Vulnerability Description
CVE-2026-21858 is a critical unauthenticated remote code execution (RCE) vulnerability in n8n, a widely used workflow automation platform. The vulnerability allows a remote attacker with no authentication to execute arbitrary system commands by abusing workflow execution and credential handling logic, resulting in full compromise of the underlying host. This includes the ability to deploy malware, steal secrets, and pivot laterally. The issue affects n8n versions prior to 1.121.0 with the highest risk observed in self-hosted, internet-exposed deployments, including Docker-based installations.
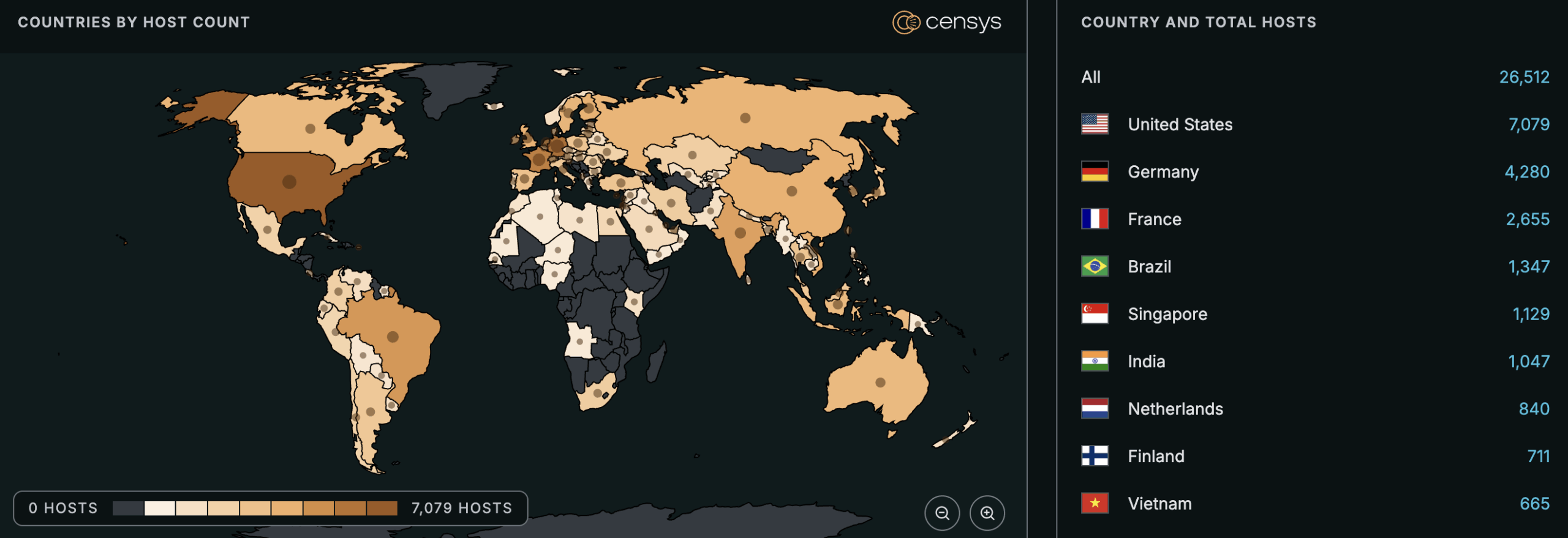
See the full breakdown by country in Censys Platform →
| Field | Description |
| CVE-ID | CVE-2026-21858 – CVSS score: 10 – assigned by GitHub |
| Vulnerability Description | A critical unauthenticated remote code execution (RCE) vulnerability in n8n, that allows a remote attacker with no authentication to execute arbitrary system commands by abusing workflow execution and credential handling logic, resulting in full compromise of the underlying host. This includes the ability to deploy malware, steal secrets, and pivot laterally. |
| Date of Disclosure | January 7, 2026 |
| Affected Assets | n8n automation workflow instances. |
| Vulnerable Software Versions | Versions below 1.121.0. Particularly impacts self-hosted and internet-exposed n8n deployments, including Docker-based installations. |
| PoC Available | Yes — public technical details and proof-of-concept exploitation steps are available in the Cyera Research Labs write-up. |
| Exploitation Status | No confirmed large-scale exploitation reported at disclosure time. Given the unauthenticated RCE nature and simplicity of exploitation, rapid weaponization is considered likely. |
| Patch status | n8n has released security updates addressing the issue in version 1.121.0. Organizations should upgrade immediately to the latest patched release provided by n8n. Internet-exposed n8n instances should be restricted or taken offline until patched. |
Censys Perspective
As of time of writing, Censys observes 26,512 exposed hosts, trackable with the following Censys queries:
host.services: (software.product: "n8n" and software.version < "1.121.0") or web.software: (product: "n8n" and version < "1.121.0")risks.name="Vulnerable n8n (Ni8mare) [CVE-2026-21858]"services.software: (product: "n8n" and version: {* to 1.121.0})References
- Cyera Research Labs — NI8MARE technical analysis:
Ni8mare – Unauthenticated Remote Code Execution in n8n (CVE-2026-21858) | Cyera Research Labs - Unauthenticated File Access via Improper Webhook Request Handling





