Executive Summary
AsyncRAT is an open-source .NET remote access trojan (RAT) implemented in C# and first released publicly in 2019. AsyncRAT has since become widely adopted by criminal operators for persistent remote access, surveillance, and data theft. The malware supports remote command execution, file transfer, keylogging, screen capture, and credential harvesting, typically communicating with command-and-control (C2) servers over a custom TCP protocol with traffic encrypted via SSL/TLS, often using self-signed certificates that may present CN=AsyncRAT Server.
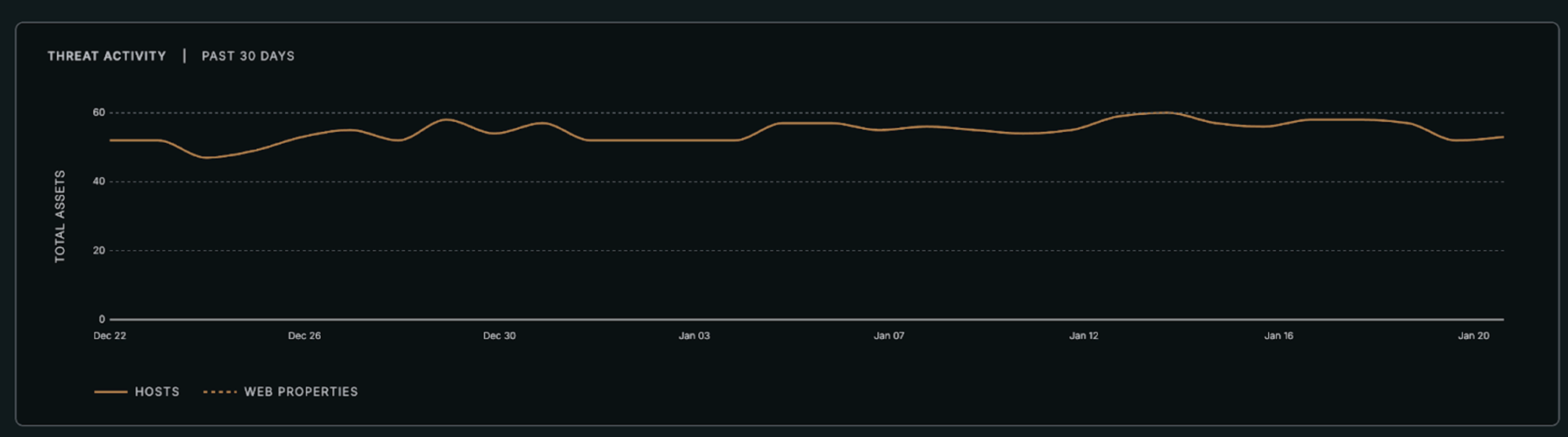
As of January 2026, Censys is tracking 57 active AsyncRAT-associated hosts exposed on the public internet. These hosts are primarily concentrated within a small number of VPS-focused autonomous systems and frequently reuse a distinctive self-signed TLS certificate identifying the service as an “AsyncRAT Server,” enabling scalable discovery of related infrastructure beyond sample-based detection.
Operationally, AsyncRAT enables long-lived unauthorized access and post-compromise control, making it a reliable tool for credential theft, lateral movement staging, and follow-on payload delivery.
Background
AsyncRAT was released publicly in 2019 by the developer known as NYAN-x-CAT and distributed via an open GitHub repository. Since its release, the codebase has been widely copied, modified, and redistributed across criminal communities, contributing to its persistent presence in commodity malware ecosystems.
The project has not undergone a formal rebrand in the way some families have, but it has spawned multiple closely related forks and derivatives, including DCRat (DarkCrystal RAT) and VenomRAT, which retain overlapping functionality and infrastructure patterns. This fragmentation complicates tracking when analysts rely solely on family names rather than shared technical artifacts.
AsyncRAT is most commonly delivered through malspam campaigns using compressed archives or document-based lures, as well as through loader chains that deploy the RAT as a secondary payload after initial execution. In some cases, AsyncRAT appears alongside other commodity tooling, enabling operators to blend its activity into high-volume background noise.
Capabilities
Once deployed, AsyncRAT provides operators with a broad set of post-compromise capabilities:
- Remote command execution and interactive shell access
- Credential theft via keylogging and memory access
- File upload, download, and arbitrary payload staging
- Persistence through scheduled tasks, registry run keys, or services
- Follow-on tooling deployment and lateral movement preparation
Technical Characteristics
AsyncRAT deployments exhibit several recurring technical traits observable across campaigns:
- Common filenames and artifacts: Though the AsyncRAT builder defaults to “AsyncClient.exe”, operators frequently use generic or misleading executable names, or masqueraded system binaries; registry-based persistence commonly leverages standard Run key locations.
