On December 17, 2024, the CISA Secure Cloud Business Applications (SCuBA) team, who has the responsibility of providing guidance and capabilities to secure federal civilian agencies’ cloud business application environments and protect federal information that is created, accessed, shared, and stored in those environments, released a Binding Operational Directive (BOD) BOD 25-01 entitled “Implementing Secure Practices for Cloud Services.”
According to SCuBA, this BOD was released because, “Malicious threat actors have increasingly targeted cloud environments and evolved tactics to gain initial cloud access. In recent cybersecurity incidents, the improper configuration of security controls in cloud environments introduced substantial risk and resulted in actual compromises.”
We have repeatedly seen this issue throughout all industries, not just the federal government. A sophisticated French-based threat actor group recently stole thousands of cloud credentials related to a major Cloud Service Provider (CSP).
Threat actors in general go after the low-hanging fruit and as a result prey on weaknesses in controls from private and public organizations migrating to cloud computing without fully understanding the complexity of services or the controls offered in cloud computing.
In this case, the French-based threat actor group was able to steal infrastructure credentials, proprietary source code, application databases, credentials to additional external services, as well as thousands of keys and secrets lifted from victim networks. With this information, the attackers were able to check for privileges related to this major CSP for additional services that may be susceptible.
It’s a tale as old as time since the inception of cloud computing. So how do organizations defend themselves against attacks targeting their cloud environments?
SCuBA Secure Configuration Baselines
According to SCuBA: “To combat these threats, through the SCuBA project, CISA developed Secure Configuration Baselines, providing consistent and manageable cloud security configurations.”
To simplify this even further, it’s about basic cybersecurity hygiene. All cybersecurity experts agree that to protect your cloud environment against cybersecurity attacks, you have to implement the same security measures/principles you have for your on-premise infrastructure to your cloud environment.
This means having a clear understanding of the security tools you have at your disposal from the CSP to help you secure your environment.
- Utilize WAF, IAM, and Logs in support of your cloud environment.
- Ensure you have visibility into your cloud environment and have the proper controls in place for access control.
- Cloud environments are dynamic and as a result change constantly. Make sure you are continually monitoring your cloud environment for expected and unexpected changes.
- If your team is not up to speed on the CSP security mechanisms available to help secure your cloud environment, invest in training for them or acquire the services needed to assist in securing your organization’s cloud environment.
SCuBA has taken the time and effort to create and provide documentation, reference architectures, tools, and GitHub repositories to help primarily Federal Civilian Executive Branch (FCEB) agencies improve the security of assets hosted in cloud environments, but these resources are available to anyone that needs guidance on how to secure their cloud environment.
BOD 25-01 – “requires agencies to implement a set of SCuBA Secure Configuration Baselines for certain Software as a Service (SaaS) products widely used in the FCEB, deploy CISA developed automated configuration assessment tools to measure against the required baselines, integrate with CISA’s continuous monitoring infrastructure, and remediate deviations from the secure configuration baselines.”
In an effort to reduce risks highlighted by recent adversary activity and increase resiliency for FCEB agencies against cyber threats, it’s important to highlight the fact that this directive is not operating in a silo: “This Directive complements existing federal resources for cloud security, including the Federal Risk and Authorization Management Program (FedRAMP), relevant NIST guidance, and the CISA Trusted Internet Connections (TIC) 3.0 Cloud Use Case.
Per SCuBA:“This Directive applies to all production or operational cloud tenants (operating in or as federal information systems) with an associated and finalized SCuBA Secure Configuration Baselines published by CISA.”
Required Action: Identifying All In-Scope Cloud Tenants
Additionally, there are six required actions for all in-scope cloud tenants that federal agencies must follow. The first rapidly approaching task of identifying all cloud tenants within the scope of this directive is due no later than Friday, February 21st, 2025.
While this may seem like yet another mandate added to your already demanding workload, these steps are essential for maintaining strong cybersecurity hygiene and preventing many of the attacks organizations face today. Returning to the basics is often the most effective starting point.
