Vulnerability Description:
CVE-2026-24858 is a critical authentication bypass vulnerability (CVSS 9.4) affecting Fortinet FortiOS, FortiManager, FortiAnalyzer, FortiProxy, FortiWeb, and potentially FortiSwitch Manager. This vulnerability has been exploited in the wild and was added to the CISA Known Exploited Vulnerabilities catalog on January 27, 2026, with a remediation deadline of January 30, 2026. The flaw allows an attacker with a FortiCloud account and a registered device to log into other devices registered to other accounts when FortiCloud SSO authentication is enabled.
While FortiCloud SSO is not enabled by default, it is commonly enabled when administrators register devices to FortiCare via the GUI unless they explicitly disable the “Allow administrative login using FortiCloud SSO” toggle. Fortinet had previously confirmed active exploitation before blocking vulnerable devices from authenticating. Malicious actors used the accounts cloud-noc@mail.io and cloud-init@mail.io, and attackers downloaded device configurations and created local admin accounts (such as “audit”, “backup”, “itadmin”, “secadmin”, “support”, “svcadmin”, or “system”) for persistence. Fortinet temporarily disabled FortiCloud SSO on January 26, 2026, and re-enabled it on January 27, 2026 with restrictions that block login from devices running vulnerable versions.
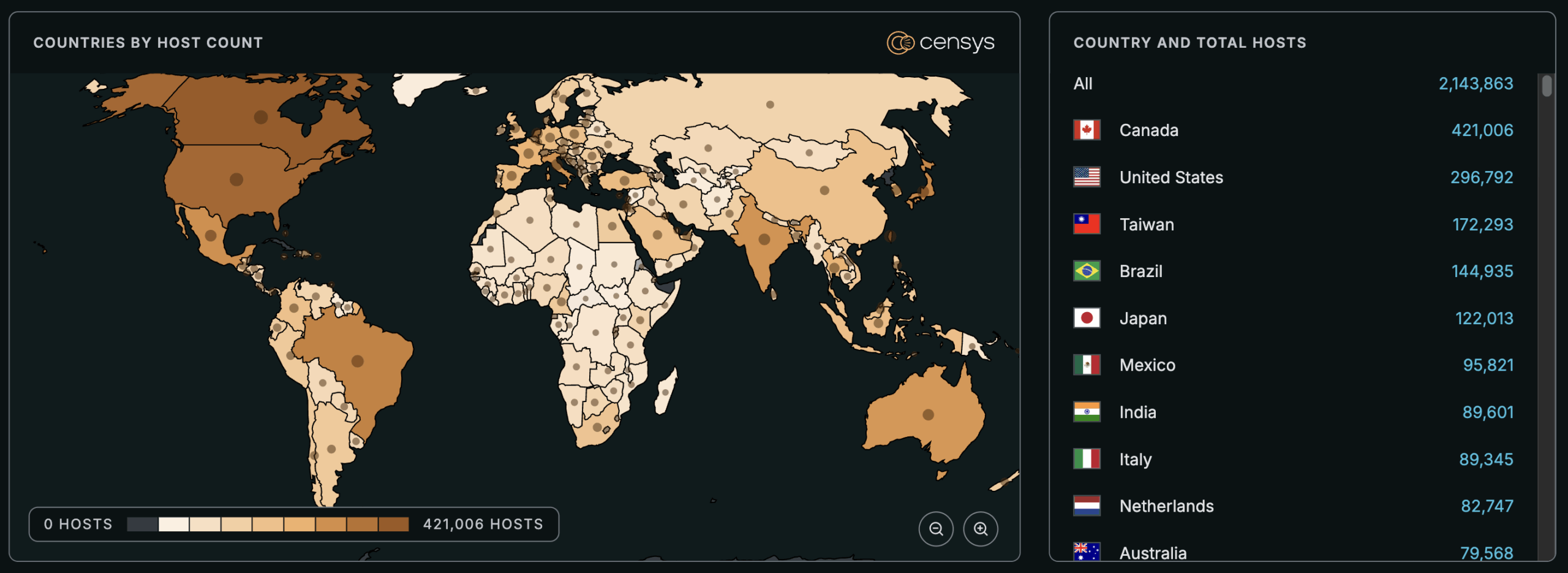
See the full breakdown by country in Censys Platform →
| Field | Description |
| CVE-ID | CVE-2026-24858 — CVSS 9.4 — assigned by Fortinet |
| Vulnerability Description | A critical authentication bypass vulnerability allows an attacker with a FortiCloud account and a registered device to log into other devices registered to other accounts when FortiCloud SSO authentication is enabled.While FortiCloud SSO is not enabled by default, it is commonly enabled when administrators register devices to FortiCare via the GUI unless they explicitly disable the “Allow administrative login using FortiCloud SSO” toggle. Fortinet had previously confirmed active exploitation before blocking vulnerable devices from authenticating. Malicious actors used the accounts cloud-noc@mail.io and cloud-init@mail.io, and attackers downloaded device configurations and created local admin accounts (such as “audit”, “backup”, “itadmin”, “secadmin”, “support”, “svcadmin”, or “system”) for persistence. Fortinet temporarily disabled FortiCloud SSO on January 26, 2026, and re-enabled it on January 27, 2026 with restrictions that block login from devices running vulnerable versions. |
| Date of Disclosure | January 27, 2026 |
| Affected Assets | FortiOS, FortiManager, FortiAnalyzer, FortiProxy, FortiWeb |
