Date of Disclosure (source): April 18, 2025
Date Reported as Actively Exploited (source): April 18, 2025
CVE-2025-32432 is a critical vulnerability affecting Craft CMS version 3.0.0-RC1-3.9.14, 4.0.0-RC1-4.14.14, and 5.0.0-RC1-5.6.16. If successfully exploited, it allows a threat actor to achieve remote code execution.
Orange Cyberdefense’s CSIRT team was credited with discovering the vulnerability and they published an in-depth technical analysis of the exploit. They described the following path to exploitation while investigating a compromised site built with CraftCMS 4.12.8:
- The threat actor sent multiple POST requests to /index.php?p=admin/actions/assets/generate-transform in order to enumerate a valid asset ID, an identifier used by Craft CMS to reference uploaded files like images. A valid asset ID is required to trigger the vulnerability.
- Once a valid asset ID was obtained, the attacker sent a second POST request to the same endpoint with a malicious handle object containing a crafted PHP class configuration.
- The attacker then sent a GET request containing injected PHP code, which Craft CMS saved in a temporary session file during a login redirect. They followed up with a POST request to the vulnerable endpoint that loaded and executed the misused class. This resulted in the download and creation of a PHP file manager, giving the attacker full remote access to the server.
| Field | Details |
|---|---|
| CVE-ID | CVE-2025-32432 – CVSS 10.0 (Critical) – assigned by NVD |
| Vulnerability Description | By sending specially crafted requests to the /index.php?p=admin/actions/assets/generate-transform endpoint, attackers can abuse insecure deserialization to execute arbitrary PHP functions. The vulnerability stems from how the handle object is processed during asset transformations, particularly when malicious fields are interpreted and instantiated without proper sanitization. |
| Date of Disclosure | April 18, 2025 |
| Affected Assets | Websites powered by Craft CMS that expose the /index.php?p=admin/actions/assets/generate-transform endpoint. Acquiring a valid asset id is prerequisite for exploitation. |
| Vulnerable Software Versions | Craft CMS versions 3.0.0-RC1-3.9.14, 4.0.0-RC1-4.14.14, and 5.0.0-RC1-5.6.16 |
| PoC Available? | A technical writeup and proof of concept has been published by Orange Cyberdefense. |
| Exploitation Status | In the technical writeup published by Orange Cyberdefense, they indicated threat actors had exploited this vulnerability as early as mid-February. Using the IoCs discovered during the analysis of this exploitation, they indicated that ~300 hosts may have been allegedly compromised. |
| Patch Status | Fixes are available in Craft CMS versions 3.9.15, 4.14.15, and 5.6.17. These patches additionally resolve the issue identified in CVE-2023-41892. |
Censys Perspective
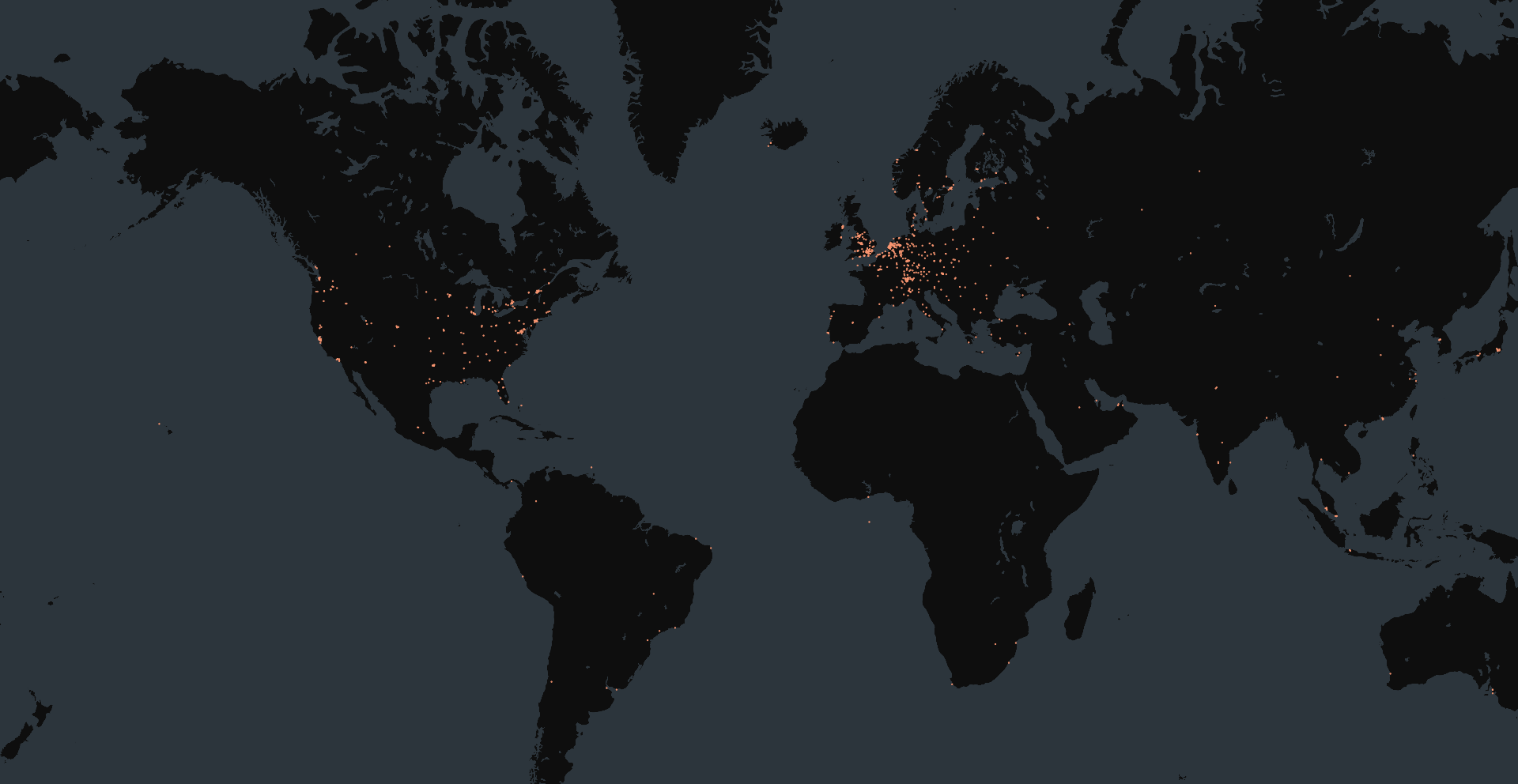
At the time of writing, Censys identified 78,984 sites powered by Craft CMS, with nearly half geolocated in the United States. Approximately 50% of these were hosted on infrastructure associated with Cloudflare, DigitalOcean, or Amazon, with the remainder distributed across various other cloud providers.
The queries below can be used to identify internet-facing instances of Commvault software, but they are not necessarily vulnerable to the exploit.
web.software.product: "Craft CMS"services.software.product="Craft CMS"host.services.software.product="Craft CMS" or web_entity.instances.software.product="Craft CMS"