To support the adoption of this BOD, SCuBA has provided an extensive array of resources, including documentation, tools, and reference architectures. Additionally, there are several Tier-1 cybersecurity tools available that can help you secure your cloud environment effectively.
Censys, a leader in internet intelligence, is one such solution.
How Can Censys Help You Protect Your Cloud Environment?
At Censys, we firmly believe that you can’t protect what you don’t see.
Censys empowers organizations to uncover unknown cloud assets and identify potential misconfigurations across all cloud providers. With Censys, you can securely migrate these assets into managed accounts, ensuring governance over your cloud adoption strategy.
Censys delivers granular insights into your cybersecurity posture, as well as that of supply chain partners, enabling a proactive approach to risk management. By revealing what attackers see when assessing your organization’s external exposure, Censys helps you strengthen your defenses and align with BOD 25-01.
Censys Key Benefits
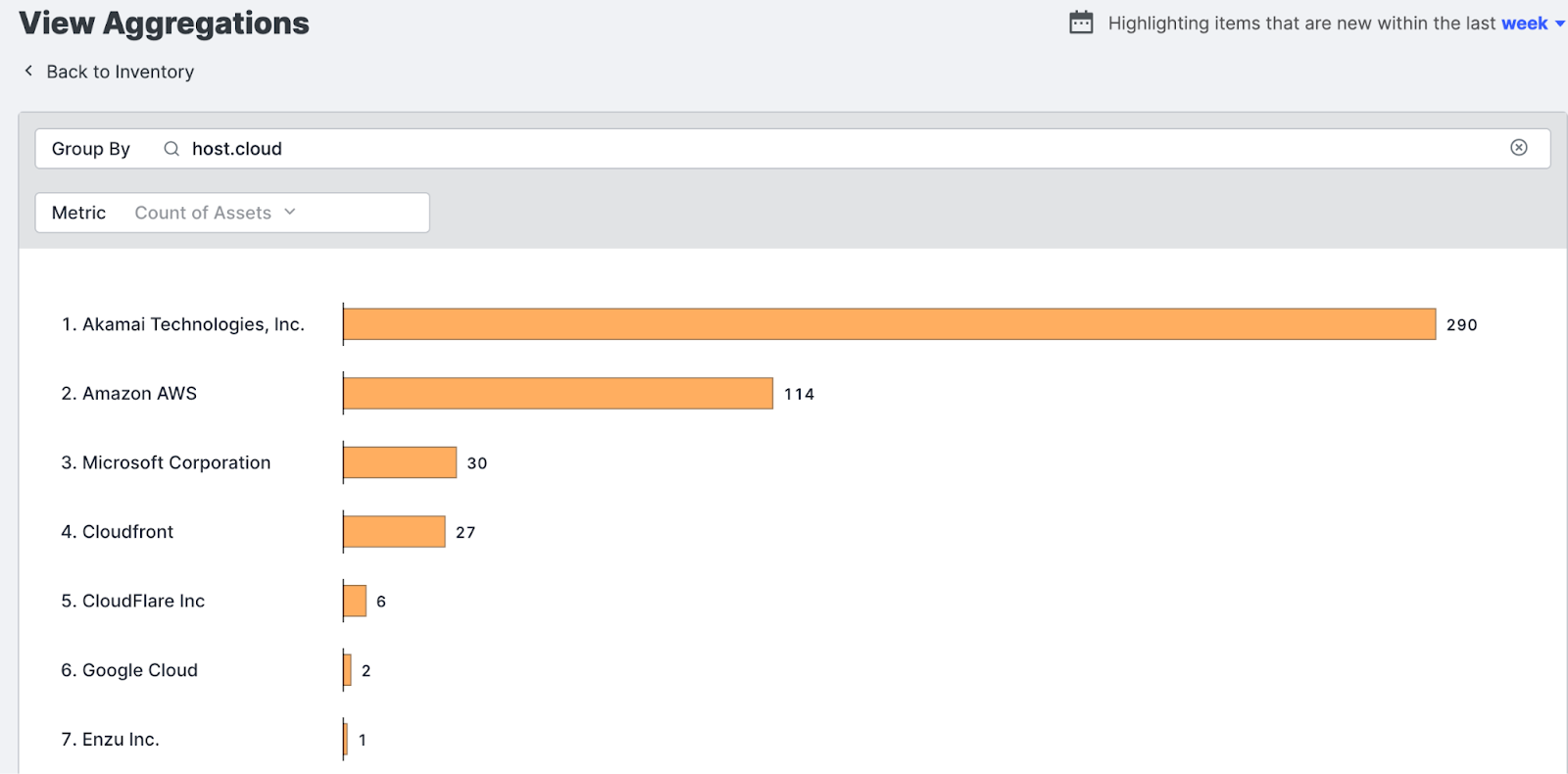
Cloud-agnostic discovery: Censys identifies exposed cloud assets and continuously monitors resources within all three major cloud service providers (CSPs) (AWS; Azure; GCP). This includes cloud storage buckets/blobs, virtual instances, databases, and more.