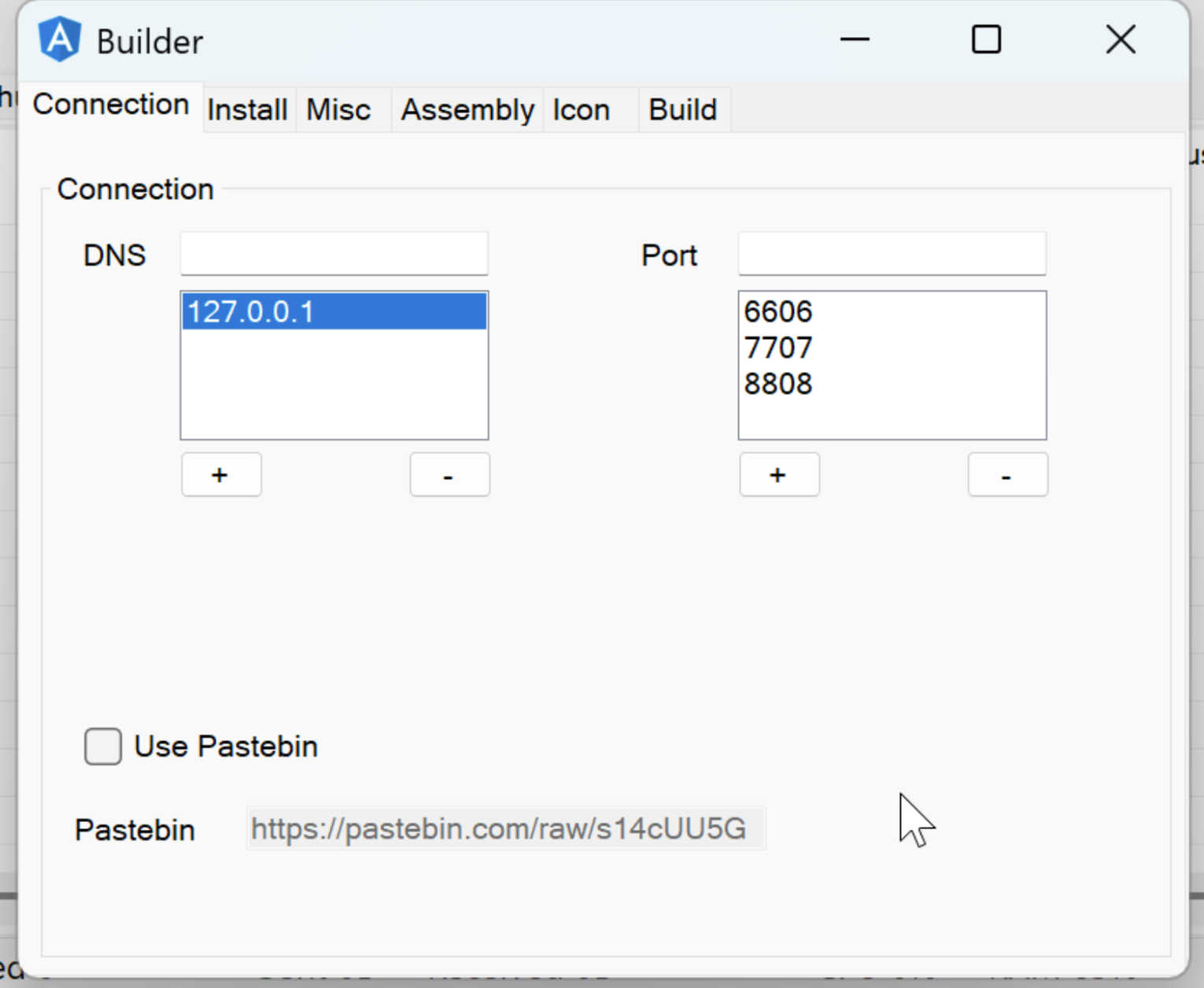
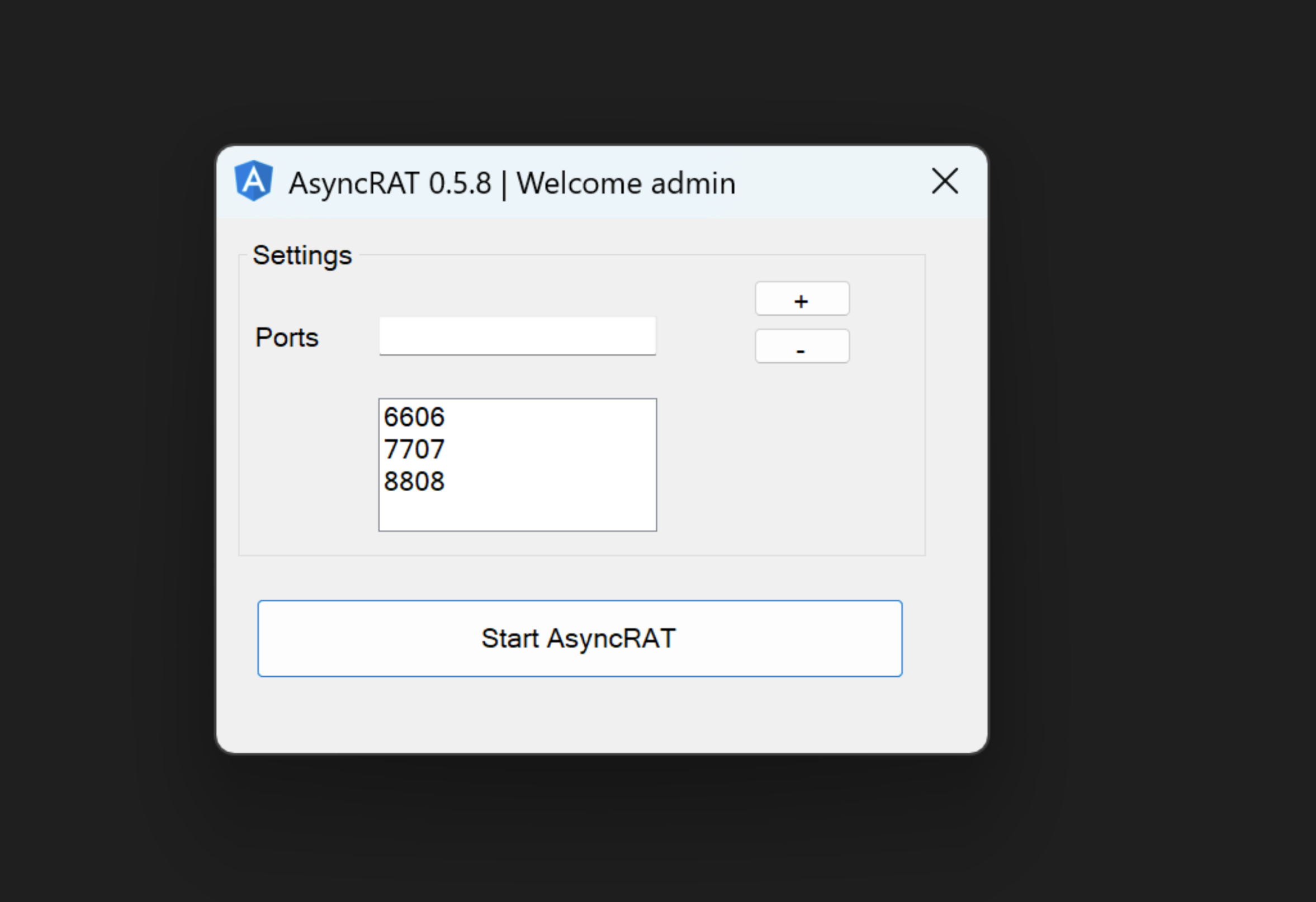
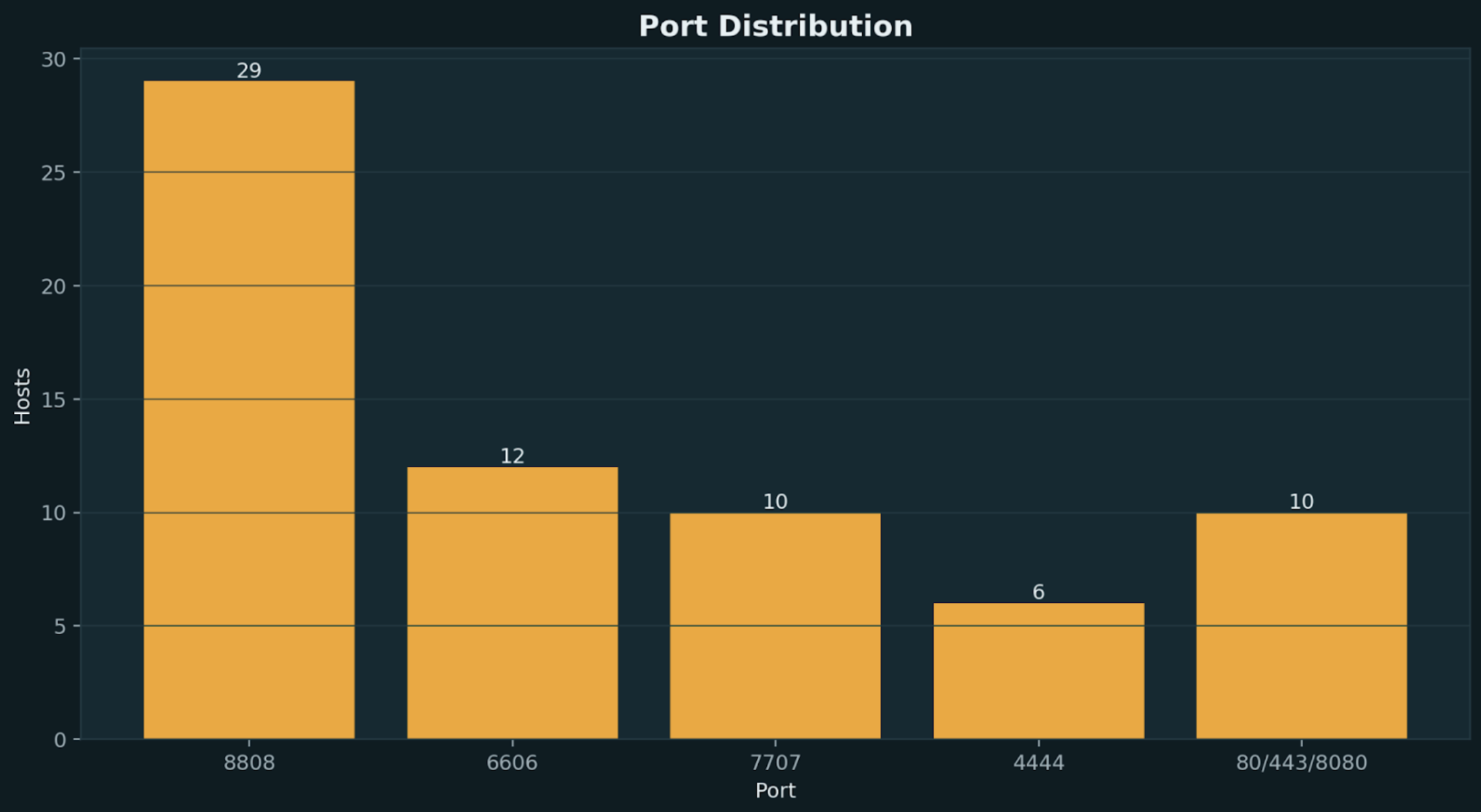
- Network behavior: AsyncRAT typically communicates with C2 servers over a custom TCP protocol, often exposed on non-standard ports such as 8808, 6606, and 7707, rather than embedding traffic within common application protocols
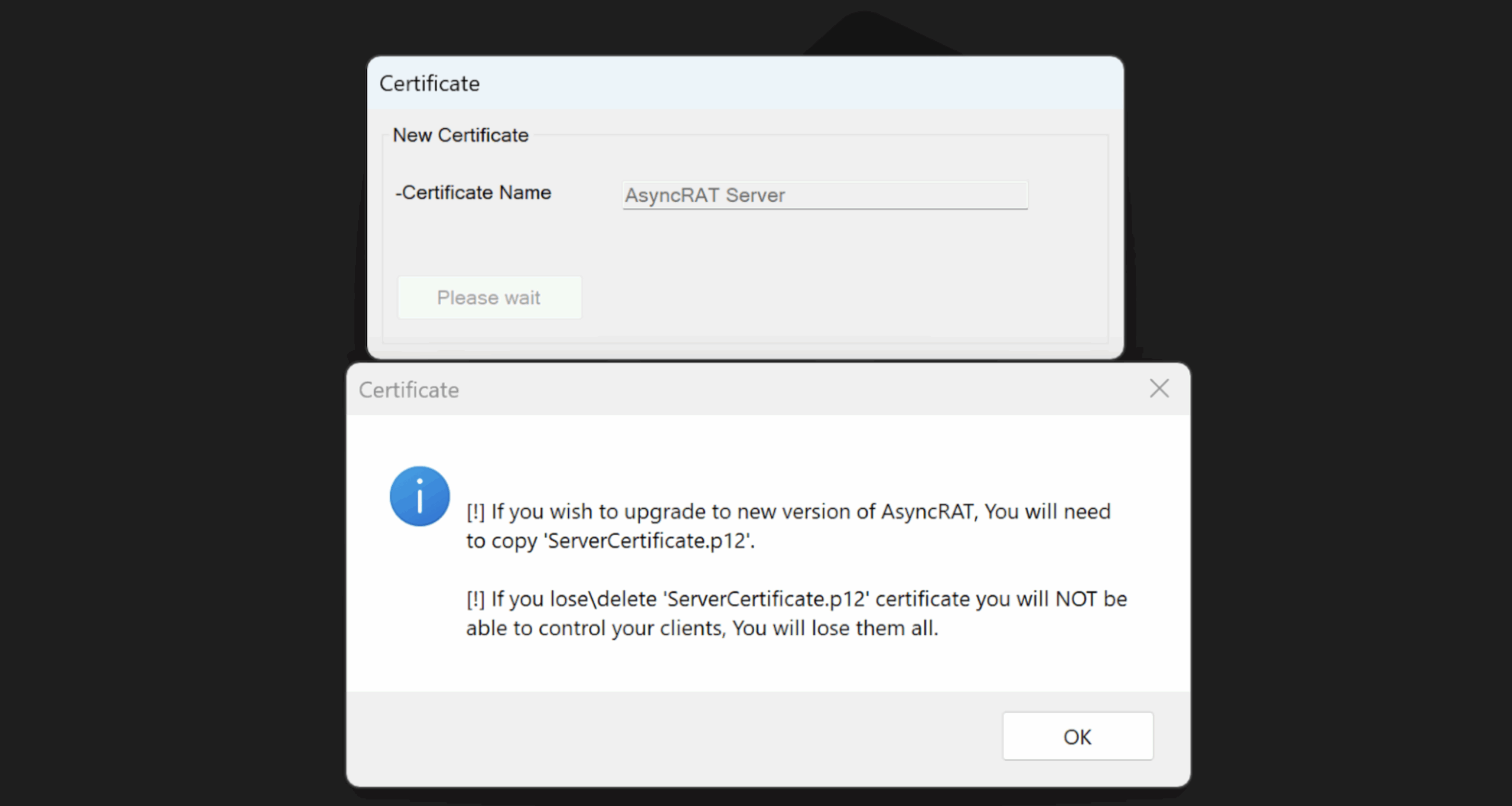
- TLS characteristics: Many deployments wrap C2 traffic in SSL/TLS using self-signed certificates, frequently presenting a common name such as “AsyncRAT Server”
Operational Context
AsyncRAT remains relevant due to its low barrier to entry, ease of customization, and continued reuse across a wide range of operators. While often associated with opportunistic campaigns, its infrastructure and tooling have also appeared in more targeted activity, underscoring how commodity RATs continue to serve as building blocks for diverse threat models. Reuse of distinctive TLS artifacts and concentration within a limited set of VPS providers further amplifies its visibility at internet scale.
