Vulnerability Description
SAP NetWeaver AS Java (Deploy Web Service) has a file upload flaw allowing a user authenticated as a non-administrative/low-privileged account to upload arbitrary files. If the uploaded file can be executed (e.g., due to weak validation of file type or insufficient access control), this may lead to full compromise of confidentiality, integrity, and availability of the system.
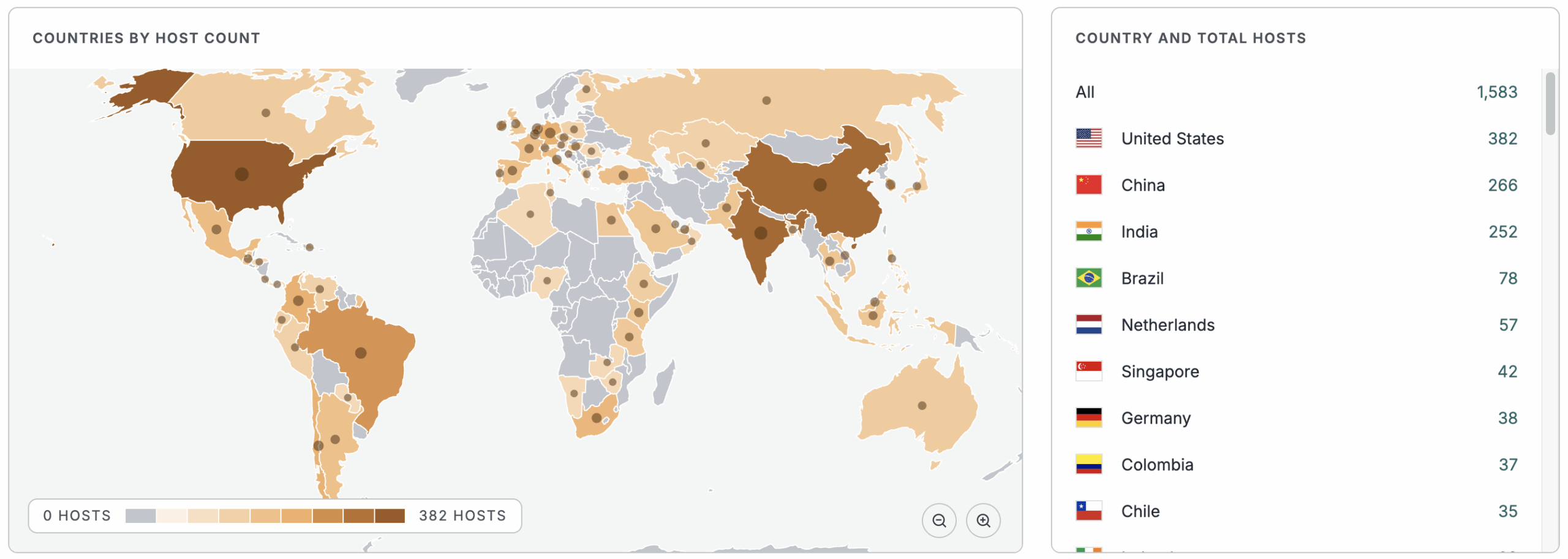
View the full geographic breakdown in Censys Platform –>
| Field | Description |
| CVE-ID | CVE-2025-42922 — CVSS 9.9 (Critical) — Assigned by SAP SE |
| Vulnerability Description | A file upload flaw in SAP NetWeaver AS Java allows a user authenticated as a non-administrative user to upload an arbitrary file. When executed, this file can lead to a full compromise of confidentiality, integrity and availability of the system. |
| Date of Disclosure | September 8, 2025 |
| Affected Assets | SAP NetWeaver AS Java (specifically the Deploy Web Service endpoint) |
| Vulnerable Software Versions | J2EE-APPS 7.50 |
| PoC Available? | As of writing, no public proof-of-concept exploit has been released. |
| Exploitation Status | As of writing, no active exploits have been publicly identified. |
| Patch Status | Apply SAP Security Note 3643865 from SAP’s September 2025 Patch Day.Workarounds:Limit access to the Deploy Web Service so only necessary, trusted users can invoke it. RedRays – Your SAP Security Solution+1Audit upload paths, log and monitor file-upload events from non-admin accounts. ZeroPath+1Validate and sanitize file types/content; ensure uploaded files are not stored in locations where they can be executed unless absolutely necessary. |
Censys Perspective
The following queries can help identify potentially affected assets:
host.services.software: (product = “netweaver_application_server_java” and version=7.50)
risks.name=”Vulnerable SAP NetWeaver AS Java [CVE-2025-42922]”
services.software: (product = “NetWeaver Application Server Java” and version=7.50)
References
- https://www.cve.org/CVERecord?id=CVE-2025-42922





