At Censys, we’ve always believed that visibility is power. Censys Attack Surface Management (ASM) provides security analysts with the unrivaled attack surface visibility into exposed assets. But visibility alone isn’t enough – security leaders and analysts also need clarity: What’s exposed? Why does it matter? And how do we fix it?
This is where the Insights Experience in Censys ASM delivers. By transforming raw data into digestible dashboards and inventories, Insights help analysts uplevel their attack surface data and track progress against key security initiatives, such as software compliance and exposure management.
From Data to Insight
Censys ASM already solves the hardest problem: discovering and attributing assets across sprawling, complex infrastructures. But once assets are discovered, the real challenge begins – understanding which exposures matter most.
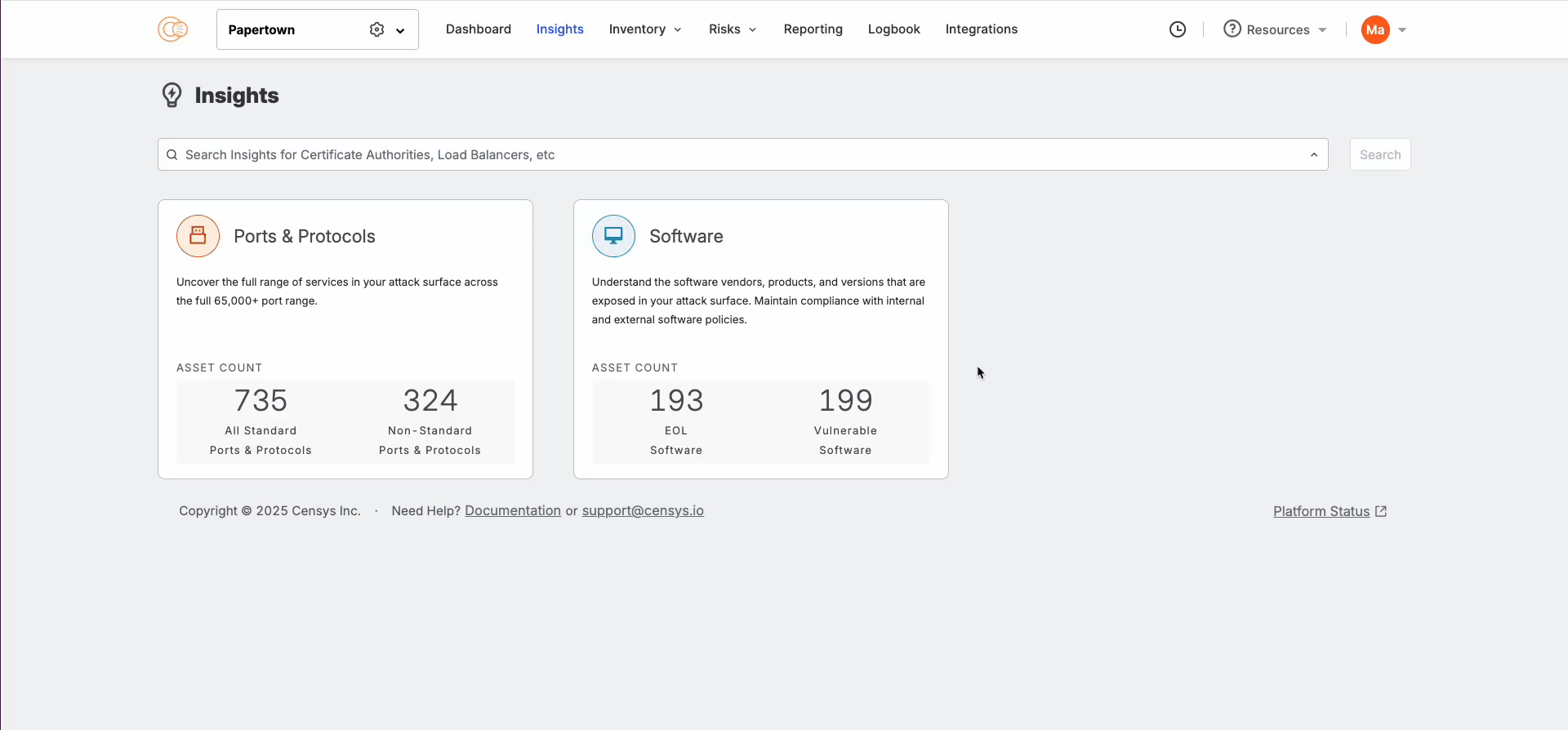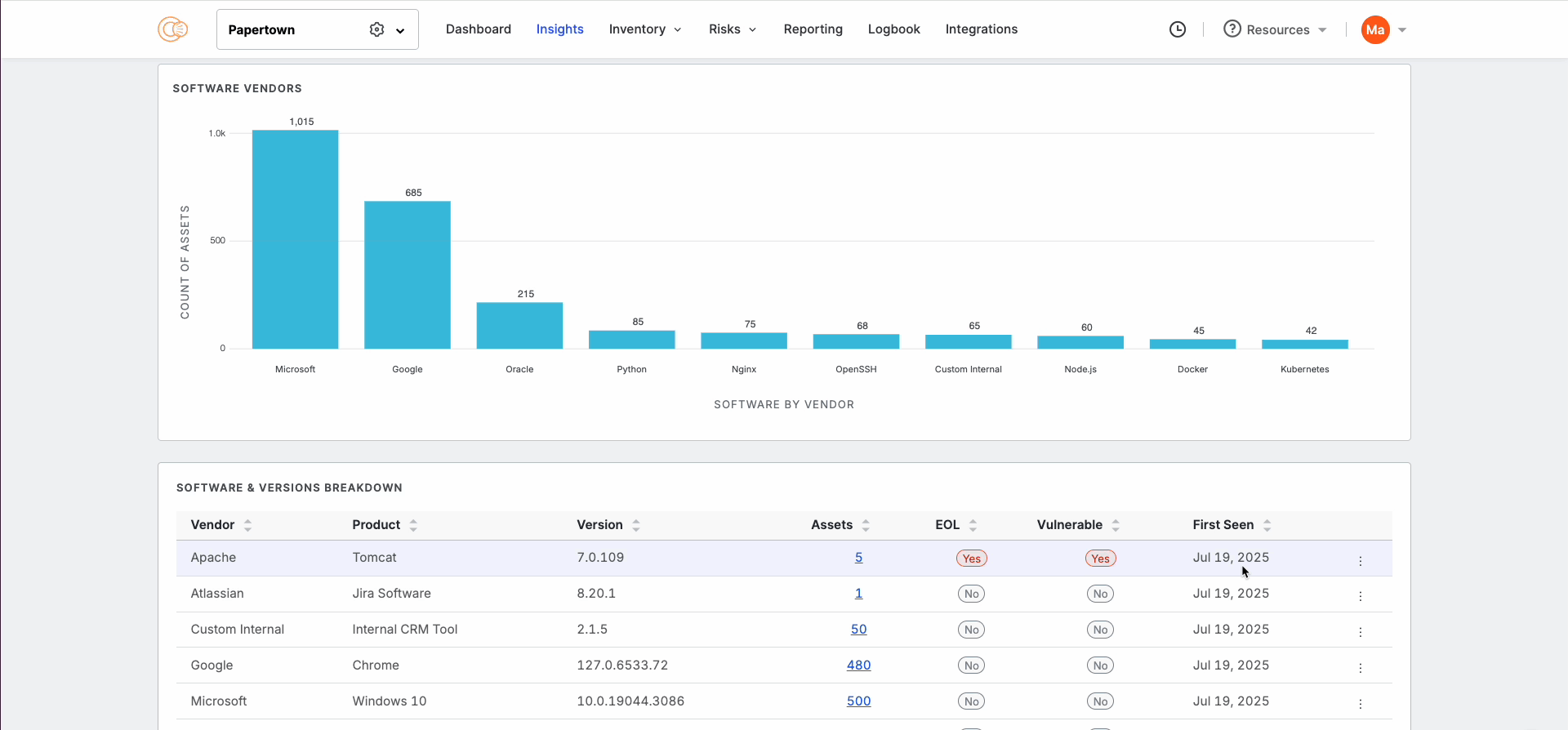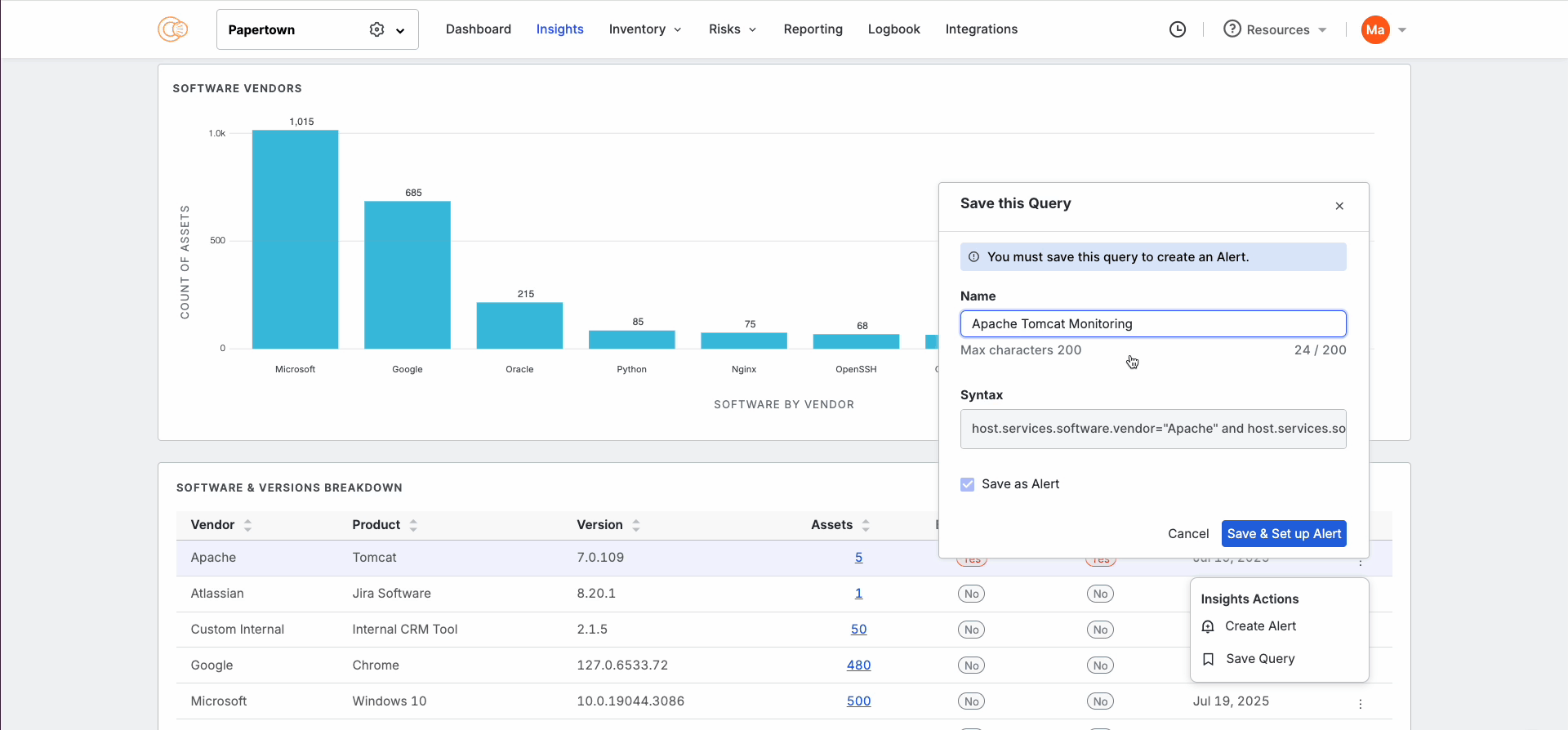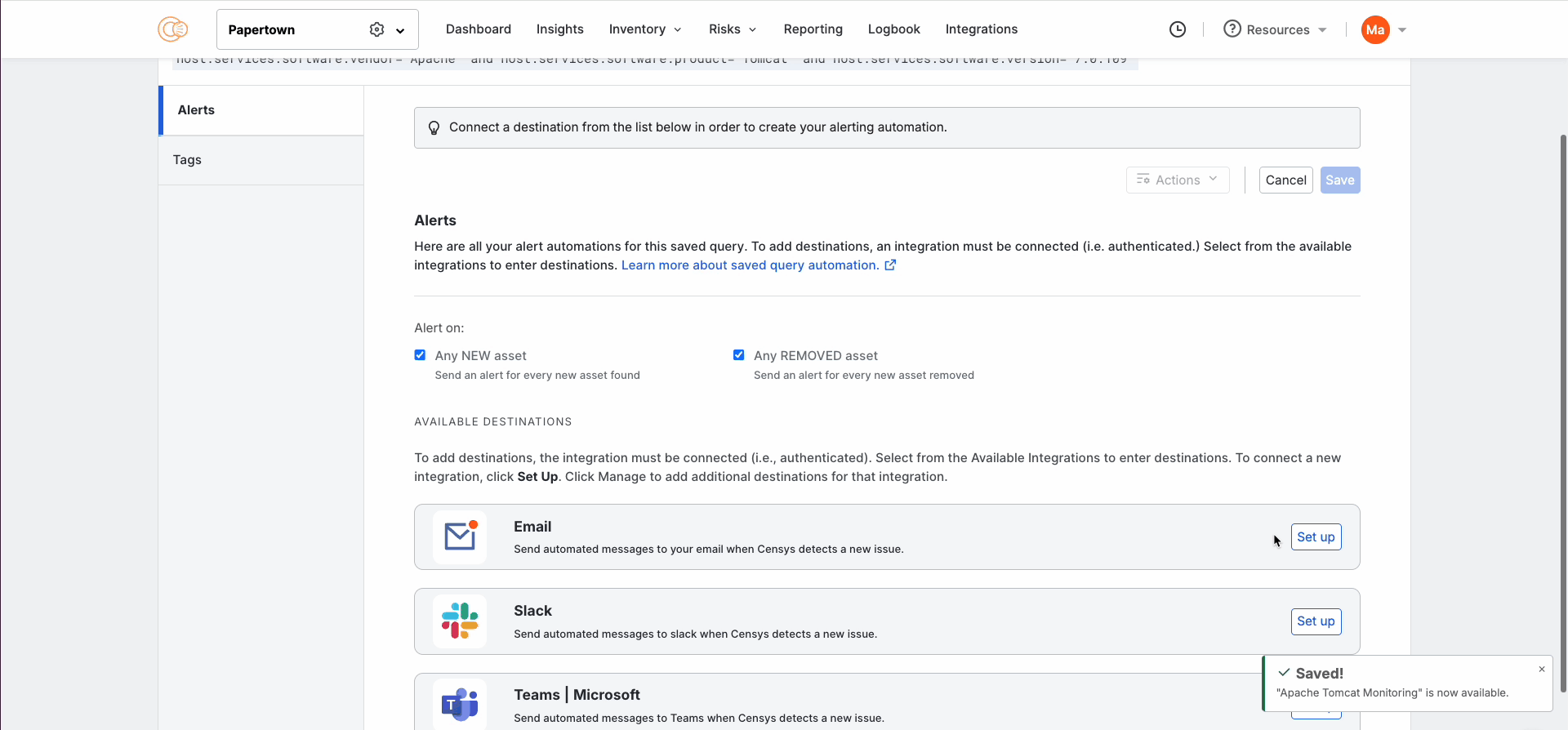
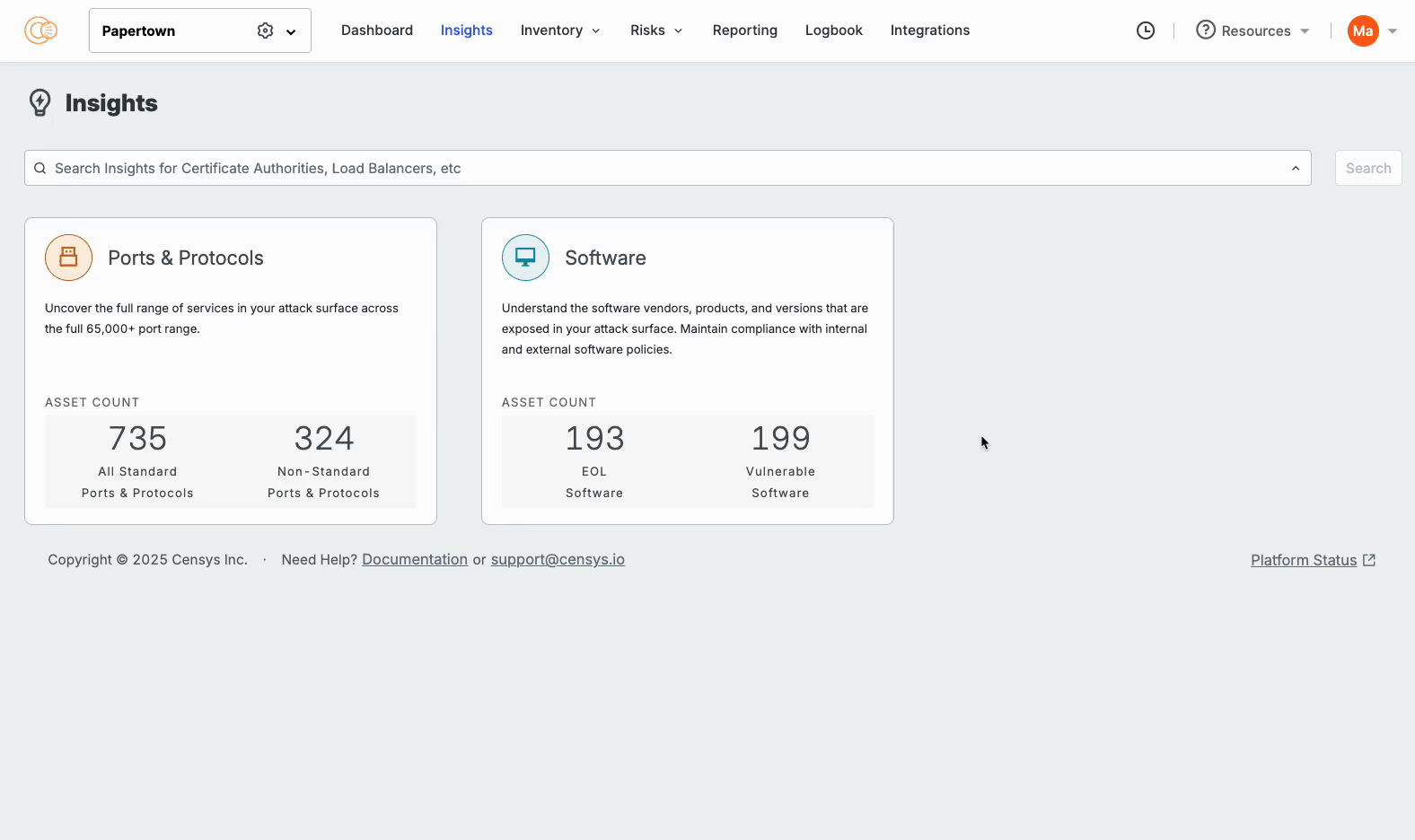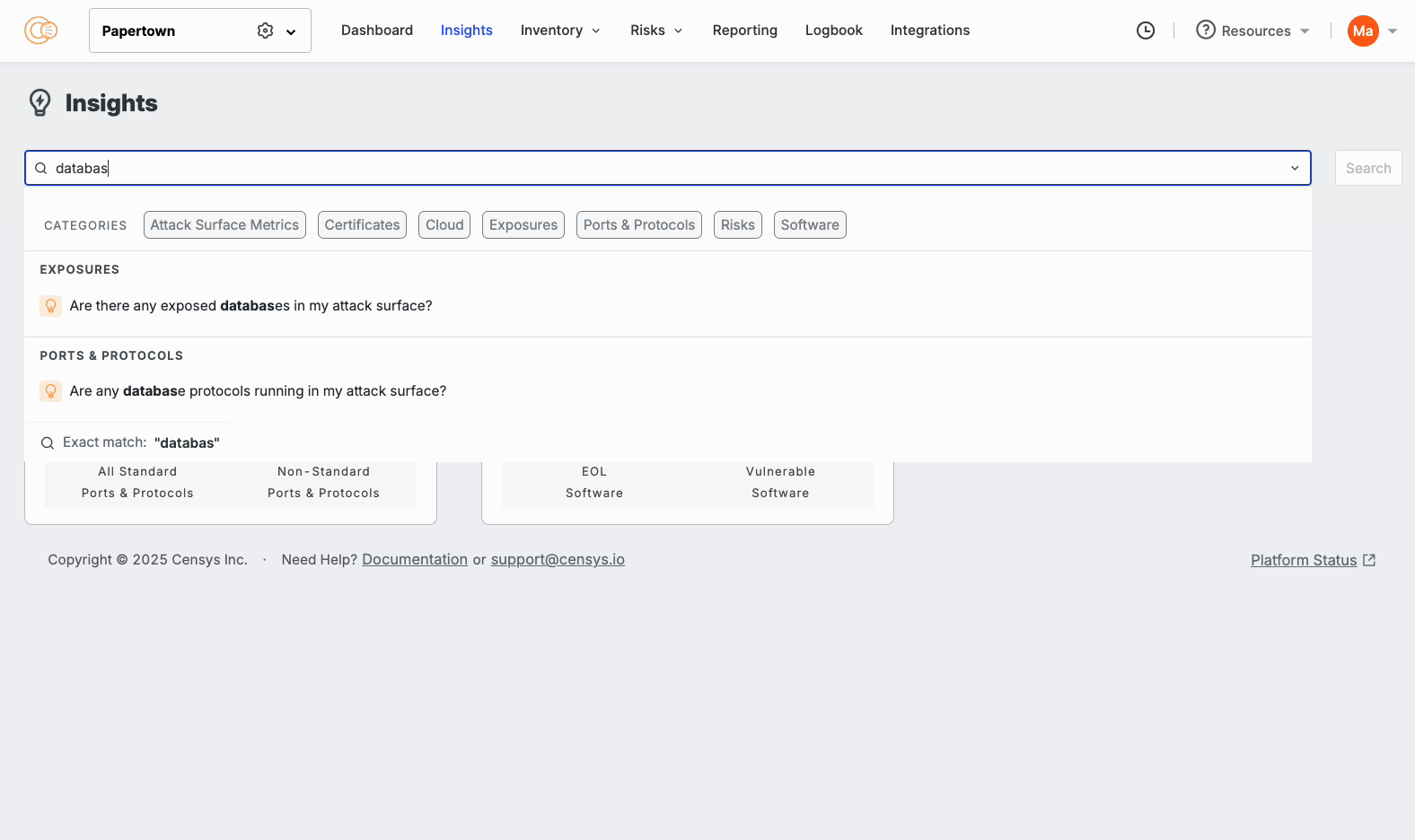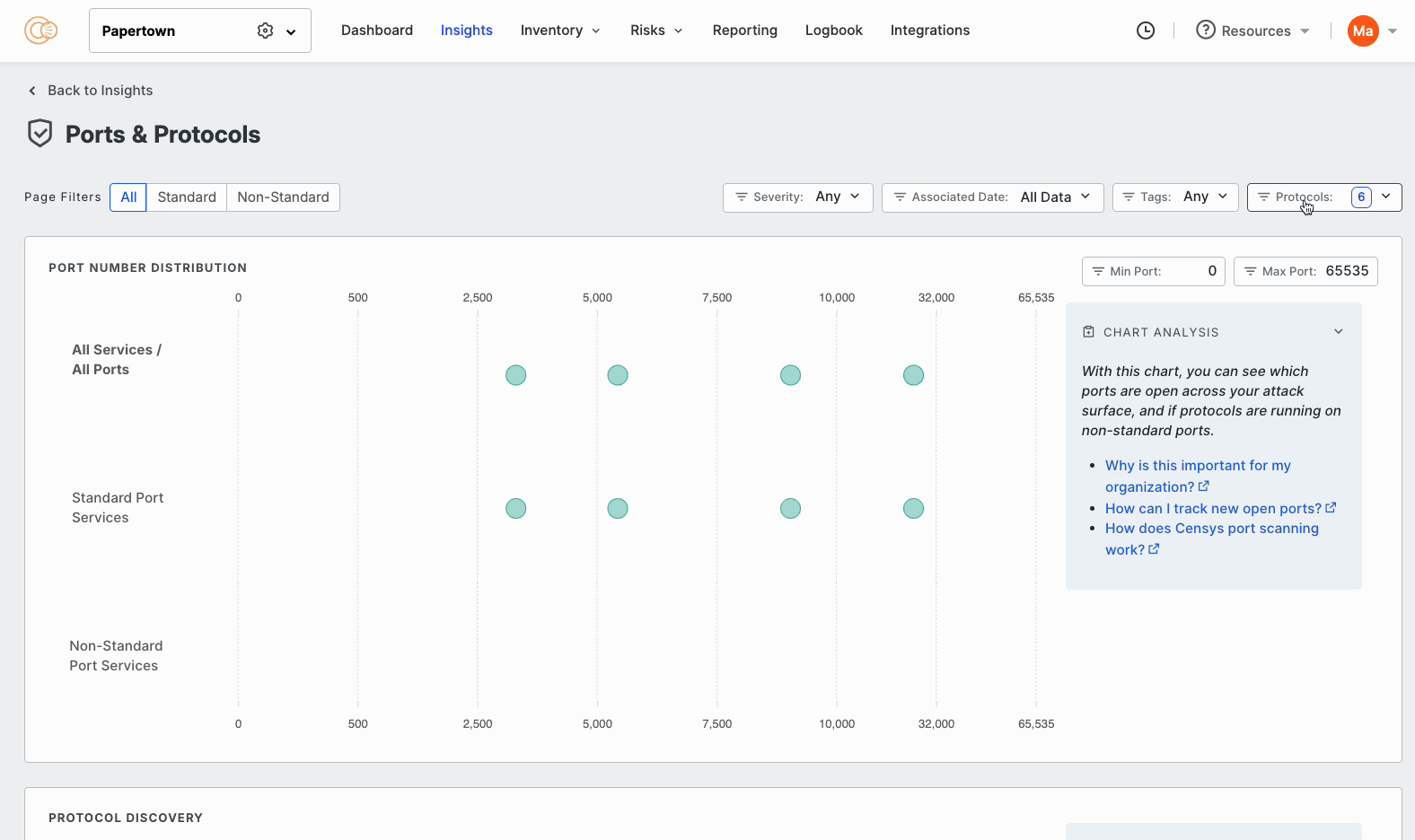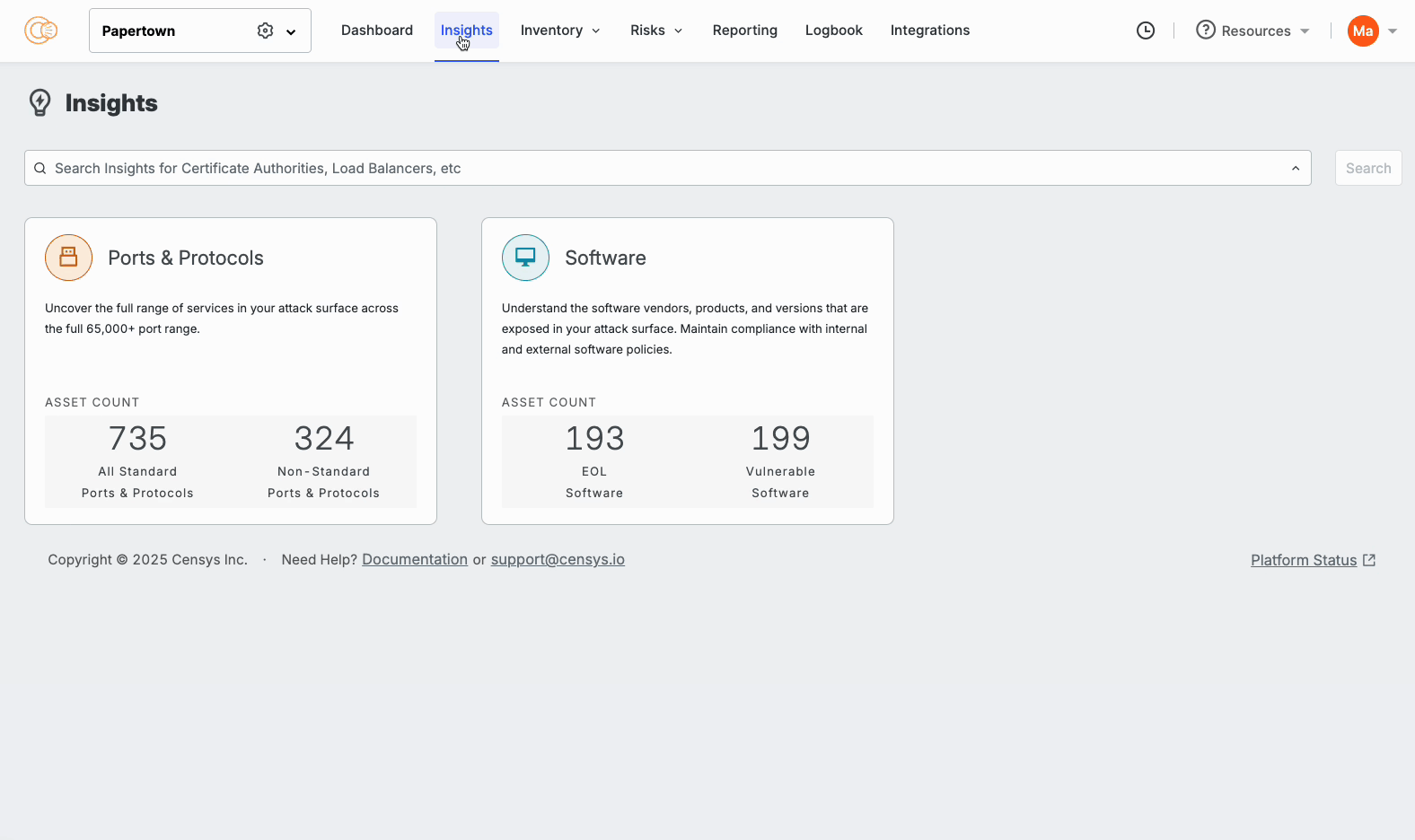
An asset may be running an uncommon service on a non-standard port or contain a vulnerable software version. Understanding these risks holistically allows