Date of Disclosure (source): February 26, 2025
Date Reported as Actively Exploited (source): March 19, 2025
CVE-2024-48248 is an arbitrary file read vulnerability affecting NAKIVO Backup & Replication before 11.0.0.88174, with a CVSS score of 8.6. If successfully exploited, it allows a threat actor to read arbitrary files from the victim’s server, potentially including credentials and backup files.
NAKIVO Backup & Replication is used to backup and restore data from a variety of sources. The NAKIVO Director is the central management HTTP interface and is typically deployed on 4443/TCP.

Researchers from Watchtowr Labs published a technical writeup detailing how attackers can exploit this vulnerability to read arbitrary files by sending specially crafted HTTP requests to the /c/router endpoint. The exploit leverages the endpoint’s handling of action and method parameters, which map to Java classes and methods that execute within the NAKIVO service’s context. Their proof of concept exploit code is available here.
This vulnerability is known to be actively exploited and was added to CISA’s list of known exploited vulnerabilities (KEV) on March 19, 2025. This vulnerability was patched in version 11.0.0.88174, as confirmed by researchers at Watchtowr Labs. Please see the release notes from the vendor for more information.
| Field | Details | |||||
|---|---|---|---|---|---|---|
| CVE-ID | CVE-2024-48248 – CVSS 8.6 (high) – assigned by MITRE | |||||
| Vulnerability Description | NAKIVO Backup & Replication before 11.0.0.88174 allows absolute path traversal for reading files via getImageByPath to /c/router (this may lead to remote code execution across the enterprise because PhysicalDiscovery has cleartext credentials). | |||||
| Date of Disclosure | February 26, 2025 | |||||
| Affected Assets | getImageByPath to /c/router endpoint of the NAKIVO Backup & Replication Director interface before 11.0.0.88174. | |||||
