Vulnerability Description
CVE-2025-47812 is a critical vulnerability affecting Wing FTP Server versions prior to 7.4.3. The vulnerability stems from improper handling of NULL bytes in the /loginok.html endpoint when processing the username parameter. This flaw allows attackers to inject arbitrary Lua code into user session files. If exploited successfully, an unauthenticated attacker could execute arbitrary commands on the underlying server with root (Linux) or NT AUTHORITYSYSTEM (Windows) privileges, depending on the operating system.
Threat Activity
This vulnerability is not currently listed in CISA’s Known Exploited Vulnerabilities (KEV) Catalog. However, a proof of concept (PoC) exploit has been published on Exploit-DB, increasing the potential risk of exploitation in the wild.
| Field | Details |
|---|---|
| CVE-ID | CVE-2025-47812 – This vulnerability does not have a CVSS score and has not been published in NVD at the time of writing. Given that the vulnerability enables unauthenticated RCE, it is likely to be a critical vulnerability. |
| Vulnerability Description | Improper NULL byte handling in the /loginok.html endpoint allows unauthenticated RCE via Lua injection. |
| Date of Disclosure | July 2, 2025 |
| Date Reported as Actively Exploited | N/A |
| Affected Assets | /loginok.html endpoint in Wing FTP Server versions <= 7.4.3 |
| Vulnerable Software Versions | Wing FTP Server versions <= 7.4.3 |
| PoC Available? | Yes – published on exploit-db |
| Patch Status | Patched in Wing FTP Server version 7.4.4 (See Wing FTP download portal). |
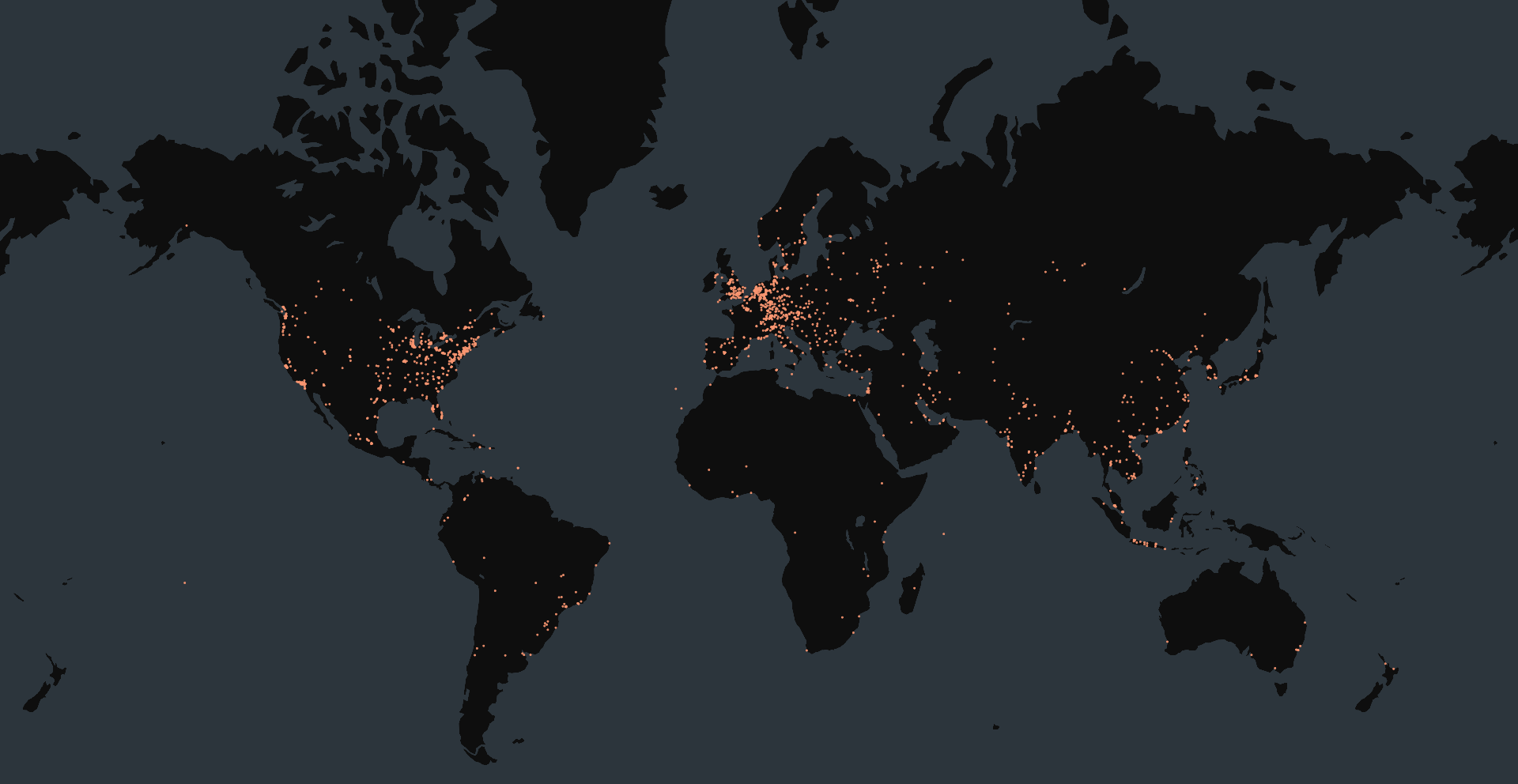
Censys Perspective
At the time of writing, Censys observed 8,103 exposed devices running Wing FTP Server. Of those, only 105 reported a version number. This is expected, as Wing FTP Server does not display the version by default. Instead, the server header often returns values such as:
- Wing FTP Server(tonyweb) – 1,500 instances
- Wing FTP Server(Free Edition) – 856 instances
- Wing FTP Server(UNREGISTERED) – 154 instances
Out of the 8,103 devices, 5,004 had exposed web interfaces. These typically displayed the Wing FTP Server – Web Client page title. Servers with this interface exposed are potentially vulnerable, as the exploit is performed using a malicious POST request, as demonstrated in the PoC exploit. The remaining hosts were identified through FTP and SSH banners. However, because they lack an exposed HTTP interface, they are not vulnerable to this specific exploit.
host.services.software: (vendor: "WFTPServer" and product: "Wing FTP Server") or web.software: (vendor: "WFTPServer" and product: "Wing FTP Server")host.services.software: (vendor="WFTPServer" and product="Wing FTP Server") or web_entity.instances.software: (vendor="WFTPServer" and product="Wing FTP Server")risks.name = "Vulnerable Wing FTP Server CVE-2025-47812"services.software: (vendor="WFTPServer" and product="Wing FTP Server")