Threat hunting articles and how-to guides are great starting points for learning about the discipline of threat hunting. However, sometimes to really turn theory into practice, you need to see concepts in action. That’s where our webinars come in! To help you enhance your threat hunting skills and fortify your defenses, we’ve recently hosted a number of webinars focused on threat hunting, led by our own experts and those in the field.
In these webinars, available to watch anytime on demand, we jump into the latest techniques, tools, and strategies you can use to get started or level up your threat hunting. Whether you’re brand new to the field or are looking to sharpen your expertise, the following five webinars offer practical insights you can use to hone your craft. Check out the summaries below and start watching!
1. How Sekoia Uses Censys to Uncover and Analyze Emerging Threats
Follow along as Sekoia Senior Threat Intelligence Analyst Marc Nebout demonstrates how he tracks attacker infrastructure and proactively detects malicious activities. As a leader of Sekoia’s Threat Detection and Research Team, Marc is responsible for examining activities from a strategic and technical perspective, providing reliable metrics to Sekoia’s CTI team, and developing tools and methodologies that can be used to discover new threats and monitor existing ones.
As part of this work, Marc and his team are often looking for evidence of Command and Control infrastructure. In this webinar, Marc describes how his team identified credible evidence of the Cobalt Strike Malleable C2 infrastructure and provides a step-by-step tutorial that begins with searching for jQuery and self-signed certificate information in Censys Search. Watch as Marc shows how he refines results and pivots within the tool, and shares the queries he uses along the way. You can learn more about the recent threats Sekoia has identified and monitored in their blog article, Adversary Infrastructure Tracked in 2023.
2. How to Start Tracking Malware Infrastructure: Practical Examples and Tips for Beginners
Matthew from Embee Research and Censys Senior Security Researcher Ariana Mirian bring Matthew’s popular A Beginner’s Guide to Tracking Malware Infrastructure guest blog to life in this highly-informative webinar. Follow along as Matthew and Ariana go inside the Censys Search tool to begin looking for actual evidence of malware infrastructure, with a specific focus on how to build effective queries that are resilient to malware that’s regularly updated. This session is ideal for those who have never searched for malware before or who are new to the world of threat hunting.
Bonus: If you’re threat hunting beginner and are looking for other resources to have handy as you begin investigations, consider our comprehensive Threat Hunting 101 ebook or our 7 Steps for Launching a Threat Hunting Investigation cheat sheet.
3. Internet Investigation with Censys Search
That text message from your bank telling you to “Reply Now” to unlock your account? Or the text from your mail carrier asking you to click a link to confirm your delivery address? There’s a good chance these are phishing attempts, and they’re increasingly common.
In this webinar, Censys Security Researcher Aidan Holland and Co-Owner of My-OSINT Training Micah Hoffman provide an in-depth tutorial into how you can investigate these potential phishing attempts using Censys Search, starting with a real-life example. Watch as Aidan and Micah share what to look for in Censys Search data to determine if a phishing campaign is actually afoot.
Plus, learn how you can take any broad area of interest and begin querying in Censys Search to learn more about the public-facing internet presence associated with it. Discover what types of data to look for on a query results page, how you can refine results with Censys filters and fields, and best practices for augmenting queries that will get you the information you’re looking for, faster.
4. Vidar Investigation: Tracking Malicious Infrastructure
In this on-demand webinar Censys Security Researcher Aidan Holland provides an in-depth overview of how he tracks malicious infrastructure in Censys Search, starting with a Censys Search 101 tutorial, followed by a deep dive into C2 labels and best practices for pivoting. Did you know that with the Censys C2 label, you can quickly acquire a list of the thousands of servers that are running C2 around the world?
Aidan also walks through specific examples regarding how to fingerprint new C2s using HTML titles, HTTP headers, HTML body hash, SSL distinguished names, and JARM or JA3 fingerprints. Plus, learn how he uses the “security tool” label within Censys Search to uncover evidence of malware.
5. Unleash the Power of Censys Search: A Threat Hunter’s Masterclass
Supercharge your threat hunting skills in this engaging session led by Censys Senior Sales Engineer Dan Whitford. In addition to providing an overview of common queries that threat hunters can use to begin exploring in Censys Search, Dan dives deep into advanced queries that can be used to accelerate investigations and pivot on findings. This includes regex queries, which are ideal when simple pattern matches won’t suffice, or when working with fields whose values are long strings.
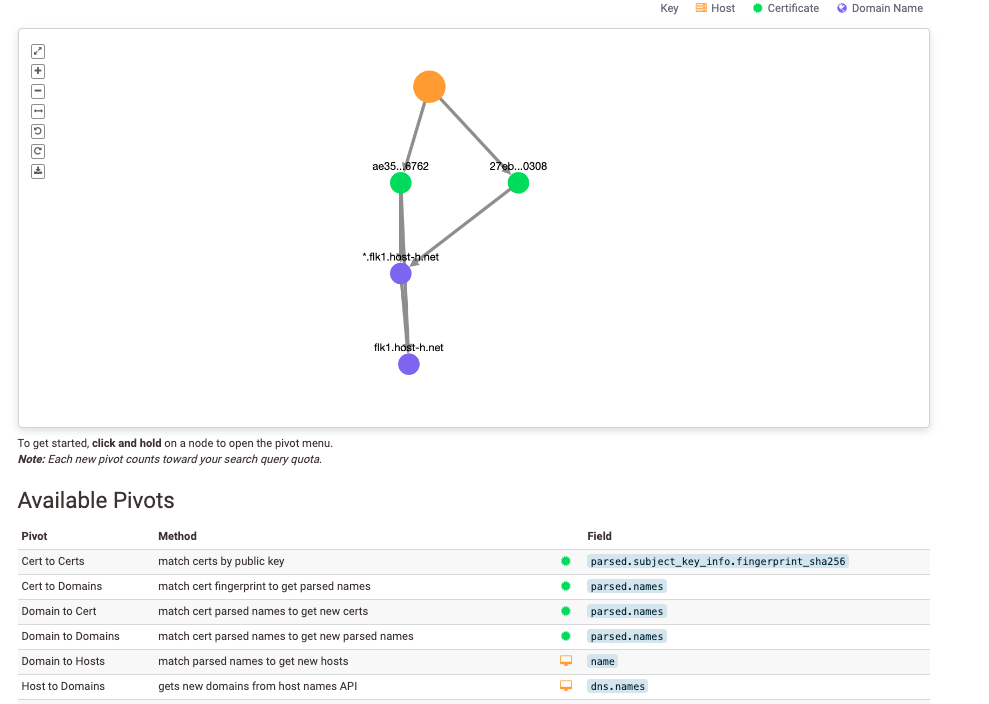
Plus, watch as Dan uses the Explore function within Censys Search to identify other connections within host and certificate data to identify commonalities and pivot investigations. In this recording, you’ll also see real examples of how to use the Map to Censys Beta geolocation feature, as well as how to leverage our Generative AI tool, CensysGPT, which translates natural language queries into Censys Search queries.
You can find even more threat hunting-focused materials in our Resource Hub, and be sure to follow us on LinkedIn and X to learn more about our upcoming webinars!