It’s unfortunate that when the term dwell time entered the cybersecurity lexicon, it focused solely on the attacker’s timeline—the duration an adversary remains undetected in a network. Missing from that view is an equally important metric: defender dwell time—the lag between when a threat artifact is created and when it becomes actionable by researchers, defenders, or sysadmins. How quickly can we respond once the breadcrumbs exist? In a world where attackers move fast and marketing claims move faster, defenders are still constrained by access, visibility, and time.
Back in 2013, I wrote CrowdFMS to solve a simple problem: every day, I was manually fetching YARA rule hits from VirusTotal to get visibility into malware infrastructure. Email notifications helped, but I needed something faster and scalable. So CrowdFMS was built to automate fetching fresh samples, extracted indicators, and got them into a usable format within seconds. IPs and domains could be blocked, analyzed, or folded into whatever lab project I was running. This essentially created the pipeline below:
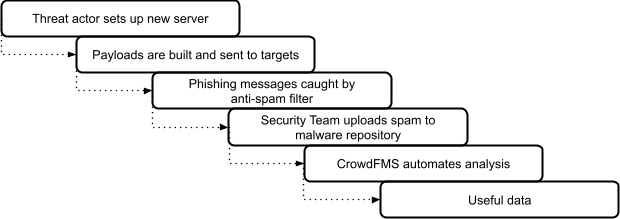
The limitation with this pipeline is the inherent dependence on data being uploaded to a malware repository. No matter how much I optimized for processing performance in CrowdFMS, if a sample wasn’t found or shared for months after use by an attacker, a major part of my dwell time depended on factors outside of my control.
Enter Censys
For years, independently running Internet-wide scans have been an invaluable way researchers have augmented their own visibility. As part of our new Censys Threat module, we’re making this type of threat hunting accessible beyond just researchers.
The Censys Threat module, shown below, allows users to rapidly investigate identified threat actor infrastructure. By enriching our existing fingerprints with context from MITRE and Malpedia, we want to be a resource to better leverage your existing threat intel sources.
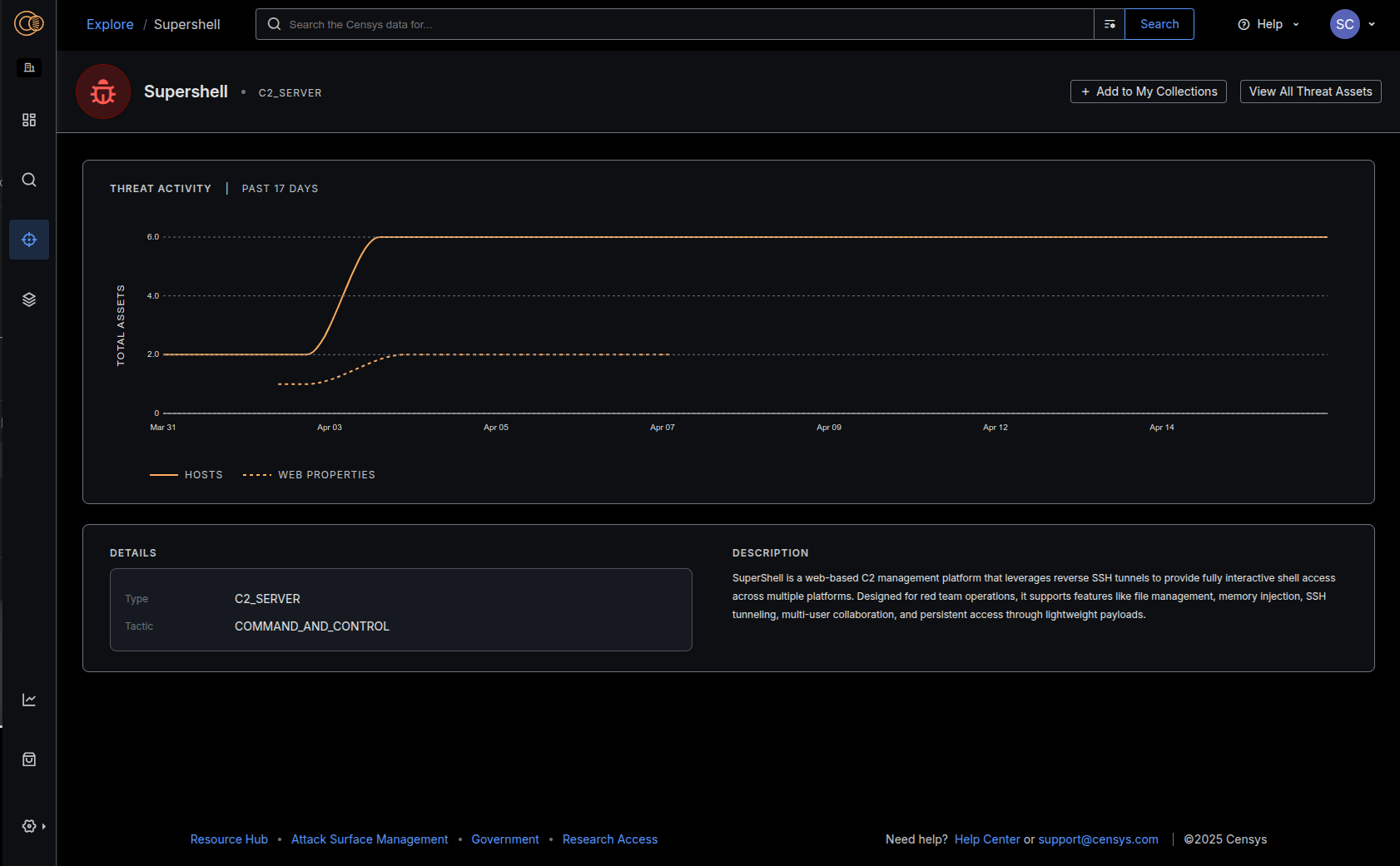
As we build out this module further, we’re roadmapping custom hunting methods, better historic data pivoting, and support for defining custom threat clusters linked to collections. We want to enable teams to build out their own threat universe, while delivering the best visibility into their infrastructure.
Faster than the threats
Our goal is to reduce defender dwell time while making threat hunting faster and more accurate. With the recent launch of Collections earlier this year, users can now save and track search results over time. The Threat Module is designed to become part of your daily workflow, helping you connect the dots faster and act before the threat matures.