| Vulnerable Software Versions | FortiOS: 7.6.0 through 7.6.5, 7.4.0 through 7.4.10, 7.2.0 through 7.2.12, 7.0.0 through 7.0.18FortiManager: 7.6.0 through 7.6.5, 7.4.0 through 7.4.9, 7.2.0 through 7.2.11, 7.0.0 through 7.0.15FortiAnalyzer: 7.6.0 through 7.6.5, 7.4.0 through 7.4.9, 7.2.0 through 7.2.11, 7.0.0 through 7.0.15FortiProxy: 7.6.0 through 7.6.4, 7.4.0 through 7.4.12, 7.2.0 through 7.2.15, 7.0.0 through 7.0.22FortiWeb: 8.0.0 through 8.0.3, 7.6.0 through 7.6.6, 7.4.0 through 7.4.11Products Under Investigation: FortiSwitch Manager |
| PoC Available | No public PoC, but the vulnerability has been exploited in the wild. Fortinet’s advisory provides IOCs and details about the attack methodology observed. |
| Exploitation Status | Fortinet confirmed active exploitation by two malicious FortiCloud accounts discovered on January 22, 2026. |
| Patch Status | The majority of patches are pending. Only the 8.0, 7.6, 7.4 branches for FortiOS, FortiManager, and FortiAnalyzer appears to have immediate fixes available.Patches Available Now:FortiOS: Upgrade to 7.4.11 or 7.6.6.FortiManager: Upgrade to 7.4.10 or 7.6.6.FortiAnalyzer: Upgrade to 7.2.12 or 7.0.16. |
Censys Perspective
At the time of writing, Censys observes 3,280,081 exposed Web Properties.
Note that a single IP address often supports many distinct applications by hosting them on different ports or distinguishing them by hostname (Virtual Hosting). Consequently, scanning for ‘Web Properties’ identifies every unique service running on the server, whereas scanning by IP alone consolidates them into a single record. This is why the number of Web Properties observed often differs from the IP-based location map shown above.
Exposed Hosts and Web Properties are trackable with the following queries:
(host.operating_system.product = "fortios" or host.services.software.product: {"fortigate", "fortiweb", "fortimanager"} or host.services.endpoints.http.html_title: "FortiAnalyzer" or host.services.cert.parsed.subject.organizational_unit = "FortiAnalyzer") or (web.operating_systems.product = "fortios" or web.software.product: {"fortigate", "fortiweb", "fortimanager"} or web.endpoints.http.html_title: "FortiAnalyzer" or web.cert.parsed.subject.organizational_unit = "FortiAnalyzer")(host.services.software.product: {"fortios", "fortigate", "fortiweb", "fortimanager"} or host.services.http.response.html_title: "FortiAnalyzer" or host.services.tls.certificates.leaf_data.subject.organizational_unit = "FortiAnalyzer") or (web_entity.instances.software.product: {"fortios", "fortigate", "fortiweb", "fortimanager"} or web_entity.instances.http.response.html_title: "FortiAnalyzer" or web_entity.instances.tls.certificates.leaf_data.subject.organizational_unit = "FortiAnalyzer")services.software.product: {"fortios","fortigate","fortiweb","fortimanager"} or services.http.response.html_title: "FortiAnalyzer" or services.tls.certificates.leaf_data.subject.organizational_unit = "FortiAnalyzer"




