Vulnerability Description
A cluster of three critical vulnerabilities has been disclosed affecting the Coolify self-hosting platform. These vulnerabilities allow unprivileged or low-privileged users to achieve Remote Code Execution (RCE) as root and bypass authentication mechanisms to steal private SSH keys.
CVE-2025-64419:
This command injection vulnerability enables attackers to execute arbitrary system commands with elevated privileges. The vulnerability exists in the docker compose build pack, where parameters from docker compose files are not properly sanitized, and requires a victim user to create an application from an attacker-controlled repository.
CVE-2025-64420:
This information disclosure vulnerability enables low-privileged users to access a private SSH key, allowing them to authenticate via SSH and potentially gain elevated privileges on the Coolify instance and underlying server.
CVE-2025-64424:
This command injection vulnerability enables low-privileged users (members) to execute arbitrary system commands on the Coolify instance. The vulnerability exists in the git source input fields, which are not properly sanitized before being used in system commands.
See the full breakdown by country in Censys Platform →
| Field | Description |
| CVE-ID | CVE-2025-64424 — CVSS version 4.0 score: 9.4 — assigned by GitHubCVE-2025-64420 — CVSS version 3.1 score 9.9 — assigned by GitHubCVE-2025-64419 — CVSS Version 3.1 score: 9.7 — assigned by GitHub |
| Vulnerability Description | CVE-2025-64419:A command injection vulnerability that enables attackers to execute arbitrary system commands with elevated privileges. The vulnerability exists in the docker compose build pack, where parameters from docker compose files are not properly sanitized, and requires a victim user to create an application from an attacker-controlled repository.CVE-2025-64420:An information disclosure vulnerability that enables low-privileged users to access a private SSH key, allowing them to authenticate via SSH and potentially gain elevated privileges on the Coolify instance and underlying server.CVE-2025-64424:A command injection vulnerability that enables low-privileged users (members) to execute arbitrary system commands on the Coolify instance. The vulnerability exists in the git source input fields, which are not properly sanitized before being used in system commands. |
| Date of Disclosure | January 5, 2026 |
| Affected Assets | CVE-2025-64419: Docker compose build pack parametersCVE-2025-64420: Private SSH key exposureCVE-2025-64424: Git source input fields in resource configuration |
| Vulnerable Software Versions | CVE-2025-64419: Versions prior to v4.0.0-beta.445CVE-2025-64420: Versions prior to and including v4.0.0-beta.434CVE-2025-64424: Versions up to and including v4.0.0-beta.434 |
| PoC Available/ | A video supplied by GitHub demonstrates trivial command injection. |
| Exploitation Status | While widespread active attacks are not yet confirmed, the availability of a PoC and the trivial nature of the exploit make active exploitation highly likely in the near future. |
| Patch Status | CVE-2025-64419: Patch available. Version 4.0.0-beta.445 fixes the issue.CVE-2025-64420: Unclear if a patch is available.CVE-2025-64424: Unclear if a patch is available. |
Censys Perspective
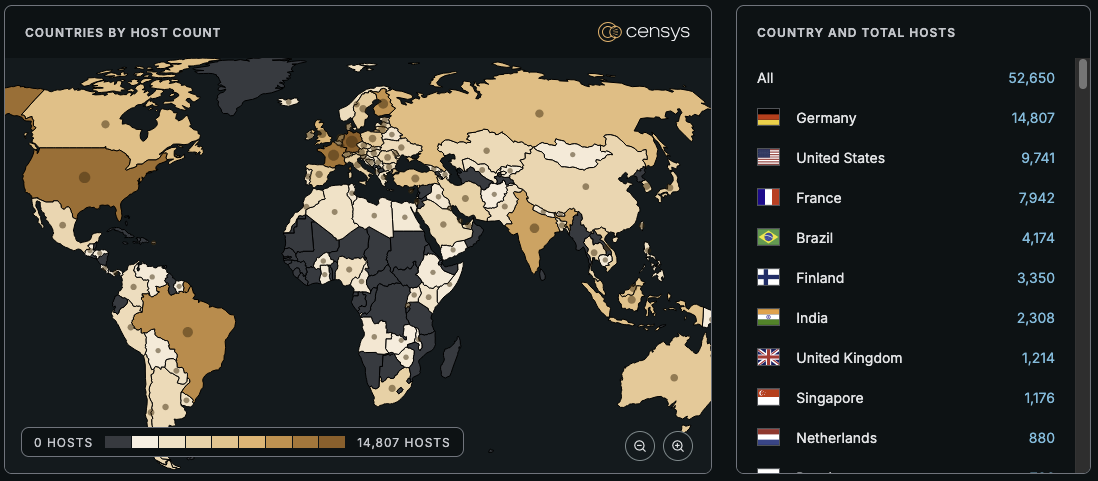
As of time of writing, Censys observes 52,650 exposed hosts, trackable with the following Censys queries:
(host.services.endpoints.http.html_title = “Coolify” or host.services.endpoints.http.headers: (key = “Set-Cookie” and value: “coolify_session=”) or host.services.endpoints.http.favicons.hash_md5 = “3108642c97cb27b075280a0860abb443”) or (web.endpoints.http.html_tags = “Coolify” or web.endpoints.http.headers: (key = “Set-Cookie” and value: “coolify_session”) or web.endpoints.http.favicons.hash_md5 = “3108642c97cb27b075280a0860abb443”)
ASM:
(host.services.http.response.html_title: “coolify” or host.services.http.response.headers: (key: “Set-Cookie” and value.headers: “coolify_session”) or host.services.http.response.favicons.md5_hash: “3108642c97cb27b075280a0860abb443”) or (web_entity.instances.http.response.headers: (key: “Set-Cookie” and value.headers: “coolify_session”) or web_entity.instances.http.response.html_title: “coolify” or web_entity.instances.http.response.favicons.hashes: “md5:e2c007eabf0fef0b2eb508d0350d9006”)
services.http.response.headers.Set_Cookie: “coolify_session” or services.http.response.html_title: “coolify” or services.http.response.favicons.hashes=”md5:e34e6be15d327d4a85c9fad467bc3f67″





