support multi factor authentication. Unitronics also has a secure cellular based longhaul transport device that is secure to their cloud services.”
In evaluating these Unitronics devices and services, we see they face problems in multiple directions: exposed protocols, exposed web control panels, and exposed VNC.
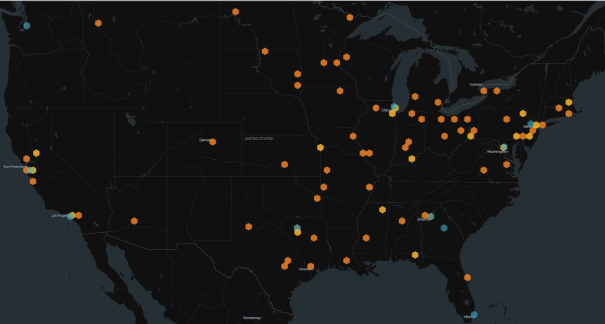
Data from 2024-01-25; Orange: Real devices; Blue: Suspected honeypots
PCOM Protocol Exposures
PCOM is a proprietary Unitronics protocol that allows applications to interact with PLC devices. Information such as device model name, hardware version, OS build number, and OS version number can be obtained via interaction with the PCOM protocol. A threat actor could use this protocol to query process-related values and underlying inputs and outputs, which could be used to change device configurations or disrupt PLC operations entirely.
Hazards or Honeypots?
The good news is that many of the exposed PCOM services we observe in the U.S. appear to be honeypots — dummy servers used to mimic real internet hosts. In fact, we assess that only 32% of PCOM services in the U.S. are real devices. The fact that there are so many honeypots is not necessarily unexpected, as researchers are likely trying to collect more information in the wake of recent attacks. However, it is a bit surprising that so many of the total number of PCOM services we see appear to be honeypots.
Panel Passwords Are a Problem
Unitronics PLC web control panels are programmed with a default “1111” password. Default passwords are an inherent security risk, and CISA recently released an advisory urging organizations to stop using them. Remarkably, many of these web control panels’ default credentials were never changed by their system administrators. Given these devices are also exposed to the public internet, this poor password security presents a particularly egregious security risk.
VNC: Additional Attack Surface
Unitronics PLCs also allow remote access to the human machine interface (HMI) via VNC. As a best practice, VNC should not be exposed to the public internet and should always require authentication. Exposed VNC, especially when combined with weak or no passwords, provides threat actors with means to trivially cause harm or disrupt operations.
Other OT Exposures
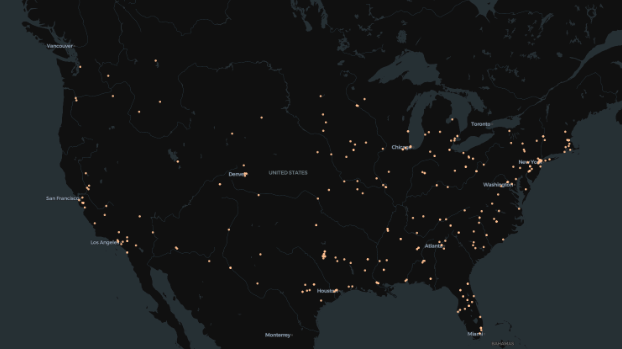
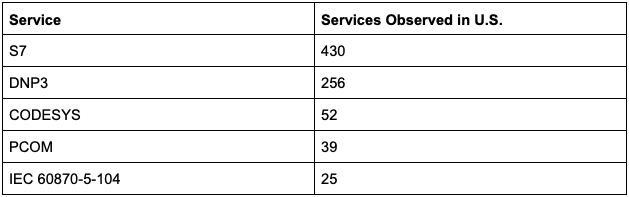
Data from 2024-01-25; S7, DNP3, CODESYS, PCOM, and IEC 60870-5-104 services observed in the U.S.
These problematic exposures go beyond just water and Unitronics services and devices. Censys also observed that exposures were present across a number of other internet-facing OT services related to critical infrastructure sectors, like energy.
Censys observed the following exposures across a selection of OT protocols:
Though these devices are public-facing, determining who owns them can be a challenge. This is because many of these devices run on LTE/5G mobile routers on mobile networks, which obfuscate details about device ownership.
However, Censys was able to determine ownership for a number of the exposed devices, and to date has notified over 20 organizations of their exposure risk.
The Larger Issue
The exposures that we observed across Unitronics services and devices and other OT systems contribute to a larger conversation about the state of critical infrastructure security in the U.S. Many critical infrastructure devices are simply “on” the internet, and without the right measures in place, can become easy points of entry to nation-state groups and other adversaries looking to do harm.
In a recent House Select Committee hearing, FBI Director Christopher Wray warned that Chinese government-backed hackers are targeting water treatment plants, electrical infrastructure, and oil and gas pipelines. During this same hearing, CISA Director Jen Easterly pointed to basic flaws in critical infrastructure technology, telling lawmakers that, “Unfortunately, the technology underpinning our critical infrastructure is inherently insecure because of decades of software developers not being held liable for defective technology. That has led to incentives where features and speed to market have been prioritized against security, leading our nation vulnerable to cyber invasion. That has to stop.”
Security flaws in technology are just one part of the problem. Administrator skills gaps pose another issue. Many small local and municipal governments are operating with incredibly lean teams, and lack headcount for dedicated IT. As a result, services tied to critical infrastructure are being deployed by OT teams without the security expertise to implement proper controls. The prevalence of default passwords left on Unitronics’ web control panels highlight this well.
These challenges invite lawmakers and decision-makers at all levels of government to consider ways to better regulate and safeguard devices.
To see ICS exposures in your region or across your IP range, you can head over to Censys Search and start with the following query: labels: ics