Vulnerability Description
A collection of 13 zero-day vulnerabilities in Ivanti Endpoint Manager (formerly LANDESK Management Suite) was disclosed by Zero Day Initiative. These vulnerabilities allow remote attackers to execute arbitrary code on affected installations via HTTP. Twelve of the vulnerabilities are remote code execution vulnerabilities and one is a local privilege escalation vulnerability. The most critical of these vulnerabilities allows for unauthenticated RCE via directory traversal in OnSaveToDB method. Other flaws include SQL injection across multiple components and deserialization vulnerability in AgentPortal service.
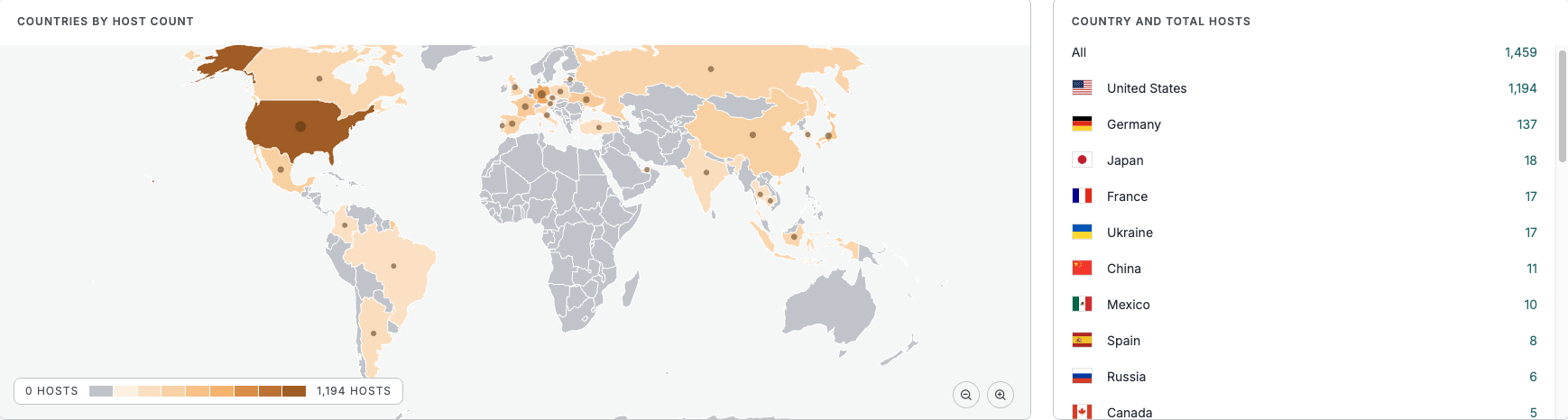
See the full breakdown by country in the Censys Platform –>
| Field | Description |
| CVE-ID | Multiple CVEs pending (13 vulnerabilities) |
| Vulnerability Description | Released zero-day vulnerabilities include: ZDI-25-947: Ivanti Endpoint Manager AgentPortal Deserialization of Untrusted Data Local Privilege Escalation Vulnerability ZDI-25-946: Ivanti Endpoint Manager Report_RunPatch SQL Injection RCE Vulnerability ZDI-25-945: Ivanti Endpoint Manager MP_Report_Run2 SQL Injection RCE Vulnerability ZDI-25-944: Ivanti Endpoint Manager DBDR SQL Injection RCE Vulnerability ZDI-25-943: Ivanti Endpoint Manager PatchHistory SQL Injection RCE Vulnerability ZDI-25-942: Ivanti Endpoint Mangaer MP_QueryDetail2 SQL Injection RCE Vulnerability ZDI-25-941: Ivanti Endpoint Manager GetCountForQuery SQL Injection RCE Vulnerability ZDI-25-940: Ivanti Endpoint Manager MP_QueryDetail SQL Injection RCE Vulnerability ZDI-25-939: Ivanti Endoint Manager MP_VistaReport SQL Injection RCE Vulnerability ZDI-25-938: Ivanti Endpoint Manager Report_RunPatch SQL Injectino RCE Vulnerability ZDI-25-937: Ivanti Endpoint Manager Report_Run SQL Injection RCE Vulnerability ZDI-25-936: Ivanti Endpoint Manager Report_Run2 SQL Injection RCE Vulnerability ZDI-25-935: Ivanti Endpoint Manager OnSaveToDB Directory Traversal RCE Vulnerability |
| Date of Disclosure | October 7, 2025 |
| Affected Assets | Ivanti Endpoint Manager (EPM/LANDesk) |
| Vulnerable Software Versions | All versions |
| PoC Available? | At time of writing, there is no PoC available. |
| Exploitation Status | At time of writing, there has been no known exploitation. |
| Patch Status | Zero-Day: No patches available. Ivanti has requested an extension until March 2026. |
Censys Perspective
Censys observed 1,452 Ivanti Endpoint Manager/LANDesk instances exposed globally; however, only 62 of those instances (~4%) provide version information.
The queries below can help identify any Ivanti Endpoint Manager / LANDesk instances exposed, but they are not necessarily vulnerable.
host.services.endpoints.http.headers: (key: “Server” and value: “CBA8/”) or host.services.endpoints.http.html_title=”LANDesk(R) Management Agent” or host.services.cert.parsed.subject.organization=”LANDesk(R) Management Suite” or host.services.cert.parsed.issuer.organizational_unit=”EPM-APPSRV” or host.services.cert.parsed.subject.locality=”LDMS Client” or host.services.cert.parsed.issuer.locality=”LDMS Core Server”
host.services.http.response.headers: (key: “Server” and value.headers: “CBA8/*”) or host.services.http.response.html_title=”LANDesk(R) Management Agent” or host.services.tls.certificate.parsed.subject.organization=”LANDesk(R) Management Suite” or host.services.tls.certificate.parsed.issuer.organizational_unit=”EPM-APPSRV” or host.services.tls.certificate.parsed.subject.locality=”LDMS Client” or host.services.tls.certificate.parsed.issuer.locality=”LDMS Core Server”
services.http.response.headers: (key: “Server” and value.headers: “CBA8/*”) or services.http.response.html_title=”LANDesk(R) Management Agent” or services.tls.certificate.parsed.subject.organization=”LANDesk(R) Management Suite” or services.tls.certificate.parsed.issuer.organizational_unit=”EPM-APPSRV” or services.tls.certificate.parsed.subject.locality=”LDMS Client” or services.tls.certificate.parsed.issuer.locality=”LDMS Core Server”
References
- https://cyberinsider.com/zdi-drops-13-unpatched-ivanti-zero-days-enabling-remote-code-execution/
- https://www.zerodayinitiative.com/advisories/ZDI-25-947/
- https://www.zerodayinitiative.com/advisories/ZDI-25-946/
- https://www.zerodayinitiative.com/advisories/ZDI-25-945/
- https://www.zerodayinitiative.com/advisories/ZDI-25-944/
- https://www.zerodayinitiative.com/advisories/ZDI-25-943/
- https://www.zerodayinitiative.com/advisories/ZDI-25-942/
- https://www.zerodayinitiative.com/advisories/ZDI-25-941/
- https://www.zerodayinitiative.com/advisories/ZDI-25-940/
- https://www.zerodayinitiative.com/advisories/ZDI-25-939/
- https://www.zerodayinitiative.com/advisories/ZDI-25-938/
- https://www.zerodayinitiative.com/advisories/ZDI-25-937/
- https://www.zerodayinitiative.com/advisories/ZDI-25-936/
- https://www.zerodayinitiative.com/advisories/ZDI-25-935/