The following section summarizes Censys visibility into infrastructure and prevalence trends associated with AsyncRAT.
Censys Perspective
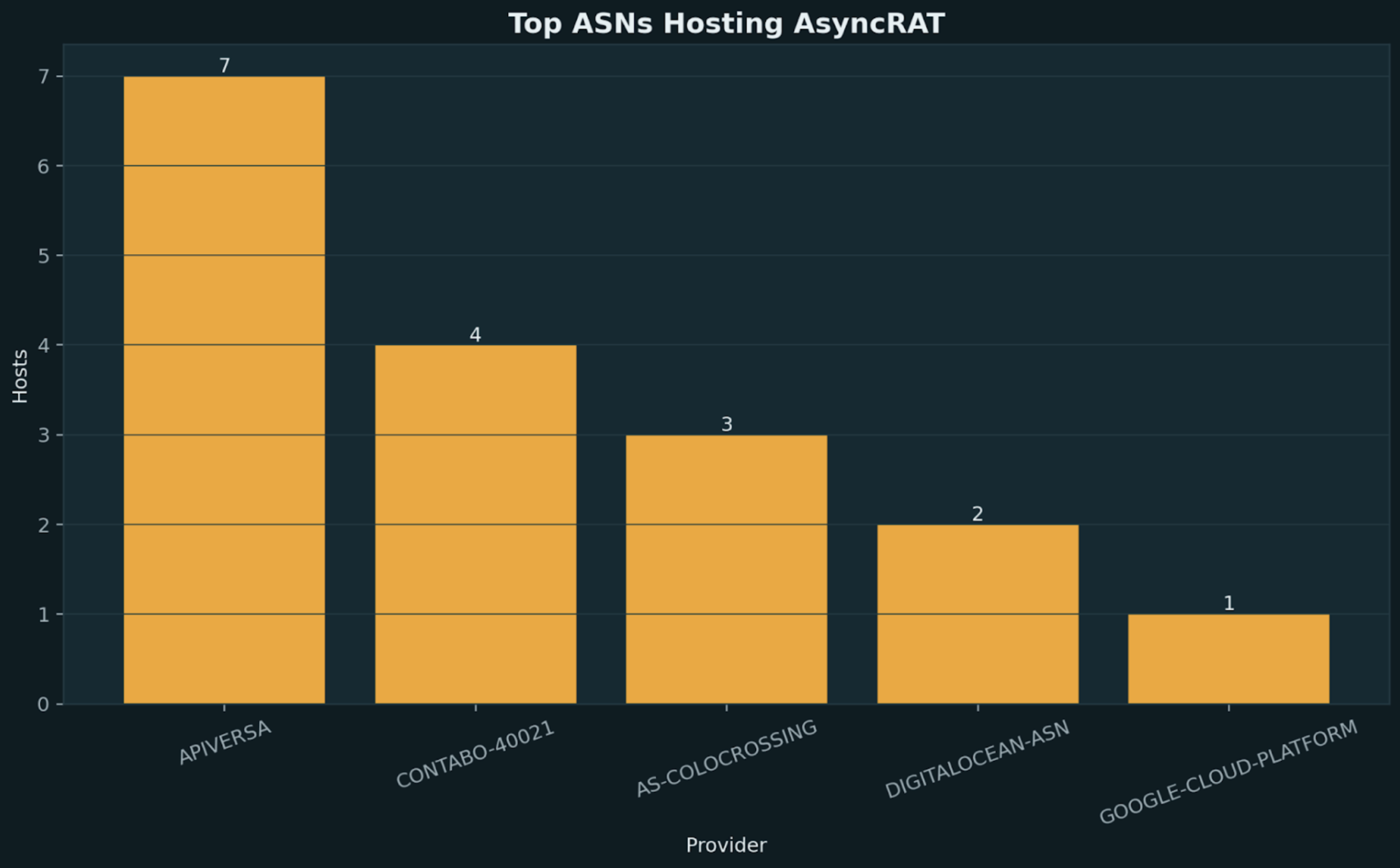
Out of the 57 total assets hosting AsyncRAT, we analyzed how they were distributed across infrastructure and found evidence of a decentralized hosting strategy favoring budget VPS providers and resellers. The dominance of APIVERSA (13% of hosts), Contabo networks (11% combined), and AS-COLOCROSSING (5.5%) indicates operators prioritize low-cost, abuse-tolerant hosting over major cloud providers.
