Vulnerability Description
Two vulnerabilities, CVE-2025-4427 and CVE-2025-4428, have been identified in Ivanti Endpoint Manager Mobile (EPMM), with CVSS scores of 7.5 and 8.8, respectively.
- CVE-2025-4427 is an authentication bypass in the API component.
- CVE-2025-4428 is an authenticated remote code execution (RCE) vulnerability.
When chained, these flaws allow a remote attacker to bypass API authentication and execute arbitrary code as an authenticated user.
Threat Activity
CVE-2025-4427 and CVE-2025-4428 were both added to CISA’s Known Exploited Vulnerabilities (KEV) catalog on May 19, 2025.
Ivanti has confirmed the vulnerabilities are being actively exploited in the wild, stating: “We are aware of a very limited number of customers who have been exploited at the time of disclosure.” At the time of writing this advisory, Ivanti has not provided a reliable method to determine whether devices have been compromised.
WatchTowr labs published a detailed technical writeup on the vulnerabilities, and published proof of concept exploit code on GitHub.
| Field | Details | |
|---|---|---|
| CVE-ID | CVE-2025-4427 – CVSS 7.5 (high) – assigned by NVD. | CVE-2025-4428 – CVSS 8.8 (high) – assigned by NVD. |
| Vulnerability Description | An authentication bypass in Ivanti Endpoint Manager Mobile allows attackers to access protected resources without proper credentials. | A remote code execution vulnerability in Ivanti Endpoint Manager Mobile allowing attackers to execute arbitrary code on the target system |
| Date of Disclosure | May 13, 2025 | |
| Date Reported as Actively Exploited | May 19, 2025 | |
| Affected Assets | API Component of Ivanti EPMM. | |
| Vulnerable Software Versions | 11.12.0.4 and prior 12.3.0.1 and prior 12.4.0.1 and prior 12.5.0.0 and prior | |
| PoC Available? | WatchTowr published proof of concept exploit code for these vulnerabilities on GitHub. | |
| Exploitation Status | These vulnerabilities are being actively exploited and were added to CISA KEV on May 19, 2025. | |
| Patch Status | These vulnerabilities have been patched in the following versions: 11.12.0.5 12.3.0.2 12.4.0.2 12.5.0.1 New releases can be downloaded from Ivanti’s Download Portal. | |
At the time of writing, Censys observed 174 exposed Ivanti EPMM instances potentially vulnerable to this exploit chain. The majority of these are hosted in cloud environments, distributed across various providers with no single vendor standing out.
For the exposed instances, version data is available, though limited to major and minor versions. In some cases, this is enough to infer vulnerability, but in others, confirmation isn’t possible.
Below are the versions observed and their inferred vulnerability status:
| Observed Version | Vulnerability Status | Host Count |
| 12.5 | Potentially. Patch was applied in 12.5.0.1 | 67 |
| 12.4 | Potentially. Patch was applied in 12.4.0.2 | 27 |
| 12.3 | Potentially. Patch was applied in 12.3.0.2 | 21 |
| 11.12 | Potentially. Patch was applied in 11.12.0.5 | 18 |
| 11.11 | Vulnerable | 15 |
| 12.1 | Vulnerable | 9 |
| 12.2 | Vulnerable | 8 |
| 11.10 | Vulnerable | 6 |
| 12.0 | Vulnerable | 3 |
The queries below can be used to find exposed instances of Ivanti EPMM, but they are not necessarily vulnerable to the exploits.
host.services.software: (vendor: "Ivanti" and product: "Endpoint Manager Mobile") or web.software: (vendor: "Ivanti" and product: "Endpoint Manager Mobile")
services.software: (vendor="Ivanti" and product="Endpoint Manager Mobile")host.services.software: (vendor="Ivanti" and product="Endpoint Manager Mobile") or web_entity.instances.software: (vendor="Ivanti" and product="Endpoint Manager Mobile")
The query below can be used to find instances of Ivanti EPMM that are vulnerable to these exploits.
