Vulnerability Description
CVE-2025-10035 is a deserialization vulnerability in the License Servlet of Fortra’s GoAnywhere MFT that allows an attacker with a forged license response signature to deserialize arbitrary objects, potentially leading to command injection. Exploitation requires the system to be publicly accessible, which is common for GoAnywhere MFT deployments.
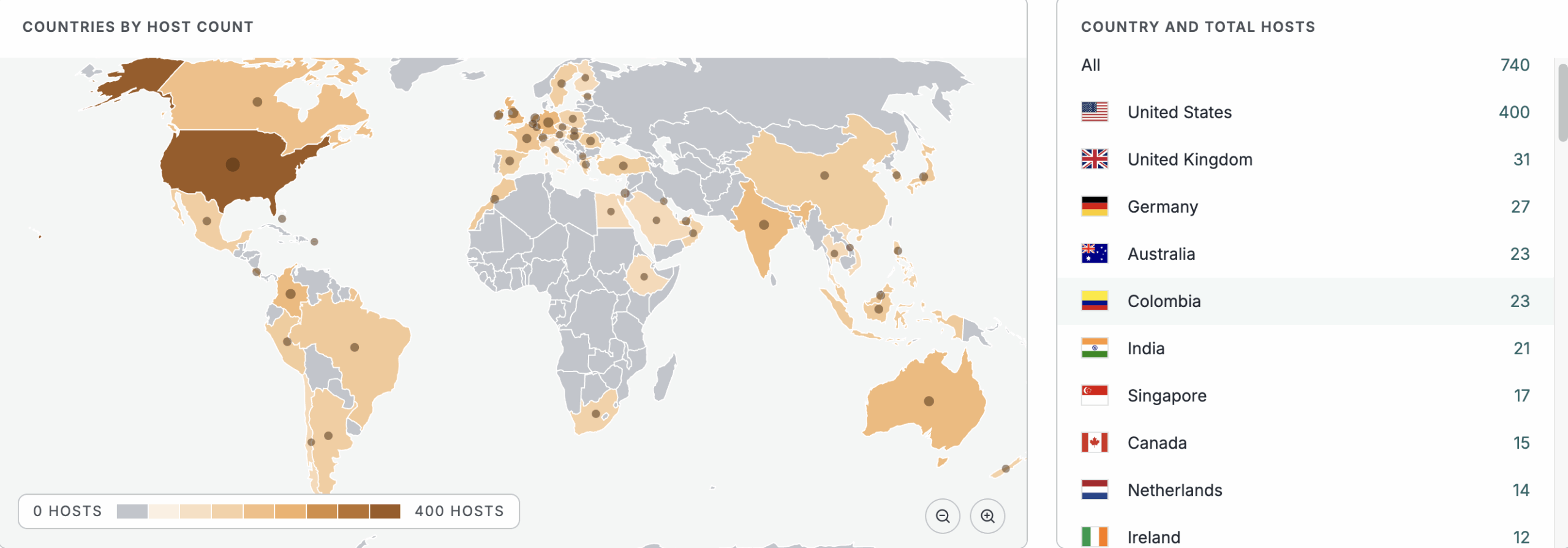
See the full breakdown by country in Censys Platform –>
| Field | Description |
| CVE-ID | CVE-2025-10035 — CVSS 10 (critical) — assigned by Fortra |
| Vulnerability Description | A deserialization vulnerability in the License Servlet of Fortra’s GoAnywhere MFT allows an attacker with a forged license response signature to deserialize arbitrary objects, potentially leading to command injection. Exploitation requires the system to be publicly accessible, which is common for GoAnywhere MFT deployments. |
| Date of Disclosure | September 18, 2025 |
| Affected Assets | Fortra GoAnywhere MFT |
| Vulnerable Software Versions | GoAnywhere MFT versions prior to 7.8.4 (Standard) and 7.6.3 (Sustain Release) |
| PoC Available? | Yes — a proof of concept writeup was published by watchTowr Labs. |
| Exploitation Status | Microsoft Defender researchers observed exploitation of this vulnerability in multiple organizations on September 11, 2025 that leveraged TTPs associated with Storm-1175, a cybercrime group. They stated:“Ultimately, in one compromised environment, the successful deployment of Medusa ransomware was observed.” |
| Patch Status | Upgrade to GoAnywhere MFT 7.8.4 or 7.6.3. If patching is not immediately possible, restrict access to the Admin Console to prevent public exposure. |
Censys Perspective
At the time of writing, Censys observed 740 instances of Forta GoAnywhere MFT. Of those, only 65 reported a version number and 40 instances are running a version known to be affected by this vulnerability.
Platform query for exposed devices:
host.services.software: (vendor: “Fortra” and product: “GoAnywhere MFT”) and not host.services.labels.value = “HONEYPOT”
Legacy Search query for exposed devices:
services.software: (vendor: “Fortra” and product: “GoAnywhere MFT”)
ASM query for potentially vulnerable devices:
risks.name:”GoAnywhere MFT Deserialization Vulnerability [CVE-2025-10035]”
References
- https://www.fortra.com/security/advisories/product-security/fi-2025-012
- https://thehackernews.com/2025/09/fortra-releases-critical-patch-for-cvss.html
- https://www.cisa.gov/known-exploited-vulnerabilities-catalog?search_api_fulltext=CVE-2025-10035&field_date_added_wrapper=all&field_cve=&sort_by=field_date_added&items_per_page=20&url=
- https://www.microsoft.com/en-us/security/blog/2025/10/06/investigating-active-exploitation-of-cve-2025-10035-goanywhere-managed-file-transfer-vulnerability/





