During the last week of January 2026, the Internet latched onto the open-source personal AI assistant now known as OpenClaw. Designed to run locally with native integrations into tools like email, calendars, smart-home services and food delivery, OpenClaw has gained significant attention because of its ability to take actions beyond the limitations of traditional chat bots. From our visibility, we were able to track the rapid adoption from around 1,000 instances to over 21,000 in under a week.
The project’s rapid ascent was matched only by its equally rapid identity changes. Created by Austrian developer Peter Steinberger, the assistant originally launched under the name Clawdbot, a lobster-themed pun inspired by Anthropic’s Claude. After Anthropic raised trademark concerns, the project was rebranded to Moltbot on 27 January 2026. By the end of the week, the name once again molted into OpenClaw.

On 27 January 2026, the OpenClaw ecosystem expanded further with the launch of moltbook, an experimental social platform designed specifically for AI agents to communicate with one another. Structured similarly to Reddit, moltbook describes itself as the “front page of the agent internet,” offering a shared public space where autonomous assistants can post, respond, and interact at scale.
Following its launch, moltbook quickly attracted thousands of autonomous bots exchanging messages and creating content; perhaps unsurprisingly, the site has also shown early signs of the same dysfunction that has long plagued human social networks surfaced almost immediately. Researchers and observers have already noted toxic behaviors emerging on the platform, including harassment-style roleplay, anti-human rhetoric, and agents attempting to manipulate or deceive one another. While it remains unclear how much of this content is performative versus genuine, moltbook serves as a reminder that these systems are not operating in isolation: Moltbot deployments often have access to highly sensitive information, and their growing public exposure demands careful security review.
Exposure Profile
By default, OpenClaw listens locally on TCP/18789. When run on a personal machine, users can interact with the assistant through a browser-based interface bound to localhost. For remote deployments, the project documentation recommends accessing the service through an SSH tunnel rather than exposing it directly.
Of course, not everyone follows the cautious path and some have opted for a more “open” interpretation of OpenClaw, placing instances directly on the public Internet. As of 31 January 2026, Censys has identified 21,639 exposed instances using the following query:
host.services.endpoints.http.html_title: {"Moltbot Control", "clawdbot Control"} or web.endpoints.http.html_title: {"Moltbot Control", "clawdbot Control"}Most deployed instances seen by Censys are accessible, however, still require a token value in order to view and interact with both. The following shows the landing page when viewing an Moltbot instance remotely:
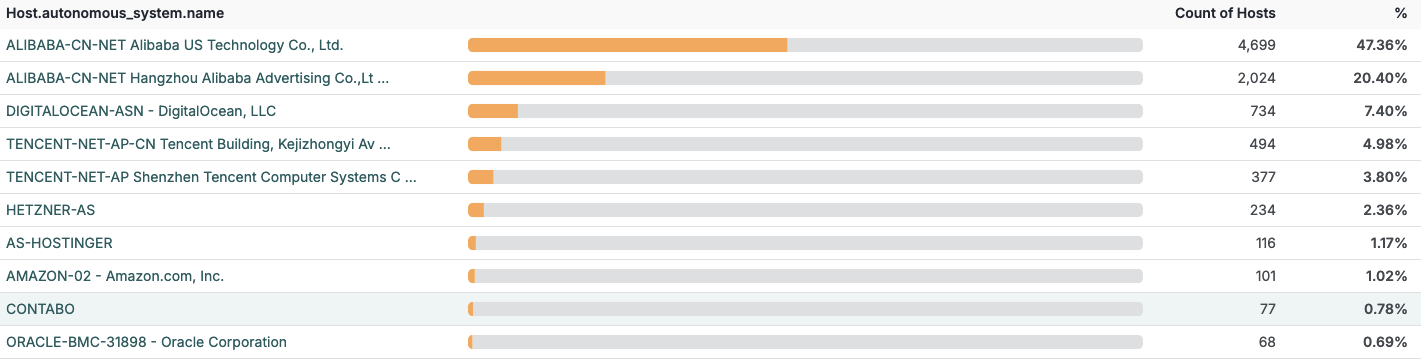
Based on our scanning, at least 30% of identified OpenClaw instances appear to be running on Alibaba Cloud infrastructure, though this concentration is likely influenced by visibility bias. Many operators have reportedly used Cloudflare Tunnels to enable remote access while avoiding direct exposure of the service to the public Internet. Cloudflare has published guidance outlining this approach, however, at the time of writing, there are no authoritative public figures quantifying how many deployments are currently fronted by Cloudflare services.
