Vulnerability Description
This is a medium severity vulnerability that could allow an authenticated attacker to execute code on a FortiWeb system by crafting HTTP requests or CLI commands. At the time of writing this, there is suspicion that this exploit is being chained with CVE-2025-64446, but no confirmation from any official sources. CVE-2025-58034 comes just five days after the announcement of the previous vulnerability. See the full Censys advisory for CVE-2025-64446.
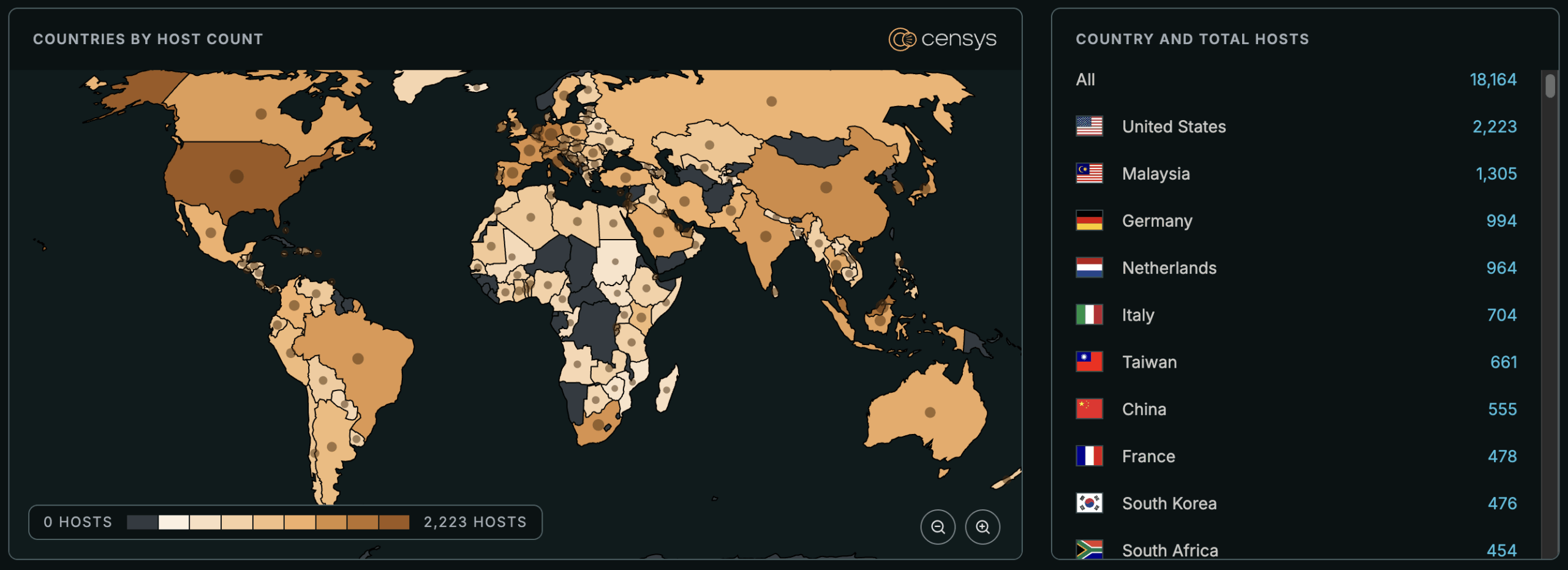
See the full breakdown by country in Censys Platform –>
| Field | Description |
| CVE-ID | CVE-2025-58034 — CVSS 6.7 — assigned by Fortinet, Inc. |
| Vulnerability Description | A medium-severity vulnerability that could allow an authenticated attacker to execute code on a FortiWeb system by crafting HTTP requests or CLI commands. At time of writing, there is suspicion that this exploit is being chained with CVE-2025-64446, but no confirmation from official sources. |
| Date of Disclosure | November 18, 2025 |
| Affected Assets | FortiWeb |
| Vulnerable Software Versions | 8.x: 8.0.0 – 8.0.17.6.x: 7.6.0 – 7.6.57.4.x: 7.4.0 – 7.4.107.2.x: 7.2.0 – 7.2.117.0.x: 7.0.0 – 7.0.11 |
| PoC Available? | CVE-2025-58034 is being exploited in the wild according to multiple sources linked in the references below, and CISA has added this to their Known Exploited Vulnerability Catalog as of November 18th, 2025. |
| Exploitation Status | No known exploitation at time of writing. |
| Patch Status | The following versions of FortiWeb resolve this issue, according to Fortinet’s advisory FG-IR-25-513:FortiWeb 8.0.2FortiWeb 7.6.6FortiWeb 7.4.11FortiWeb 7.2.12FortiWeb 7.0.12 |
Censys Perspective
At the time of writing, Censys observes 22,246 exposed FortiWeb instances online, across all versions. These queries identify FortiWeb appliances but do not filter by version. They cannot confirm if a device is vulnerable because the specific version is not visible in the response data.
((web.cert.parsed.subject.common_name: “FortiWeb” or web.cert.parsed.subject.organizational_unit: “FortiWeb”) and (web.software.vendor: “fortinet”)) and not web.labels.value: “HONEYPOT”
web_entity.instances.software.vendor:”fortinet” and (web_entity.instances.tls.certificate.parsed.issuer.common_name: “FortiWeb” or web_entity.instances.tls.certificate.parsed.issuer.organizational_unit: “FortiWeb”) and not web_entity.instances.labels={honeypot, tarpit}
services.software.vendor:”fortinet” and services: (tls.certificate.parsed.subject.common_name: “FortiWeb” or tls.certificate.parsed.subject.organizational_unit: “FortiWeb”) and not labels={`honeypot`, `tarpit`}
References
- PSIRT | FortiGuard Labs
- NVD – CVE-2025-58034
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Critical Vulnerability in Fortinet FortiWeb Exploited in the Wild (Updated November 19, 2025 with information about CVE-2025-58034)