risks.name = "Vulnerable Ivanti Endpoint Manager Mobile [CVE-2025-4427 & CVE-2025-4428]"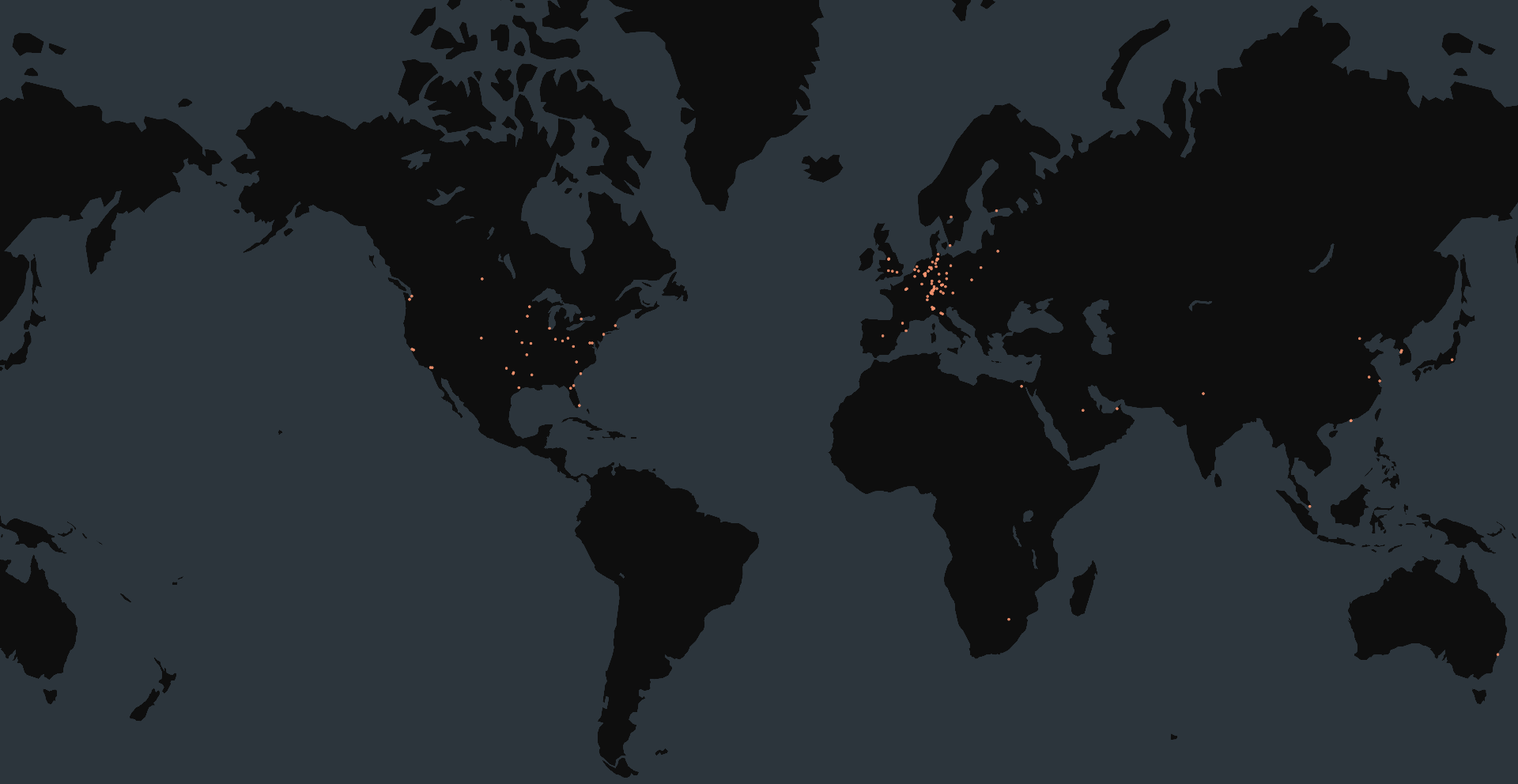
References
- https://nvd.nist.gov/vuln/detail/cve-2025-4427
- https://nvd.nist.gov/vuln/detail/cve-2025-4428
- https://labs.watchtowr.com/expression-payloads-meet-mayhem-cve-2025-4427-and-cve-2025-4428/
- https://github.com/watchtowrlabs/watchTowr-vs-Ivanti-EPMM-CVE-2025-4427-CVE-2025-4428
- https://forums.ivanti.com/s/article/Security-Advisory-Ivanti-Endpoint-Manager-Mobile-EPMM?language=en_US