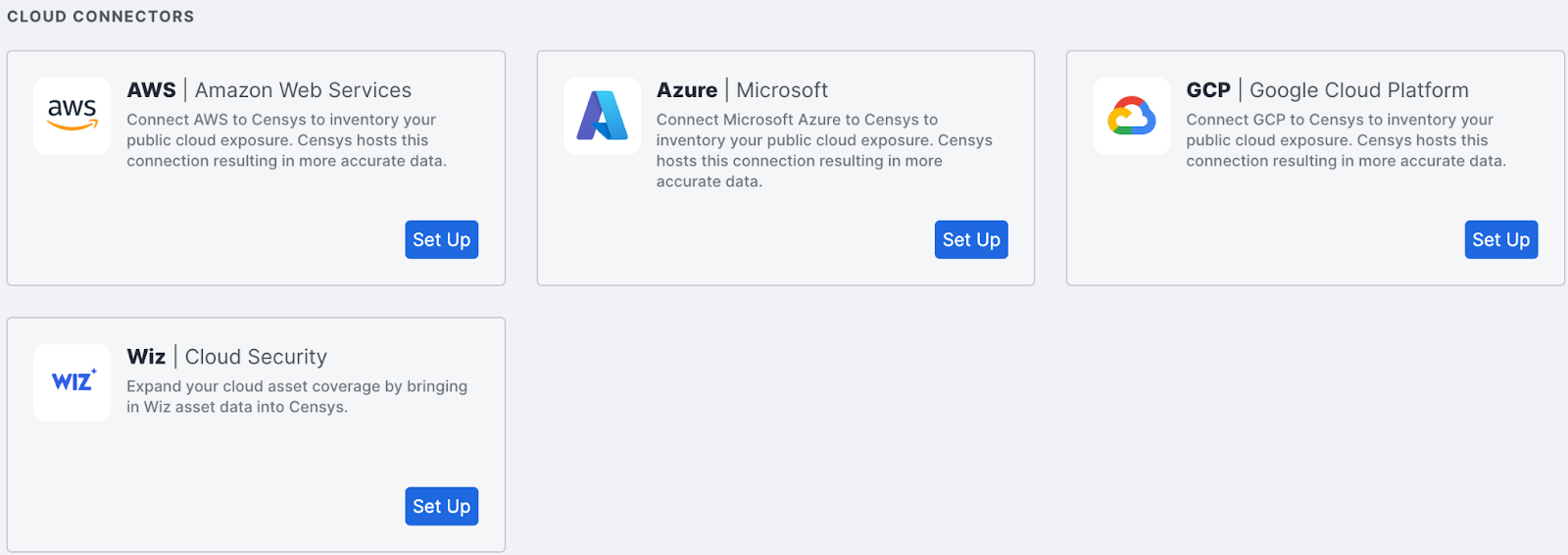
Attribution and continuous monitoring: Censys assists with attribution and provides continuous monitoring to manage and reduce risks associated with cloud and external-facing infrastructure.