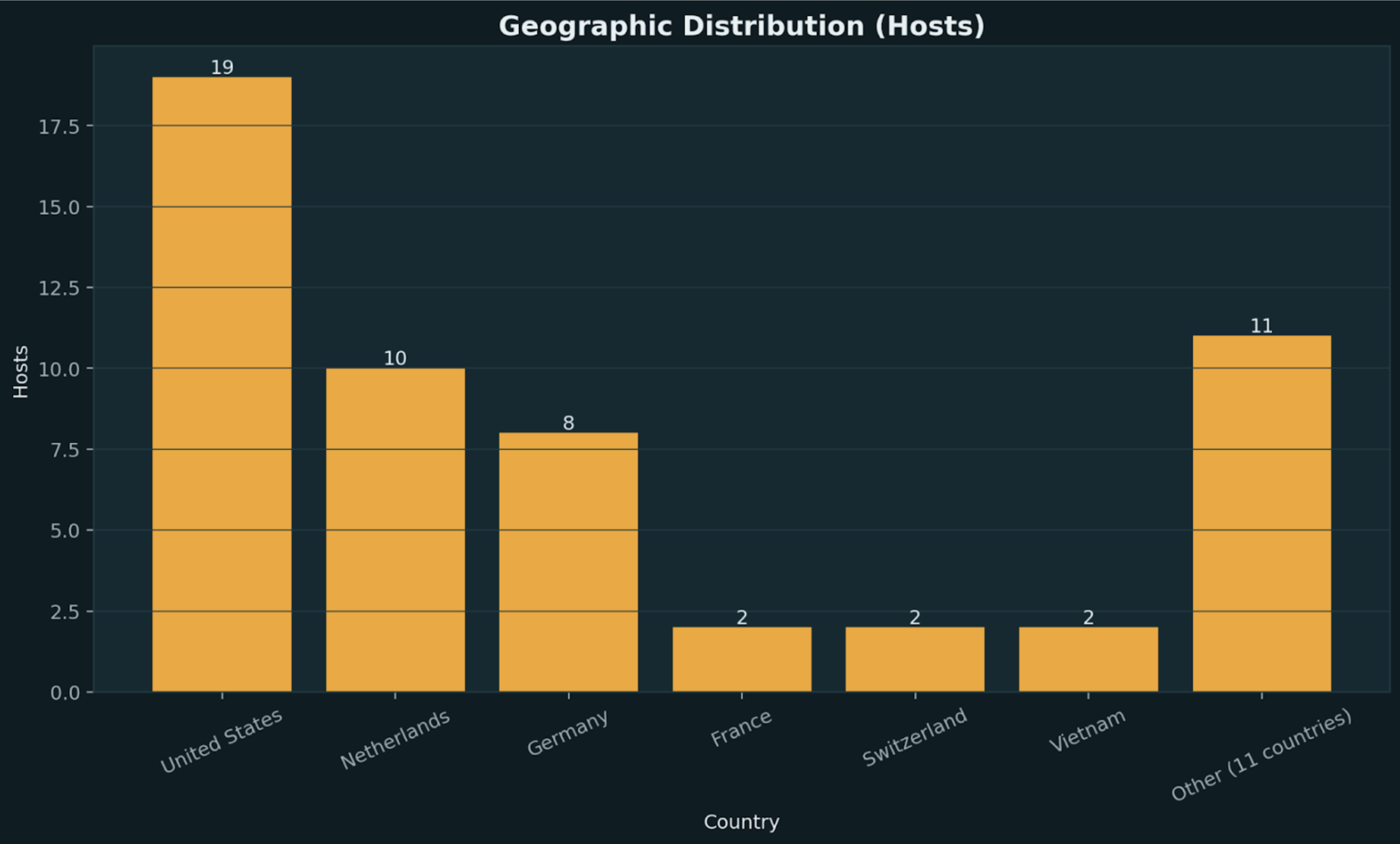
Geographic concentration in the US, Netherlands, and Germany aligns with data center density in these regions rather than operator location.
The near-universal use of the default “AsyncRAT Server” certificate (98%) suggests operators are deploying unmodified or lightly customized versions of the RAT, creating a highly reliable detection pivot.
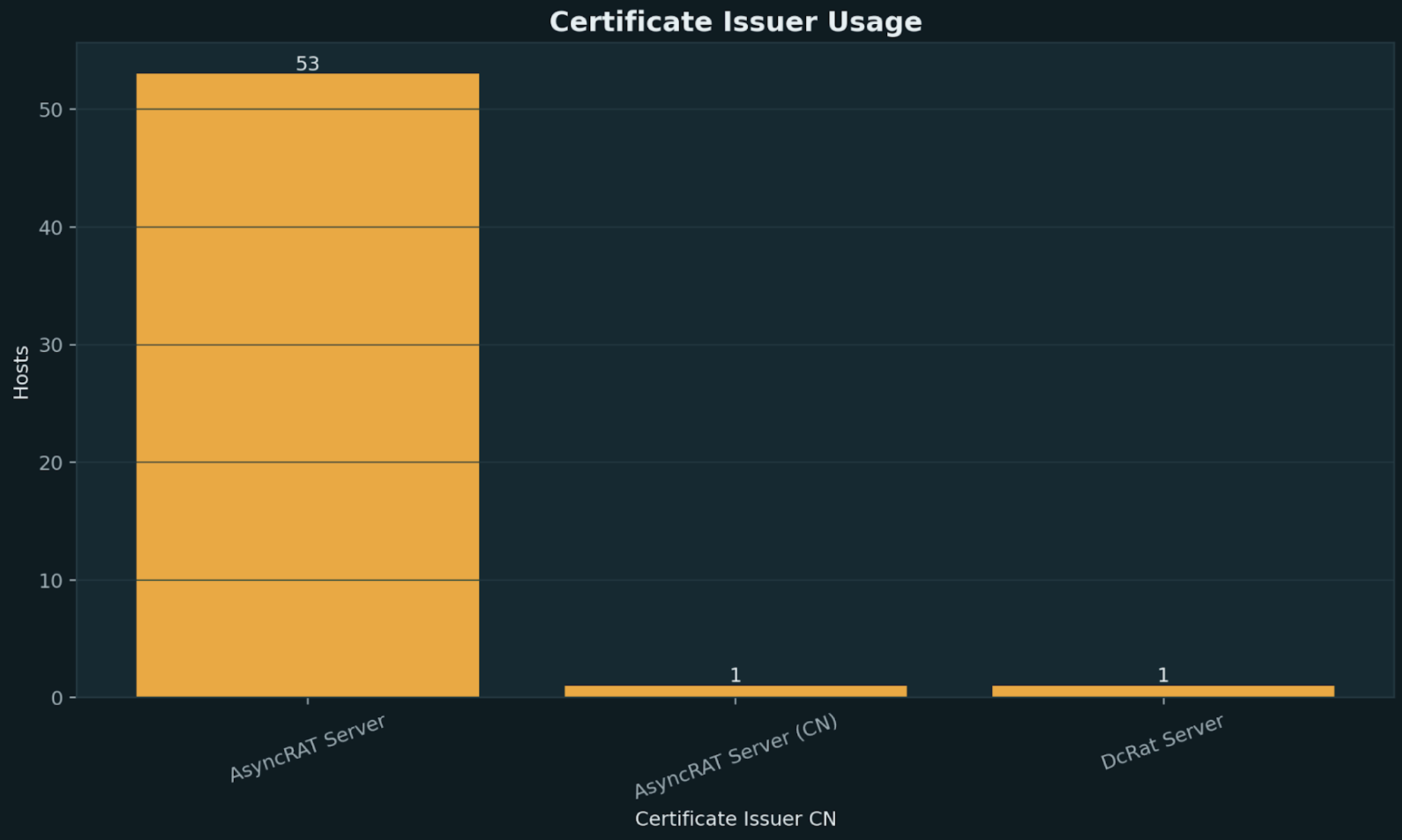
Multiple hosts running 3-5 AsyncRAT instances on sequential ports (e.g., 185.196.9.158 with ports 4501-4504) indicate either multi-campaign infrastructure or redundancy configurations.
