Date of Disclosure (source): April 9, 2025
Date Reported as Actively Exploited (source): May 5, 2025
CVE-2025-3248 is a critical vulnerability affecting Langflow versions prior to 1.3.0, with a CVSS score of 9.8. A remote unauthenticated attacker could exploit this vulnerability by sending crafted HTTP requests to the /api/v1/validate endpoint, potentially leading to arbitrary code execution.
Langflow is an open-source Python based web application that provides a low-code, visual interface for building agentic AI workflows.
Accepting user supplied Python code is a core feature of Langflow, but versions prior to 1.3.0 fail to restrict execution of code in certain instances.
Langflow’s /api/v1/validate endpoint filters input to only allow imports and function definitions, but still executes them. Executing a function definition only makes that code available in the Python namespace rather than executing the code inside. However, the exploit is still possible by abusing Python decorators, expressions that return functions wrapping other functions, to embed code or arbitrary commands. In addition to abusing decorators, command injection is possible by embedding code in Python default arguments that get executed when a function is defined.
| Field | Details |
|---|---|
| CVE-ID | CVE-2025-3248 – CVSS 9.8 (Critical) – assigned by Vulncheck |
| Vulnerability Description | An unauthenticated API endpoint /api/v1/validate enables attackers to embed malicious code or arbitrary commands in Python decorators and default arguments. |
| Date of Disclosure | April 9, 2025. |
| Affected Assets | /api/v1/validate endpoint in Langflow |
| Vulnerable Software Versions | Langflow versions prior to 1.3.0 |
| PoC Available? | Horizon3 published a technical writeup and proof of concept. They also published a Nuclei template that can be used to identify vulnerable devices. |