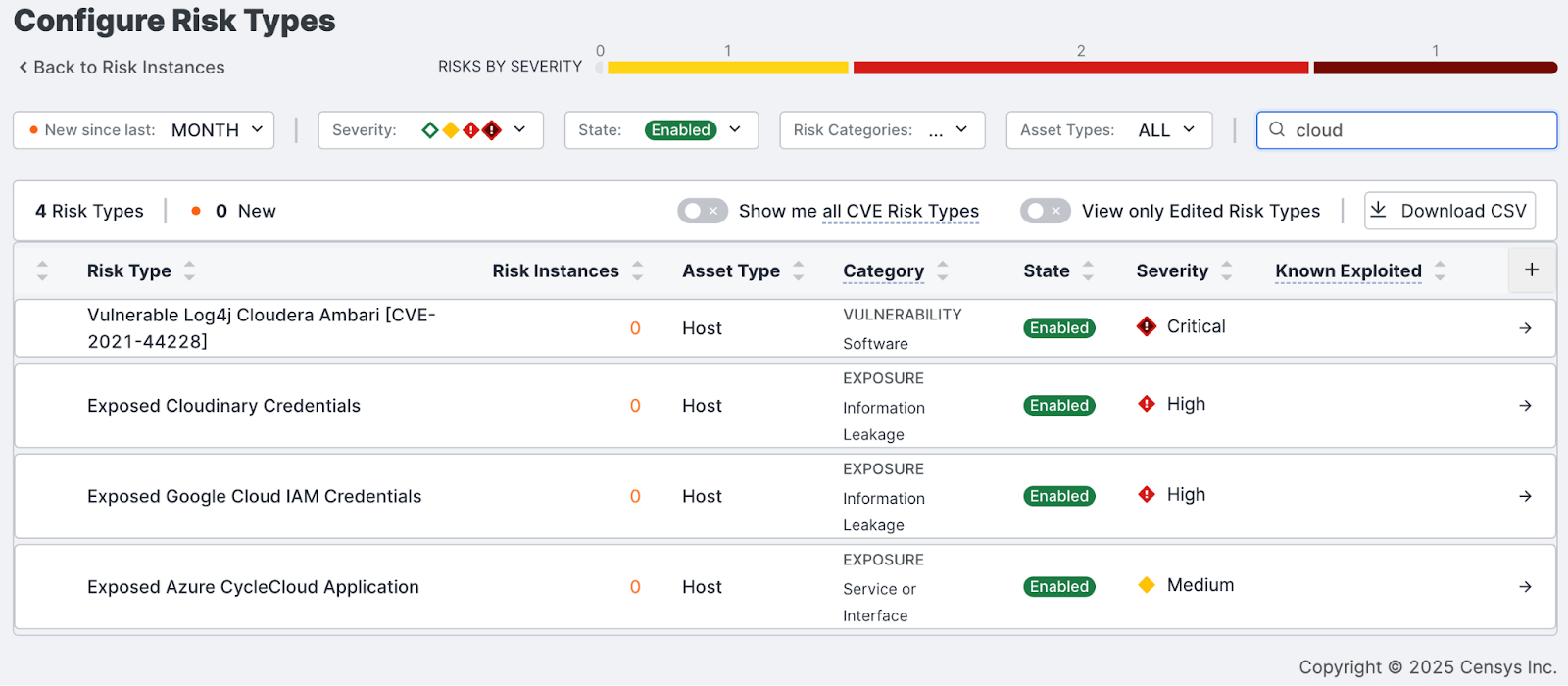
Secure configuration management: Censys helps identify cloud resources that are improperly configured and distinguish between managed and unmanaged assets.