analysts to reduce business risk faster. For example, upgrading the software on 1000 servers is far more efficient than going after each and every instance. Clearly, comprehensive views of key exposures are crucial to providing the most actionable steps to reducing their attack surface.
Attack Surface Management is also becoming a core topic for security executives, and communicating what is exposed is critical security operations. SOC and vulnerability teams are asked to track their progress against key initiatives, which are designed to ensure software is up-to-date and unnecessary exposures are closed. Without a digestible report, these details are difficult to articulate.
Maintain Full Visibility; Stay on Top of Security Initiatives
This is where the new Insights Experience can help. Software and service visibility is now available in purpose-built dashboards and inventories, enabling analysts to remediate vulnerabilities and exposures holistically. For example, if you want to know if you are impacted by a critical vulnerability, such as the Sharepoint ToolShell exploit (CVE-2025-53770), you can filter for the impacted software and see all the assets that are impacted. At the same time, security directors and CISOs can understand if the organization is compliant across all software and services from a bird’s eye view.

Within these inventories, you can filter for the exact information that you are looking for and set up alerting in one click. This way, if a new vulnerable software version or unexpected service appears, your team is notified right away:
Additionally, you can now get quick answers to questions that are critical to your security team, all within the new insights search bar. For example:
- Is any critical infrastructure exposed, like a database or network administration tool?
- Are any assets located outside of countries that I operate in?
- Am I running any vulnerable or end-of-life software?
- Is there any potential sensitive information exposure in my attack surface?
All of these questions and more are now available within the ASM Insights interface:
If you are a Censys ASM customer, try out Insights today! If you are new to Censys ASM, schedule a demo to learn how you can maximize your external visibility.