Date of Disclosure (source): April 24, 2025 (SAP)
Date Reported as Actively Exploited (source): April 22, 2025 (ReliaQuest)
CVE-2025-31324 is a critical unauthenticated file upload vulnerability affecting SAP NetWeaver Visual Composer’s Metadata Uploader component.
This is an especially severe issue that combines several of the worst-case risk factors: it has a maximum CVSS score of 10.0, requires no authentication, affects a product that is widely adopted in large enterprise environments, and has already been actively exploited to achieve remote code execution.
SAP NetWeaver is an enterprise software stack designed to support large organizations in managing applications and business processes. The vulnerability arises from missing authorization checks on the /developmentserver/metadatauploader endpoint, allowing unauthenticated attackers to upload malicious executable files. This could potentially lead to remote code execution and full system compromise. Although Visual Composer is not installed by default, it’s a seemingly popular feature enabled on top of NetWeaver Application Server Java systems. Organizations can test for exposure by verifying whether the /developmentserver/metadatauploader endpoint is accessible without credentials.
ReliaQuest researchers first identified active exploitation on April 22, 2025, observing attackers uploading JSP webshells to the servlet_jsp/irj/root/ path to enable remote code execution through simple HTTP POST requests. Post-exploitation activity included deployment of Brute Ratel and Heaven’s Gate command-and-control frameworks. Multiple security firms have since also confirmed exploitation in the wild.
SAP has released an emergency patch for this vulnerability and strongly recommends that organizations apply Security Note 3594142 immediately. Note that SAP’s vendor advisory and patches (released as “SAP Security Notes”) are not publicly accessible and require a “SAP for Me” account to view.
| Field | Details |
|---|---|
| CVE-ID | CVE-2025-31324 – CVSS 10.0 (critical) – assigned by NVD |
| Vulnerability Description | An unauthenticated file upload vulnerability affecting the Metadata Uploader component of SAP NetWeaver Visual Composer. The flaw is the result of missing authorization checks to the “/developmentserver/metadatauploader” endpoint, allowing attackers to upload malicious files without authentication, which can be executed to achieve RCE. |
| Date of Disclosure | April 24, 2025 (SAP) |
| Affected Assets | SAP NetWeaver Visual Composer (VCFRAMEWORK 7.50) |
| Vulnerable Software Versions | SAP Visual Composer component for SAP NetWeaver 7.xx (all SPS) |
| PoC Available? | At the time of writing, no proof-of-concept (PoC) code has been publicly published for CVE-2025-31324, though exploitation techniques are trivial and have been documented by security researchers. |
| Exploitation Status | This vulnerability is being actively exploited with widespread exploitation observed by multiple security firms. |
| Patch Status | This vulnerability has been patched via SAP Security Note 3594142. Mitigations for organizations unable to immediately patch include disabling or preventing access to the vulnerable component, as detailed in SAP note 3596125. |
Censys Perspective
Given the severity of CVE-2025-31324 and ongoing active exploitation, we are currently holding off on publicly sharing direct Censys queries for identifying exposed and potentially vulnerable NetWeaver instances. However, as of this writing, Censys has observed approximately 7,562 SAP NetWeaver Application Servers exposed to the internet, primarily concentrated in the United States, India, and China.
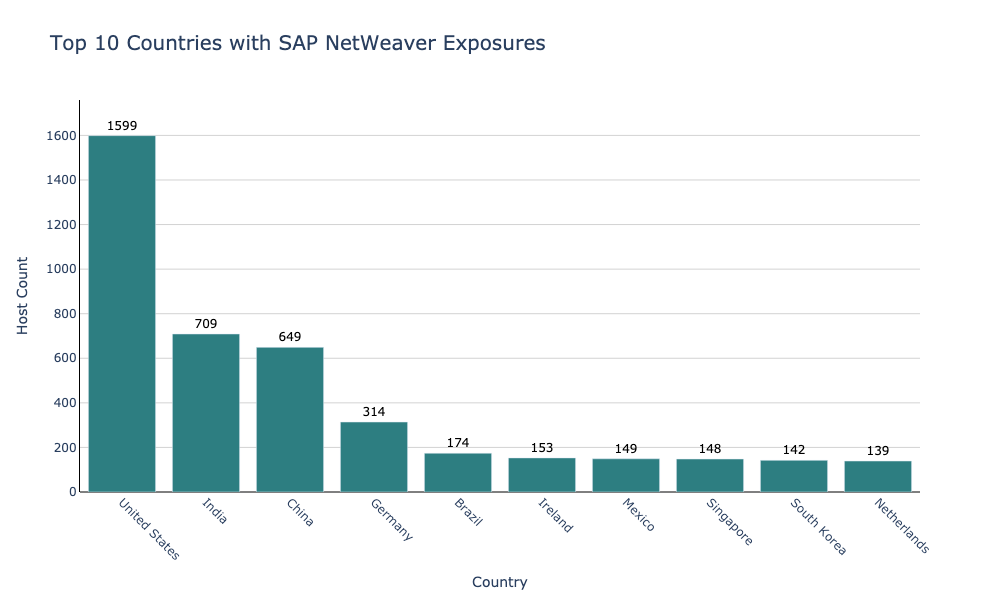
It’s important to note that not all observed instances are necessarily vulnerable, as this exploit requires the Metadata Uploader component to be enabled. Verifying whether an instance is affected is relatively straightforward, and can be done by checking if the affected /developmentserver/metadatauploader URL can be accessed without authentication. Current estimates from researchers suggest that between 50% and 70% of internet-facing SAP NetWeaver Application Server Java systems have the vulnerable Visual Composer component enabled.

References
- https://nvd.nist.gov/vuln/detail/CVE-2025-31324
- https://reliaquest.com/blog/threat-spotlight-reliaquest-uncovers-vulnerability-behind-sap-netweaver-compromise/
- https://www.bleepingcomputer.com/news/security/sap-fixes-suspected-netweaver-zero-day-exploited-in-attacks/
- https://onapsis.com/blog/active-exploitation-of-sap-vulnerability-cve-2025-31324/
- https://cyberscoop.com/sap-netweaver-zero-day-exploit-cve-2025-31324/