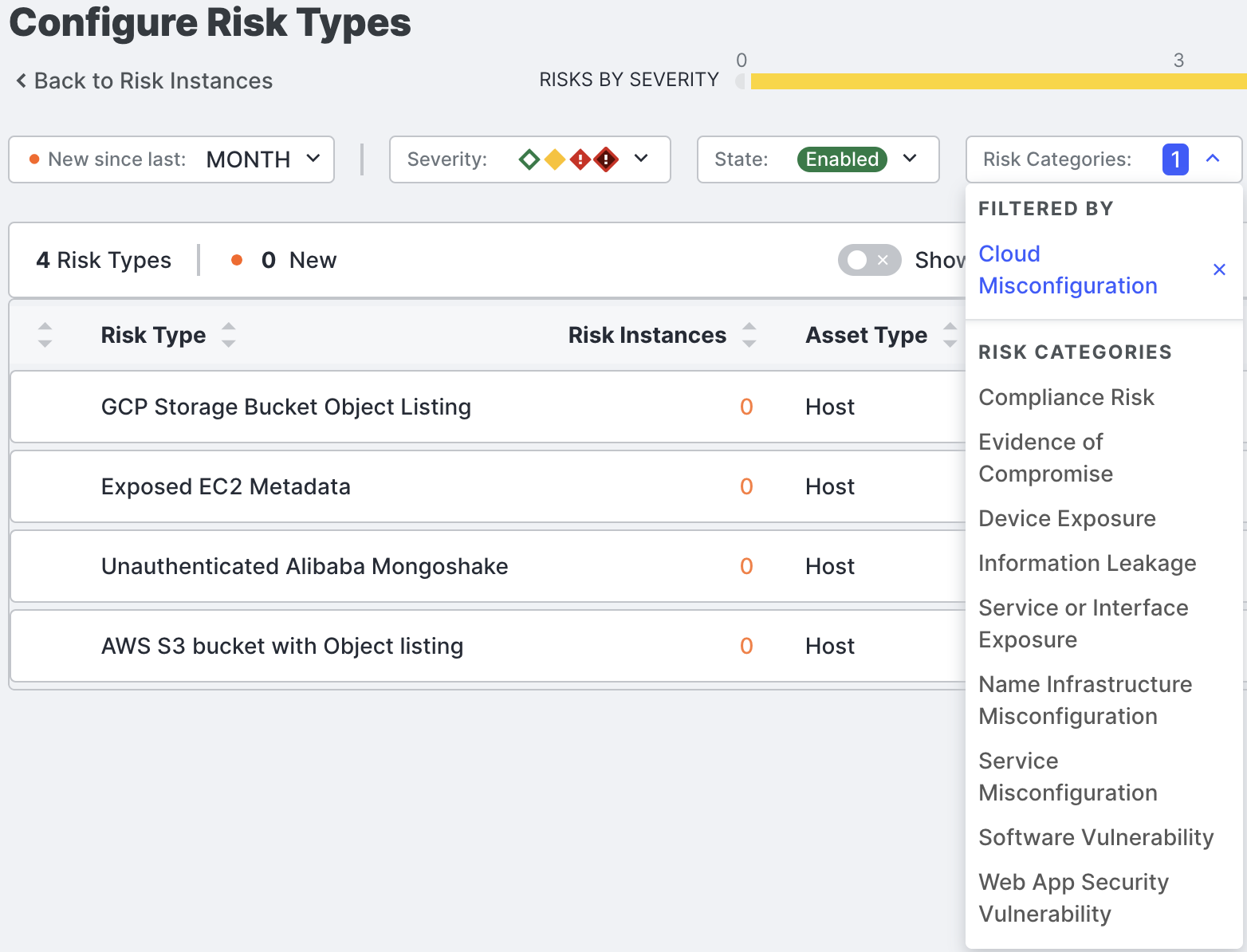
Immediate Benefits
- Sanctioned Asset Tracking:
Assemble a curated list of sanctioned cloud assets used across your organization to differentiate between managed and unmanaged resources.