Case Study
Another approach to hunting AsyncRAT with Censys Platform is to go after exposed clients. By searching for the known default name of the AsyncRAT client (AsyncClient.exe) we are able to discover AsyncRAT samples staged in Open Directories using the Censys Open Directory details view.
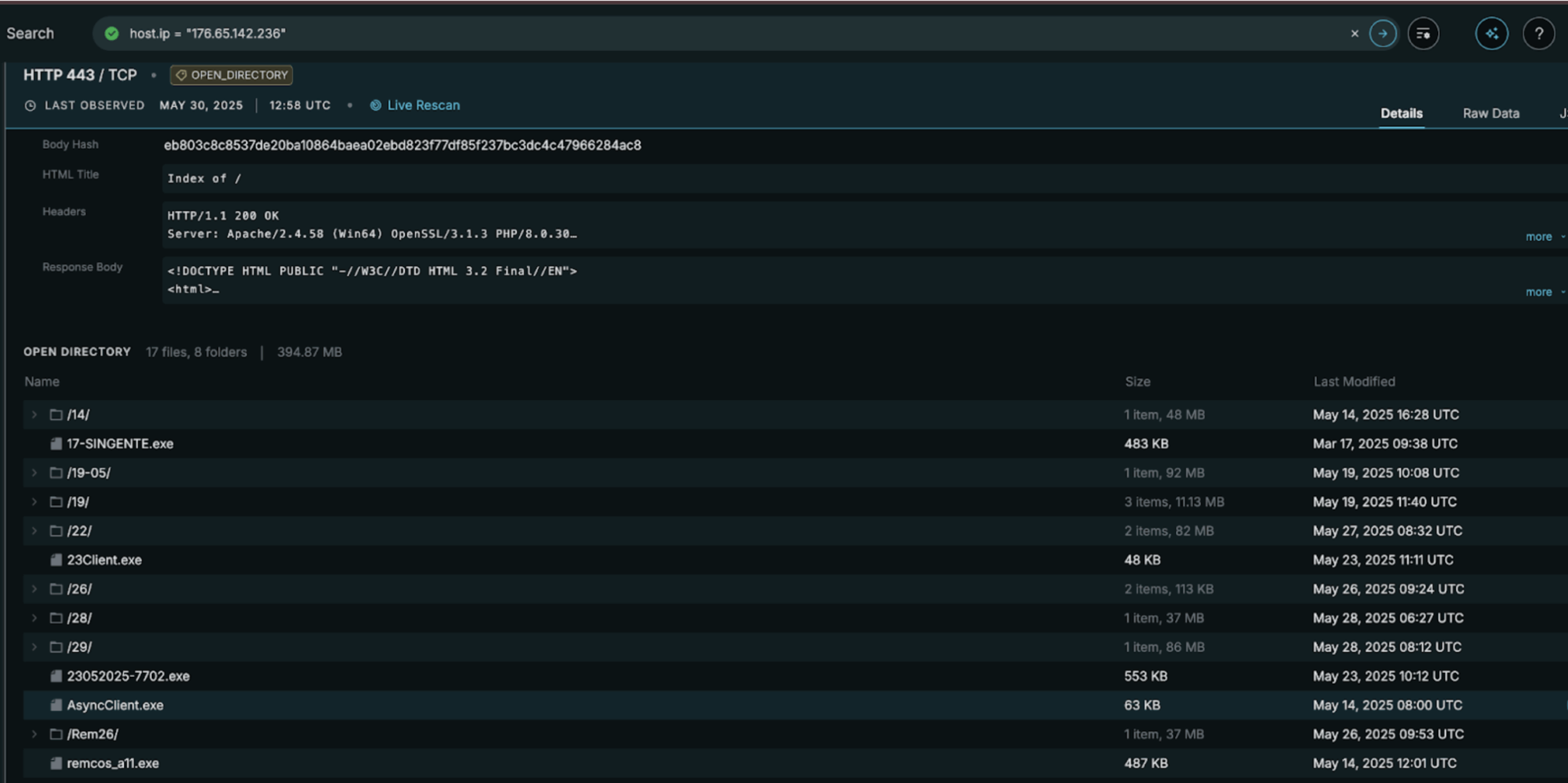
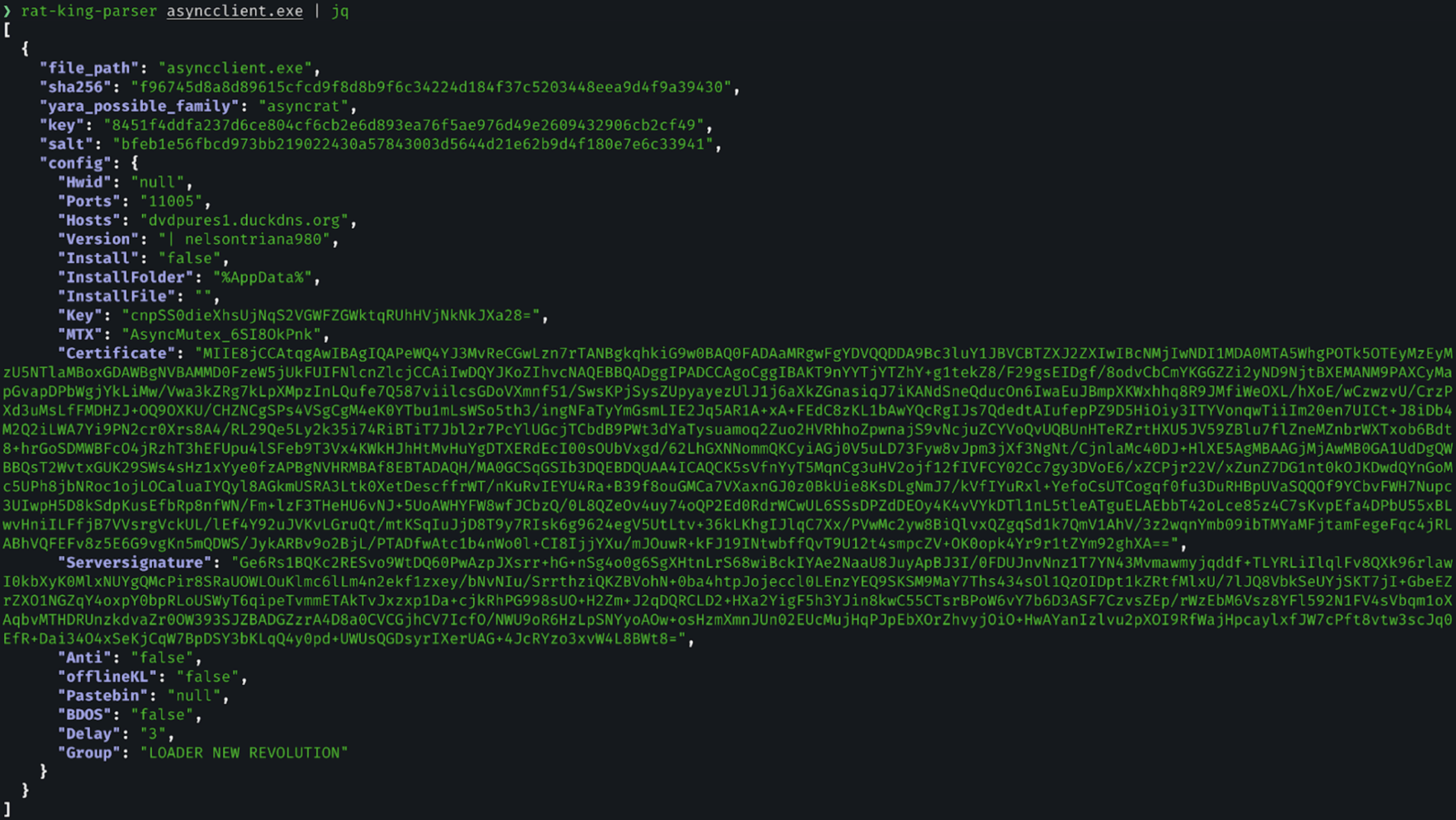
Static analysis confirms the payload is AsyncRAT. The sample implements the canonical AsyncRAT client architecture, including MessagePack-encoded command routing using a top-level Packet field, a plugin-based execution model that dynamically loads compressed assemblies in memory and invokes a standardized Plugin.Plugin.Run() entrypoint, and an AES-encrypted configuration schema containing the standard AsyncRAT fields (Hosts, Ports, MTX, Install, BDOS, Pastebin, Group). The client initializes a self-signed TLS channel using an embedded X.509 certificate whose decrypted subject is “AsyncRAT Server”, and passes that certificate directly into the client socket and plugin runtime.