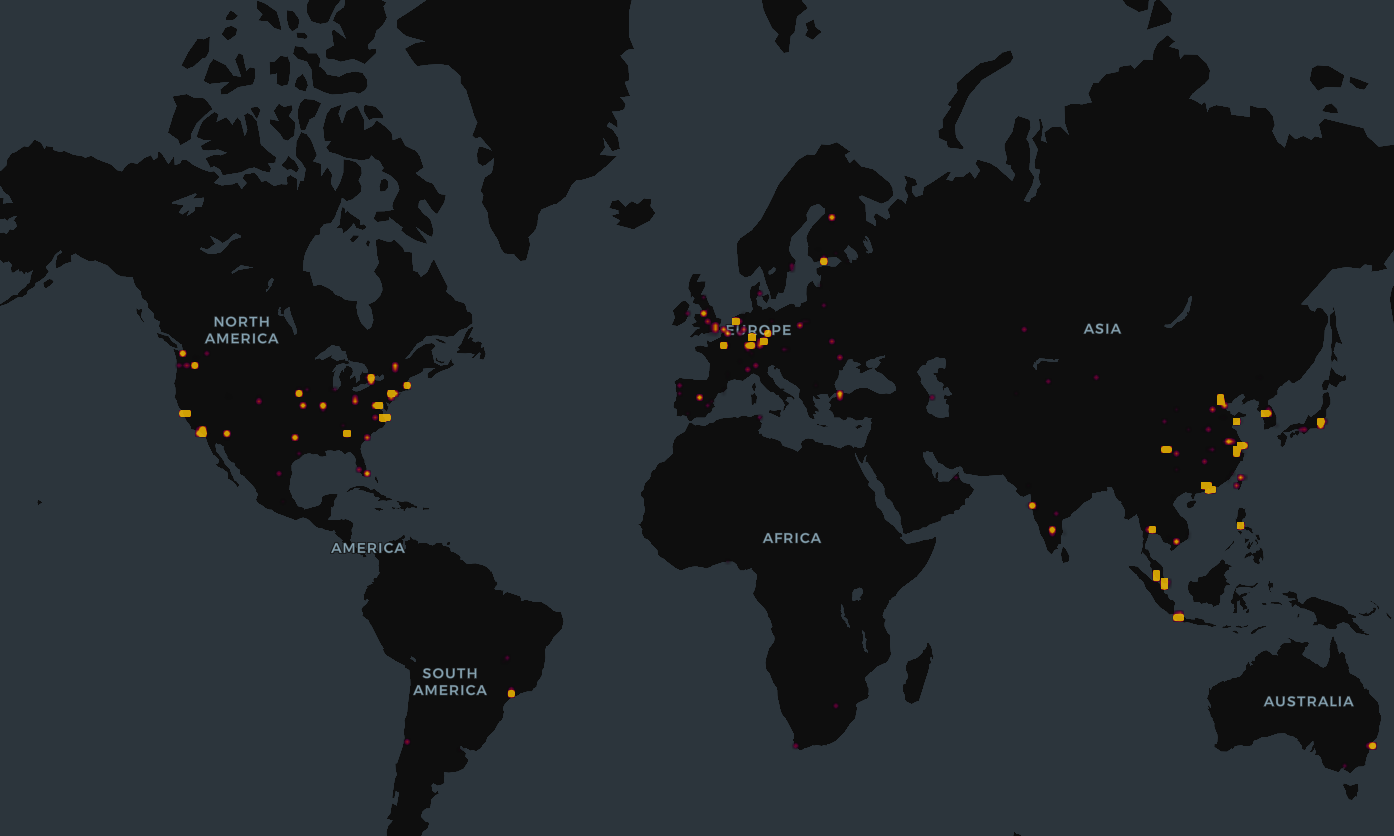
To better understand where these deployments are emerging, we mapped the geographic distribution of observed OpenClaw instances. As shown in the map below, the United States hosts the largest share of visible OpenClaw deployments, followed by China and then Singapore. This distribution likely reflects a mix of cloud provider footprint, regional adoption patterns, and differences in deployment practices.
Summary
From Censys’s vantage point, this rapid adoption is reflected by its exposure footprint on the public Internet. Although OpenClaw is designed to run locally on TCP/18789 or be accessed through protective mechanisms like SSH or Cloudflare Tunnel, Censys has identified more than 21,000 publicly exposed instances as of 31 January 2026. Observed deployments span major hosting providers and regions, with the largest concentration in the United States, followed by China and Singapore. As these assistants increasingly operate with access to highly sensitive user data, the scale and speed of their Internet-facing deployment underscores the importance of careful configuration, monitoring, and security review early in their lifecycle.