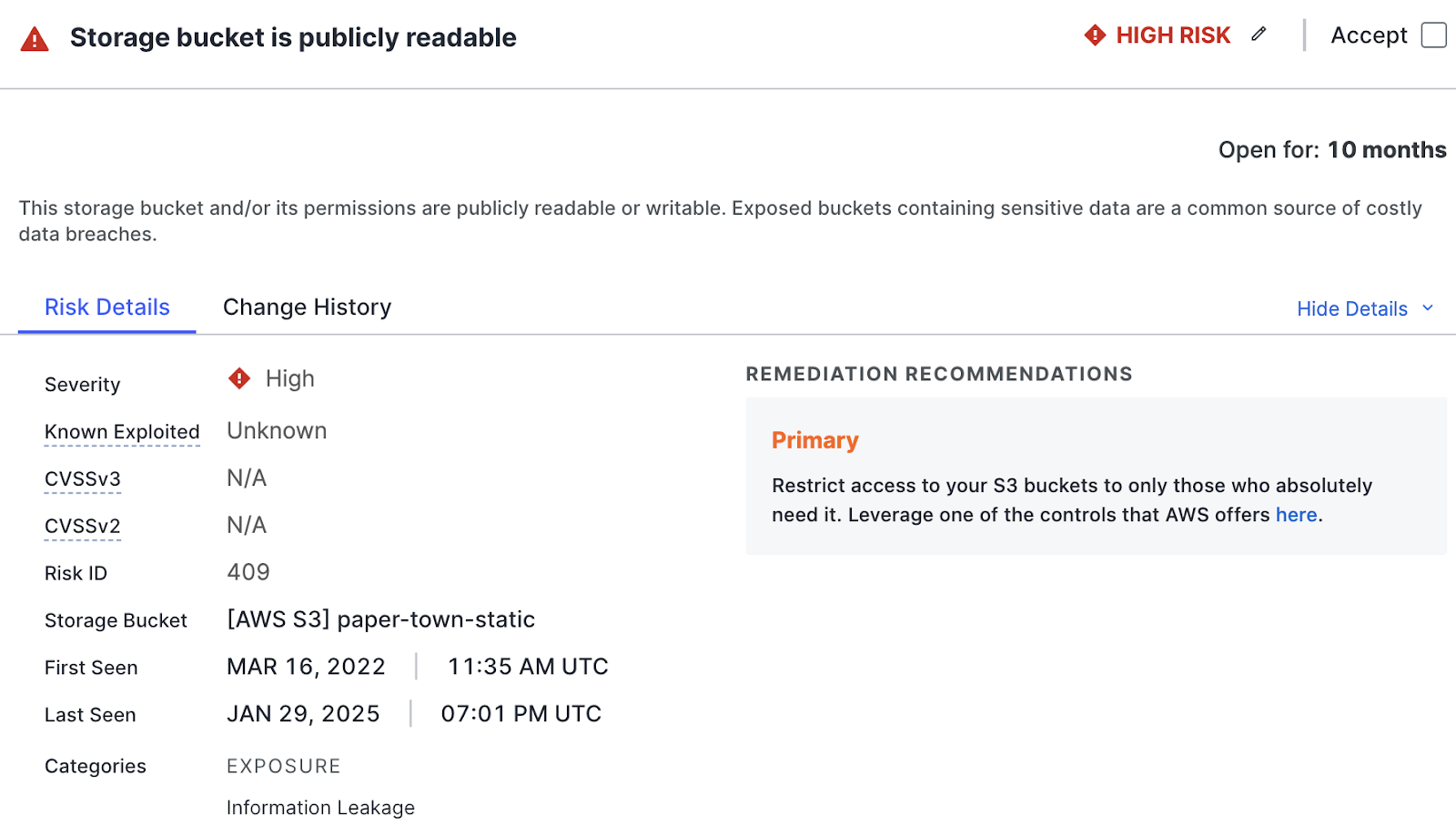
- Cloud Misconfiguration Remediation:
Address common cloud misconfigurations, such as:- Logging misconfigurations
- Authentication misconfigurations
- Firewall misconfigurations
- Credential exposure
With Censys, you gain a comprehensive understanding of your cloud environment and the tools needed to secure it. By aligning with BOD 25-01, NIST CSF, and other federal mandates, Censys supports effective cloud governance while safeguarding your organization’s cloud assets.
Learn more about how Censys can help you meet these objectives, control cloud sprawl, and enhance cloud security.