The Censys Threat Hunting Module is Now Generally Available!
We’re elated to announce the release of the Threat Hunting Module as part of the newly launched Censys Platform. This isn’t just another feature release—it’s a defining moment for Censys as the authority in Internet Intelligence, built from the ground up to be the world’s most trusted provider of Internet insights.
Since the inception of Censys, we’ve been proud of our accomplishments in making the Internet safer and providing the best data and insights to organizations to help defend against complex threats. We’ve helped Citizen Lab uncover mercenary spyware, we’ve worked with the EPA to reduce the number of exposed water control systems by 94%, and we’ve become a trusted source of Internet intelligence for governments, security companies, and the world’s largest organizations. To us, the standard is not to be “good enough”; we’re here to provide the most timely, accurate data about everything connected to the Internet, enabling organizations, researchers, and governments to solve complex security problems. With that, we aim to transform how our customers think about what’s possible.
The Threat Hunting Module: Providing the best visibility into adversary infrastructure.
We built the new Censys Platform to better support specialized hunt use cases, such as tracking malicious infrastructure, while supporting familiar workflows our users depend upon. We listened closely to our customers and even hired a few former customers to help us move the vision of this product forward. We documented their challenges: the constant race against time, the burden of working with fragmented intelligence, the time and craft needed to find meaningful signals and signatures that are worth tracking. All feedback pointed to the same theme over and over again: it is extremely challenging for security teams to defend against sophisticated attacks by ransomware gangs and APT groups while also having to defend against the constant barrage of commodity threats. With this feedback in mind, we built the Threat Hunting Module.
Subscribe to a Constantly-Updated and Curated View of Adversary Infrastructure
Our module provides unparalleled accuracy and timeliness in identifying evasive and emerging adversary infrastructure. This is your early warning system, your constantly-updated feed of threat updates that your team can use and trust (rather than using yet another feed of stale IOCs). Want to know about the quality of our detections? You can read some of our research here:
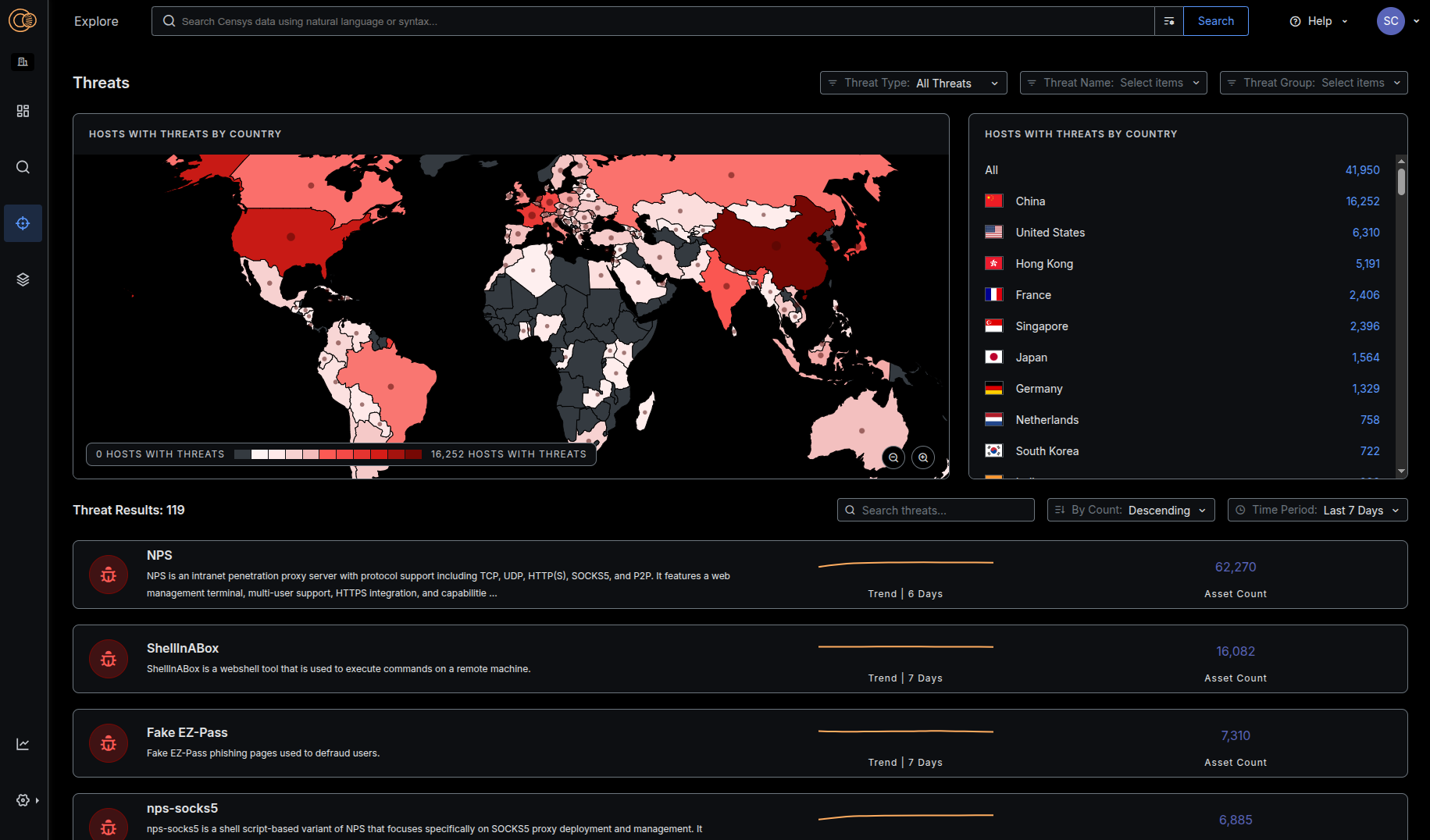
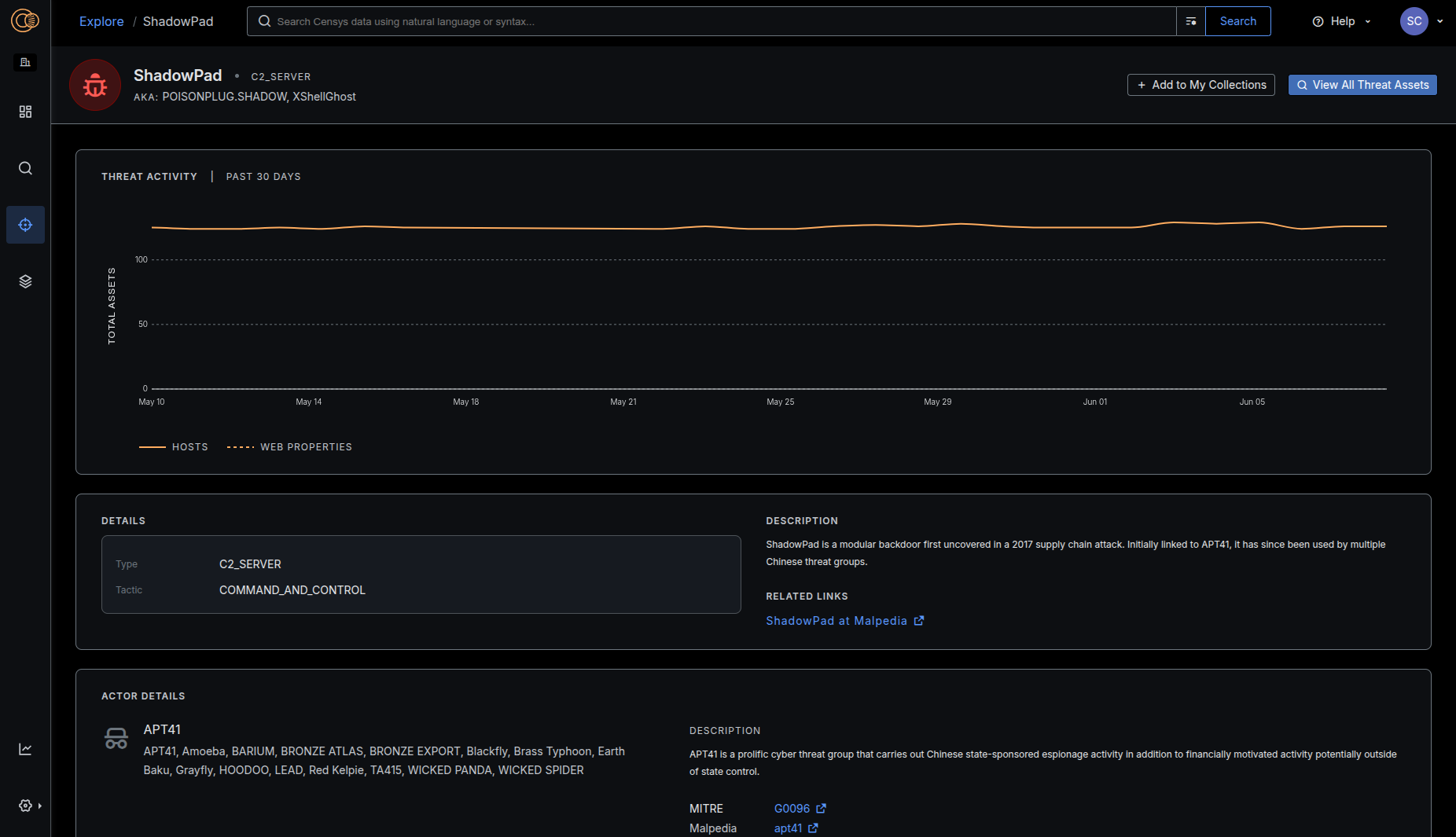
Reference Meaningful Context about Malware and Threat Actors
We’ve added context and insights about how adversary infrastructure changes and evolves (tracking changes as we process scan data) and integrated helpful descriptions and third party links, helping to guide defense strategies.