| Exploitation Status | CISA added this vulnerability to their Known Exploited Vulnerabilities (KEV) catalog on May 5, 2025. Additionally, this query in GreyNoise visualizer indicates that six malicious IPs were attempting to exploit this vulnerability at the time of writing. |
| Patch Status | This vulnerability has been patched in Langflow version 1.3.0. |
Censys Perspective
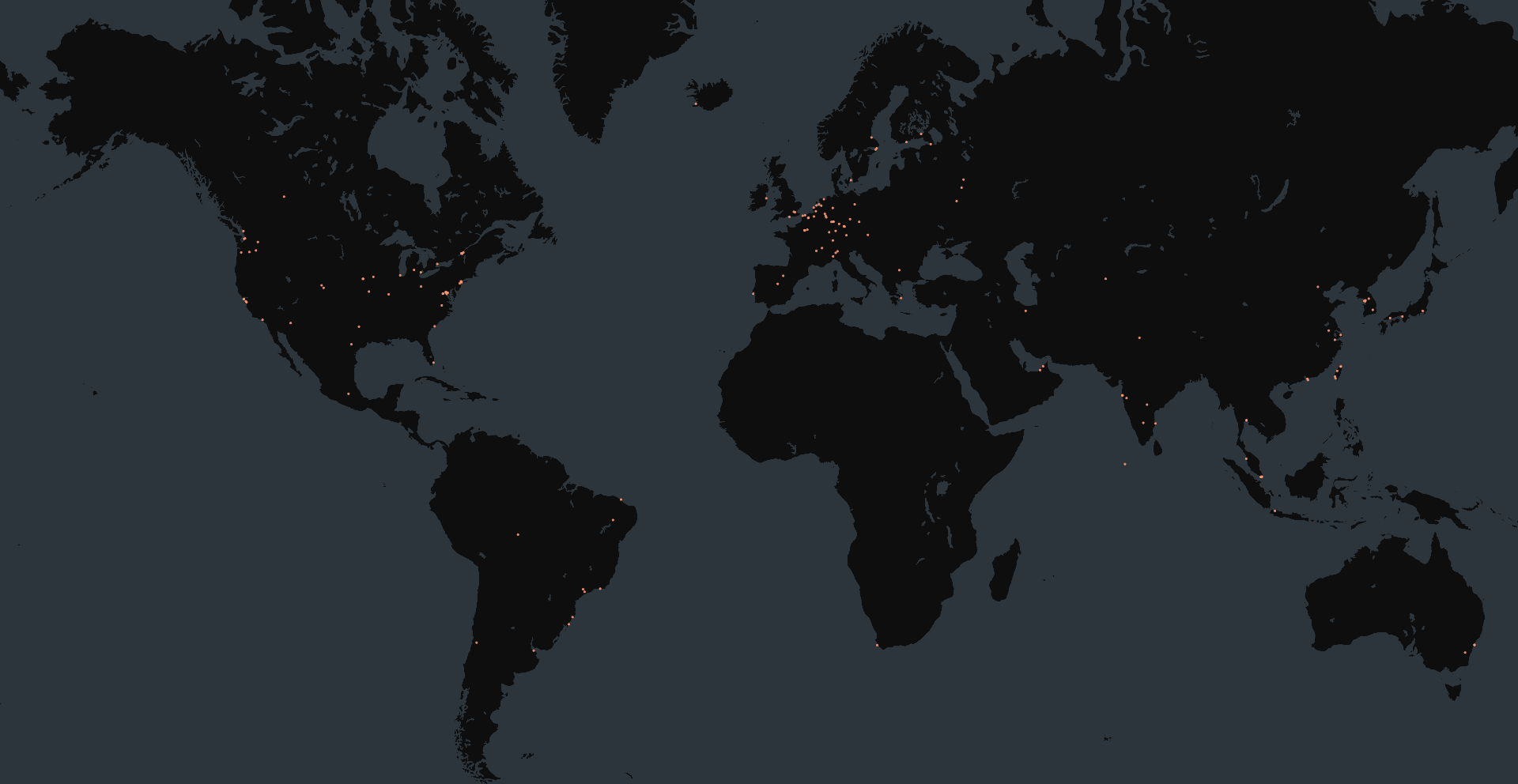
At the time of writing, Censys observed 1,156 exposed Langflow servers online, nearly half of which are located in the United States.
While we were unable to see versions directly on exposed Langflow servers, versions can be enumerated on servers that do not restrict access to their API using the following command:
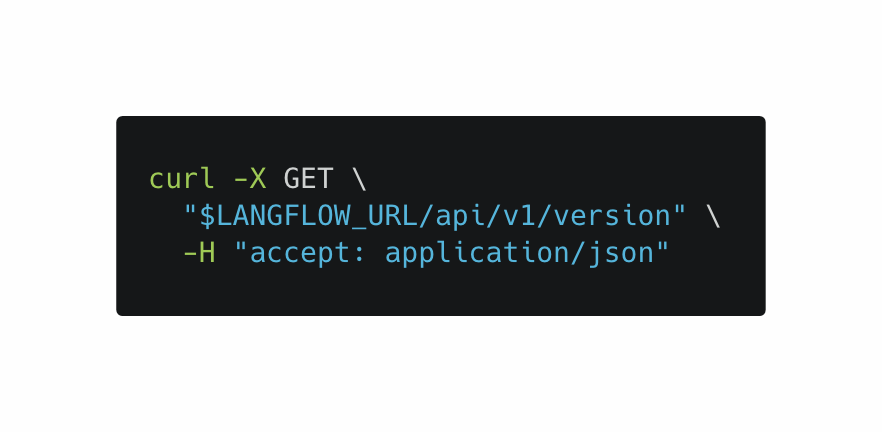
See below for an example of a successful response from the endpoint:
{"version":"1.1.3","main_version":"1.1.3","package":"Langflow"}There’s evidence that admins are patching their Langflow instances, albeit at a slow pace. Of the 1,156 exposures we detected, ~31% (360 servers) appear to be running a vulnerable version, ~25% (287 servers) appear to be running the patch (1.3.0), and the remaining 44% (509 servers) did not advertise a version.
Top 10 Most Commonly Observed Langflow Versions Vulnerable to CVE-2025-3248:
| # | Langflow Version | Host Count |
|---|---|---|
| 1 | 1.2.0 | 104 |
| 2 | 1.1.1 | 69 |
| 3 | 1.1.4 | 61 |
| 4 | 1.0.19 | 40 |
| 5 | 1.1.3 | 33 |
| 6 | 1.1.0 | 13 |
| 7 | 1.0.15 | 10 |
| 8 | 1.0.18 | 10 |
| 9 | 1.0.17 | 6 |
| 10 | 1.0.14 | 5 |
The table below breaks down the most commonly observed vulnerable versions in our scans.
The queries below can be used to identify exposed Langflow servers, but they are not necessarily vulnerable to the exploit.
web.software: (vendor: "Langflow" and product: "Langflow")services.software: (vendor="Langflow" and product="Langflow")host.services.software: (vendor="Langflow" and product="Langflow") or web_entity.instances.software: (vendor="Langflow" or product="Langflow")