| Vulnerable Software Versions | NAKIVO Backup & Replication before 11.0.0.88174. | |||||
| PoC Available? | A PoC exploit published by Watchtowr Labs is available here. | |||||
| Exploitation Status | This vulnerability is known to be actively exploited and was added to CISA KEV on March 19, 2025. | |||||
| Patch Status | This vulnerability was patched in version 11.0.0.88174. See the release notes from the vendor for more information. | |||||
Censys Perspective
At the time of writing, Censys observed 356 of exposed NAKIVO Backup & Replication instances online. 203 of these hosts exposed a version that is vulnerable to this exploit. The following vulnerable versions were observed most commonly:
| Version | Host Count |
|---|---|
| 10.8.0.73174 | 40 |
| 10.5.1.61510 | 30 |
| 10.11.2.83985 | 26 |
| 10.11.0.80830 | 24 |
| 10.11.3.86675 | 18 |
| 10.11.3.86570 | 15 |
| 10.8.0.71786 | 6 |
| 10.7.2.69768 | 5 |
| 10.4.1.59587 | 4 |
| 10.9.0.76010 | 4 |
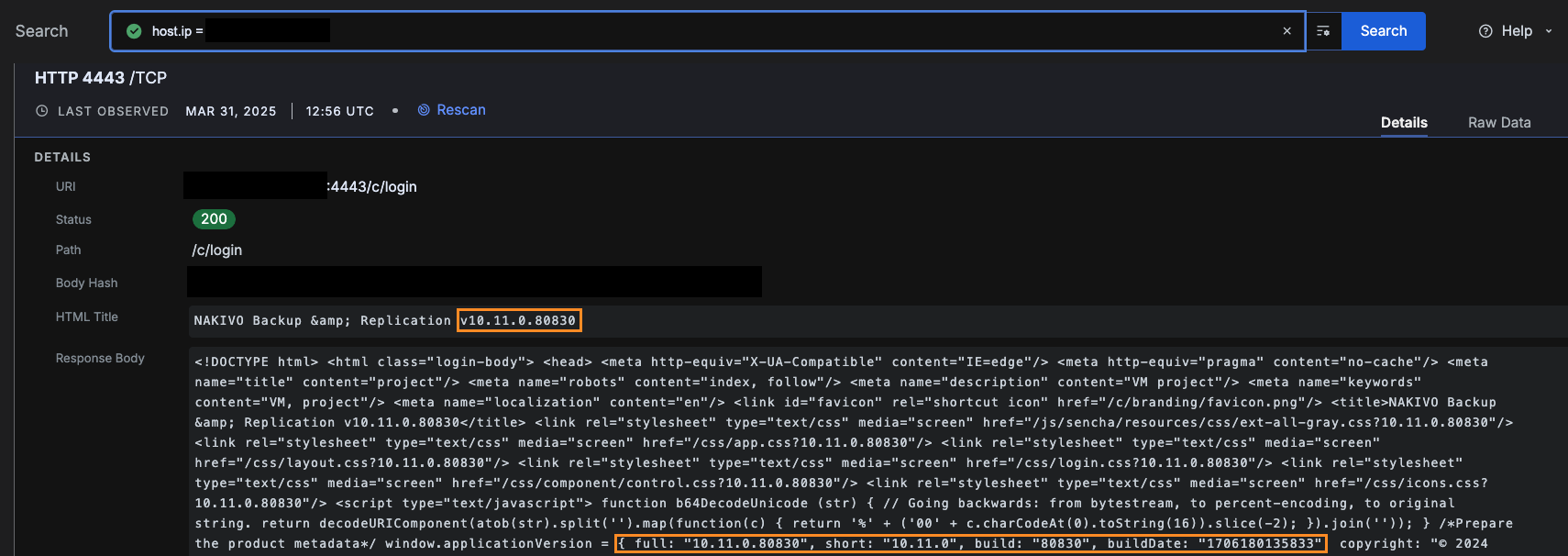
Exposed version information was observed in either the HTML title or HTML body of the page:
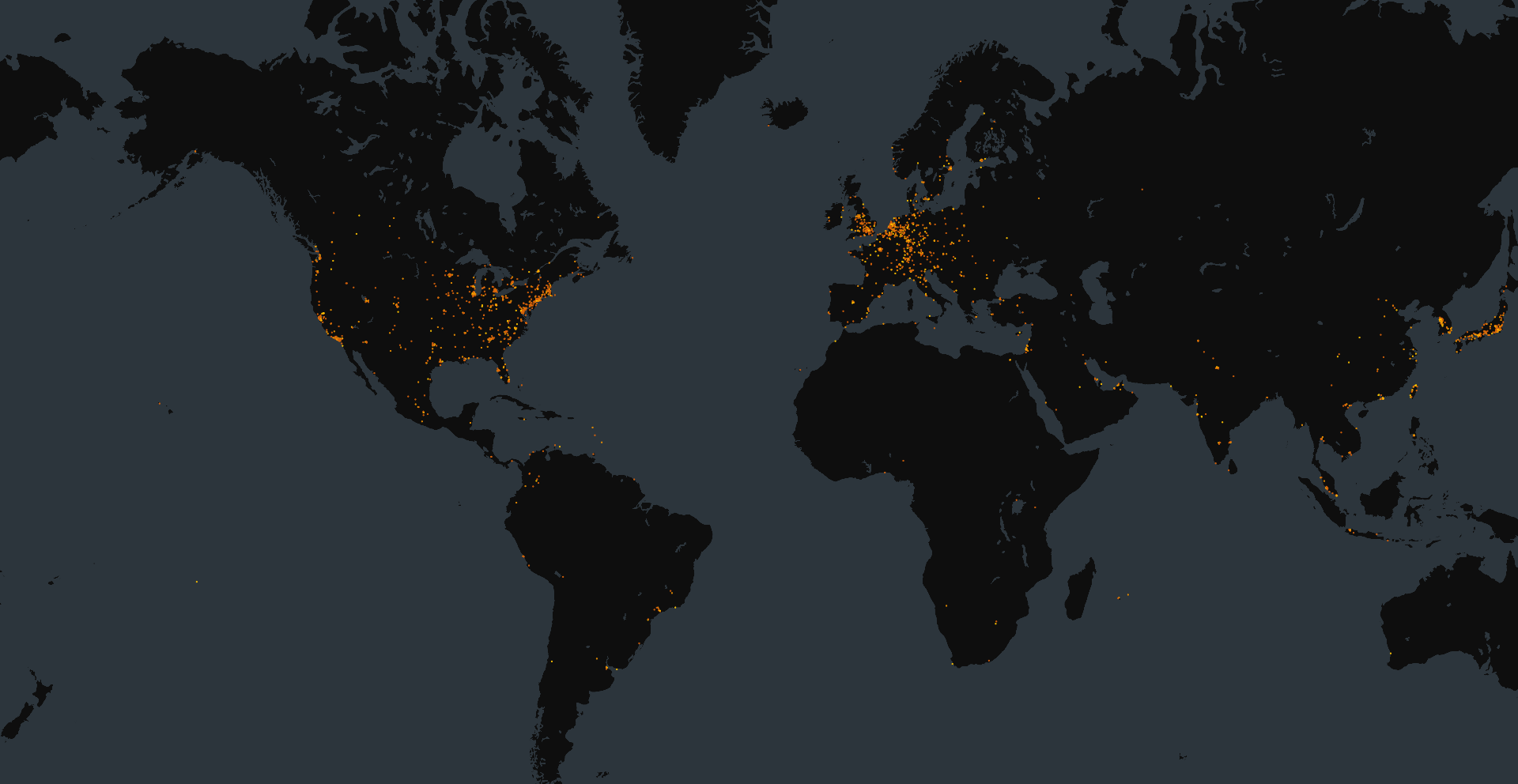
Map of Exposed Vulnerable NAKIVO Backup & Replication Instances:
The queries below can be used to identify exposed instances of NAKIVO Backup & Replication, but they are not necessarily vulnerable to the exploit.
Censys Platform Query:
host.services.software: (vendor: “nakivo” and product: “backup_&_replication”)
Censys Search Query:
services.software: (vendor=”NAKIVO” and product=”Backup & Replication”)
Censys ASM Query:
host.services.software: (vendor= “NAKIVO” and product= “Backup & Replication”)
The query below can be used to identify exposed instances of NAKIVO Backup & Replication that are vulnerable to the exploit.
Risk:
risks.name = “Vulnerable NAKIVO Backup & Replication [CVE-2024-48248]”