Our adversary profiles are written to be intelligence provider agnostic; we map the rosetta stone of malware and threat actor groups names, so you can search using names from CrowdStrike, Mandiant, Microsoft and others.
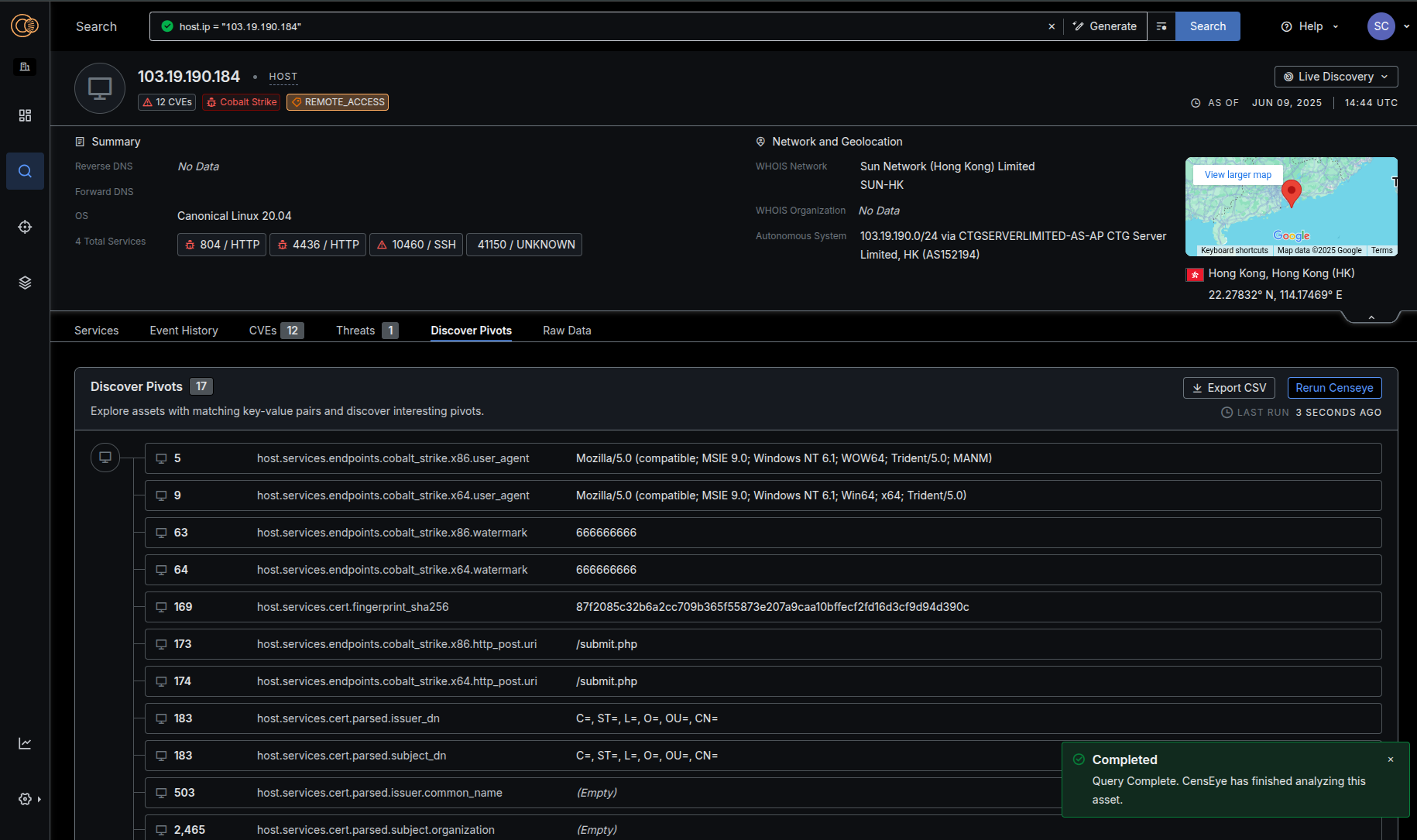
Reduce Investigation Time
We know that sophisticated teams are also tracking patterns relevant to their organizations – they have intelligence and specific investigations that are unique to them. We wanted to give our customers a mechanism to more intuitively explore and actively hunt complex adversary infrastructure in our data, saving organizations countless hours and reducing the cognitive load needed to conduct this work. We’ve added features like CensEye, Certificate Host History Visualizations, and Live Discovery to make this job easier. Read more about how our research team is using these techniques:
Operationalize Adversary Intelligence
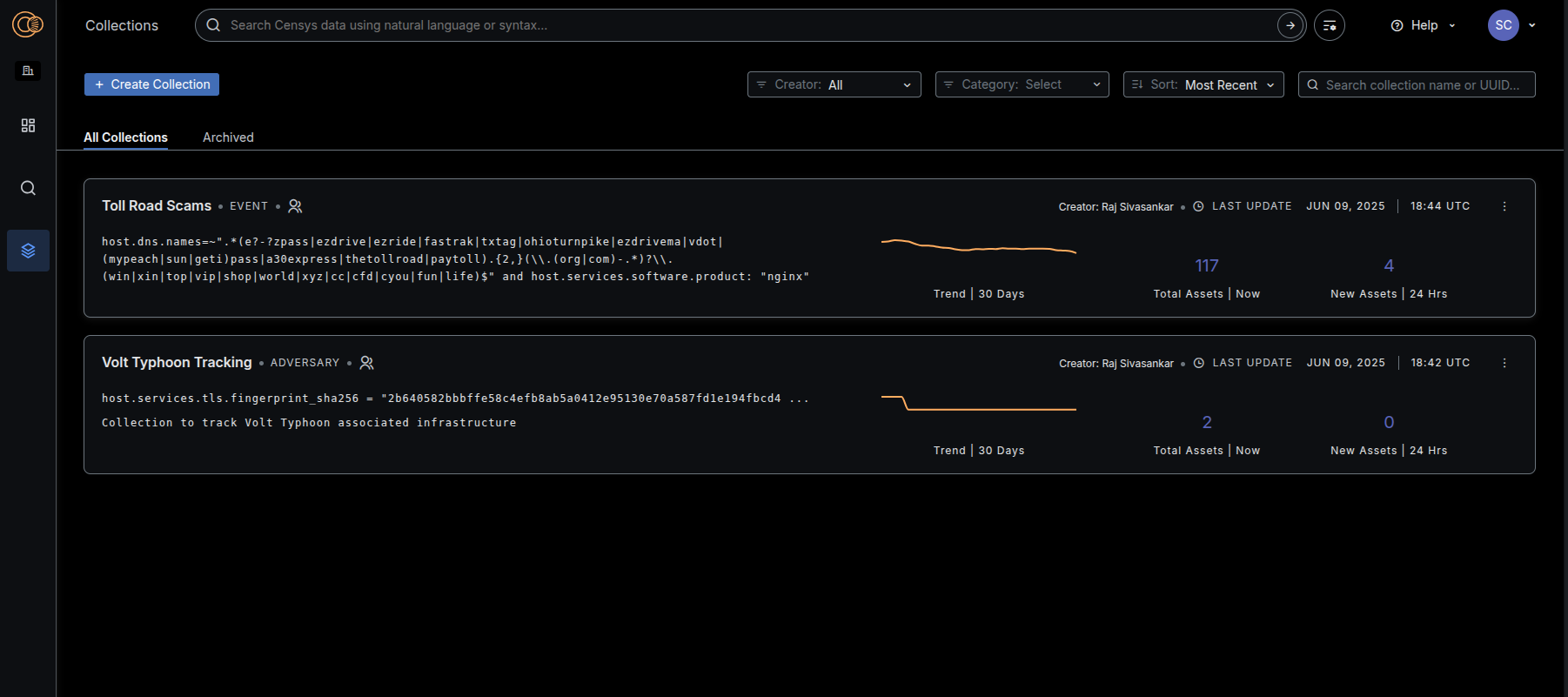
Lastly, we wanted to make it seamless for teams to consume the adversary data and use it to enrich alerts, keep firewall rules current, and receive immediate notifications about infrastructure changes that your team may want to further investigate. We have Collections that allow you to monitor queries over time, leverage webhooks and APIs to get alerted on what’s new or changed, and track historical patterns and events.
Every aspect of the Threat Hunting Module has been meticulously crafted to address the real-world challenges faced by CTI teams, Threat Hunters, and Incident Responders. From the data layer up to the user interface, from core functionality to those features you’ve been requesting forever—we’ve been obsessive about building something that makes even the most demanding security professionals think, “finally.”
See The Threat Hunting Module for Yourself
If you are an existing Censys customer, you can reach out to your Account team to get a demo of the Threat Hunting module and a trial of the new capabilities. If you are new to Censys, you can sign up for a guided demo here.