To disambiguate between AsyncRAT and VenomRAT (which shares much of the original codebase) we searched for VenomRAT-specific modules. No VenomRAT-specific modules or configuration expansions (e.g., HVNC, clipper, Telegram control) were observed, supporting classification as AsyncRAT rather than a VenomRAT fork.
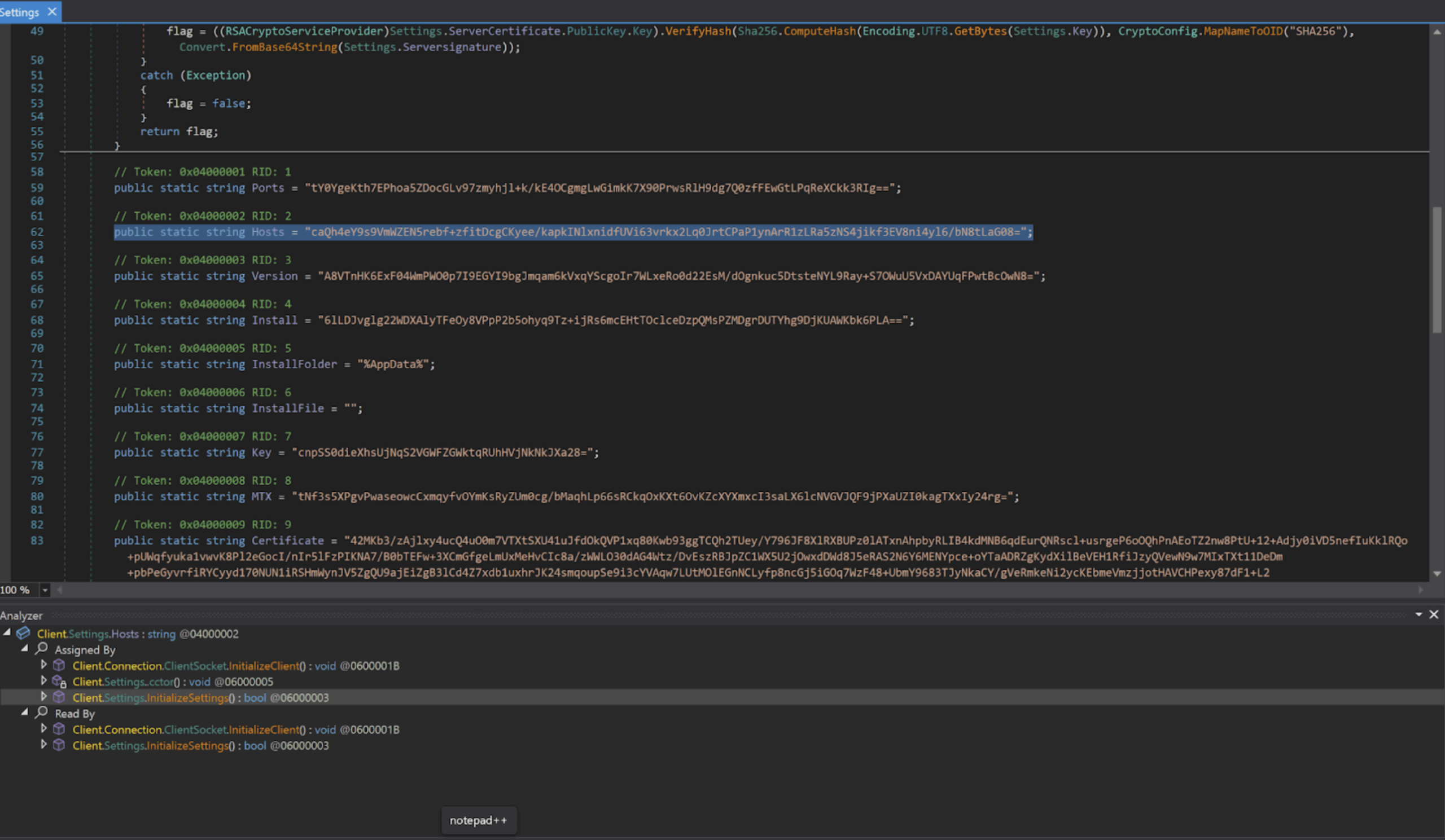
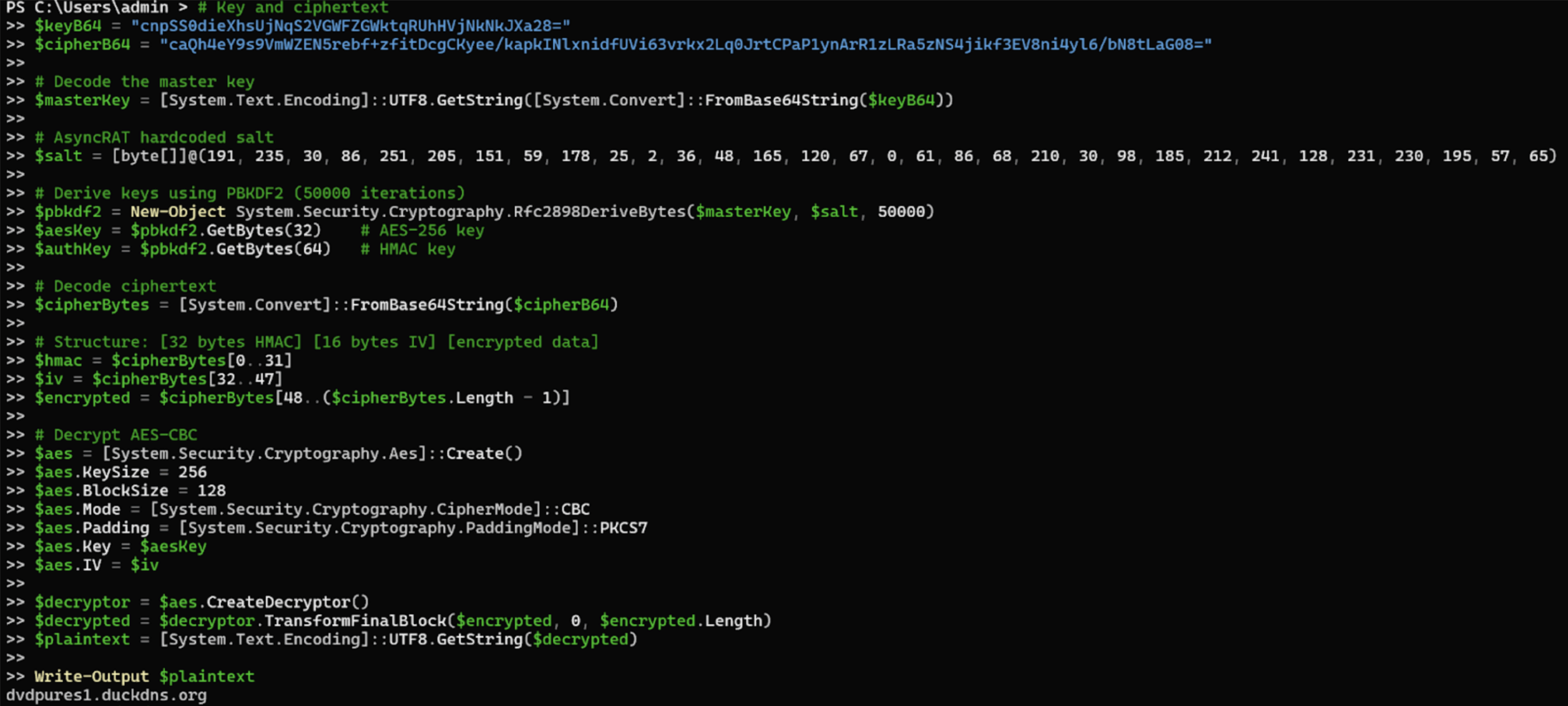
Notable Findings
The presence of a Chinese-localized certificate variant (“AsyncRAT 服务器”) and a “bullet-proof” hostname in certificate data indicates geographic expansion of operator demographics beyond the typical Eastern European and Latin American threat actor communities historically associated with AsyncRAT.
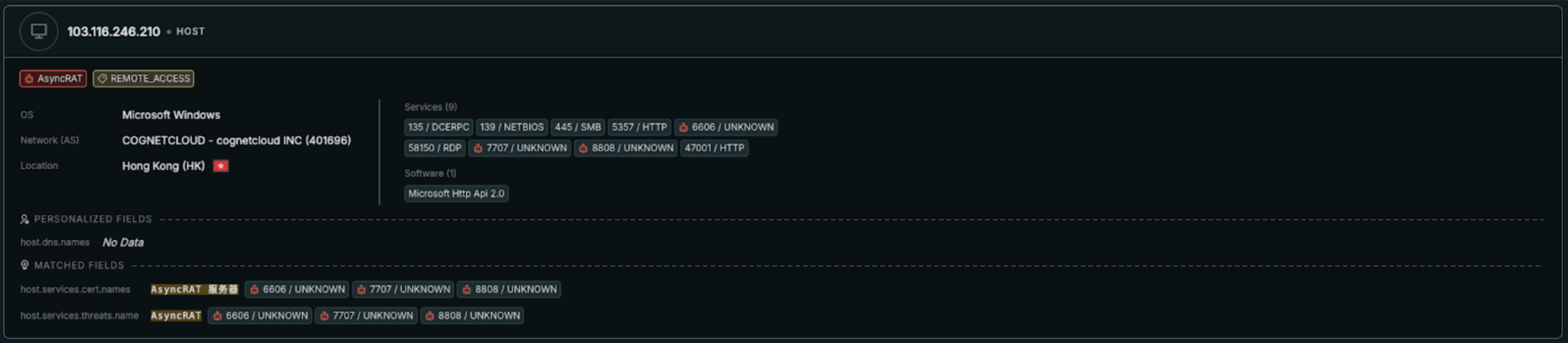
These infrastructure patterns inform how defenders can prioritize detection and blocking, detailed in the following section.
Conclusion (Implications for Defense)
AsyncRAT’s credential theft capabilities (keylogging, browser password recovery, clipboard hijacking) combined with its persistent access mechanisms (scheduled tasks, registry persistence) make it a high-value threat for network-based detection and credential hygiene efforts.
Detection Strategies
Host-Based Detection:
- Unexpected scheduled task creation referencing %APPDATA% or %TEMP% paths
- Registry Run key additions with obfuscated executable names
- Windows administrative services (RDP, WinRM, SMB) exposed on internet-facing hosts
- Process execution from unusual paths mimicking legitimate Windows processes
- PowerShell or .NET execution with AMSI bypass indicators
Network-Based Detection:
- TLS connections to servers presenting certificates with CN=AsyncRAT Server or CN=AsyncRAT 服务器
- Certificate fingerprint 136fbfd2d255a7fc69c16fe115138d7a53ed0a7db8302017ee0e692b42d82ffe
- Connections to ports 8808, 6606, 7707 with encrypted traffic patterns
- JA3/JARM fingerprints consistent with .NET TLS implementations
- DNS queries to known C2 domains
Blocking Recommendations:
- Leverage the Censys Threat Hunting Platform to identify and disrupt infrastructure linked to AsyncRAT. Run the provided queries regularly and alert on any outbound communications matching these patterns.






