Date of Disclosure (source): March 21, 2025
Date Reported as Actively Exploited (source): April 7, 2025
CVE-2025-31161 (initially tracked as CVE-2025-2825) is a critical vulnerability affecting CrushFTP versions 10.0.0-10.8.3 and 11.0.0-11.3.0. With a CVSS score of 9.8, this vulnerability allows unauthenticated remote attackers to bypass authentication.
Researchers from OutPost24 initially discovered this vulnerability, and ProjectDiscovery developed a proof of concept (PoC) exploit. The exploit requires three specific components:
- A specially crafted HTTP request to the /WebInterface/function/ endpoint
- A CrushAuth cookie that’s 44 characters in length following a specific format
- An AWS4-HMAC-SHA256 authorization header containing Credential=crushadmin/
Their technical writeup demonstrates how combining these components correctly may allow an attacker without valid credentials to gain unauthorized access to the server to then access files, upload malicious content, create additional users, and ultimately gain complete control of the server.
At the time of writing, this vulnerability was not observed to be actively exploited. However due its relatively low attack complexity, it may be a target for attackers in the future and users are encouraged to upgrade to version 10.8.4+ or 11.3.1+ immediately.
| Field | Details |
| CVE-ID | CVE-2025-31161 – CVSS 9.8 (critical) – assigned by VulnCheck |
| Vulnerability Description | Remote and unauthenticated HTTP requests to CrushFTP with known usernames can be used to impersonate a user and conduct actions on their behalf, including administrative actions and data retrieval. |
| Date of Disclosure | March 21, 2025. |
| Affected Assets | /WebInterface/function/ endpoint of CrushFTP servers running versions 10.0.0-10.8.3 and 11.0.0-11.3.0. |
| Vulnerable Software Versions |
|
| PoC Available? | ProjectDiscovery published a technical writeup detailing how the vulnerability may be exploited and provided a Nuclei template that assists with detection of the vulnerability. |
| Exploitation Status | We did not observe this vulnerability on CISA’s list of known exploited vulnerabilities or in GreyNoise at the time of writing. |
| Patch Status | This vulnerability has been patched in CrushFTP versions 10.8.4+ and 11.3.1+. The vendor has provided additional details about patching affected assets here. |
Censys Perspective
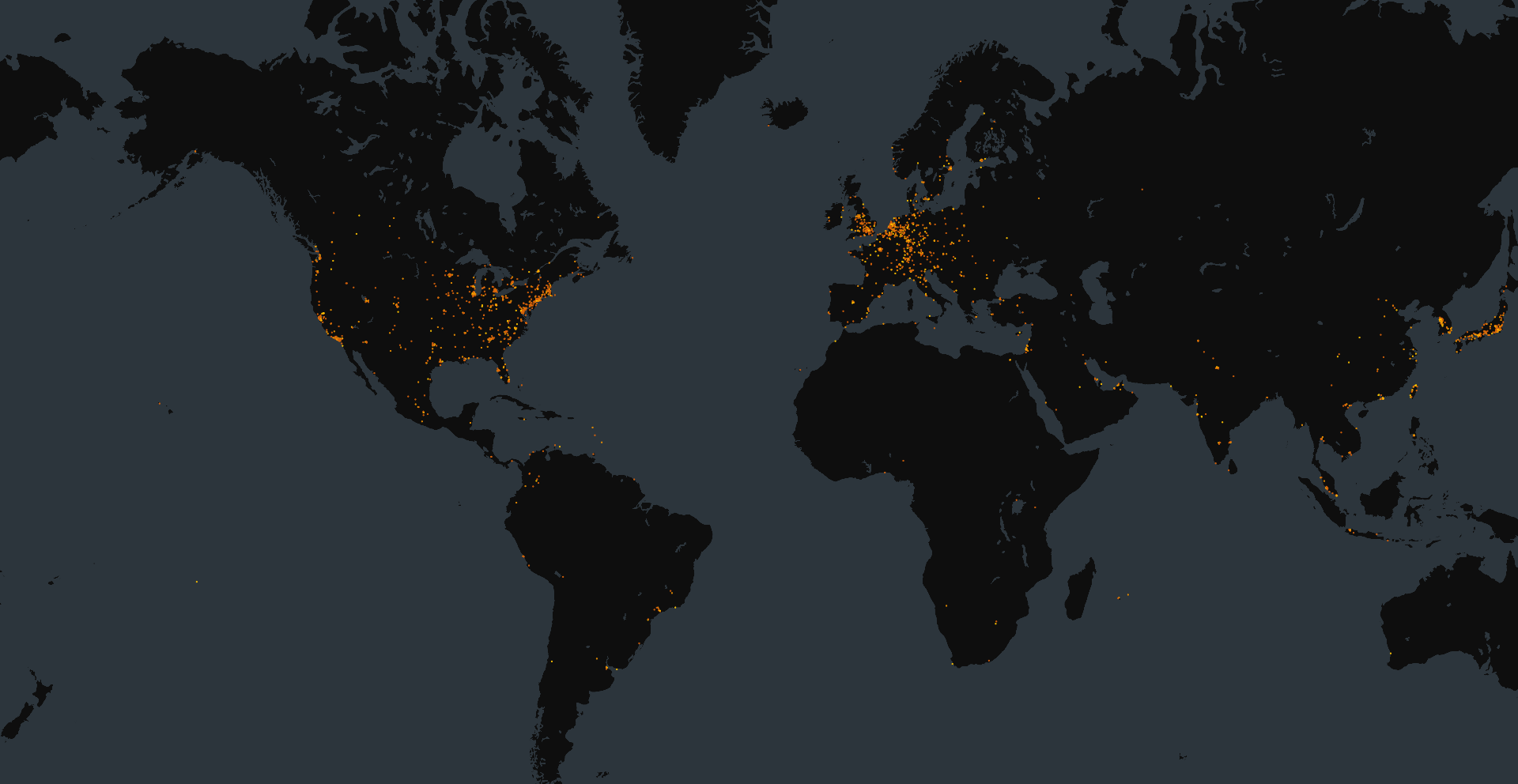
At the time of writing, Censys observed 7,524 exposed CrushFTP instances online. While we were unable to detect instances running CrushFTP10, we were able to identify 989 exposed CrushFTP11 instances, and confirmed that 287 exposed a version that is vulnerable to the exploit.
These exposures include our observations of CrushFTP web interfaces, which is where we were able to identify versions. Exposed banners indicating CrushFTP on the FTP service did not reveal any versions.
Note that not all instances observed are necessarily vulnerable as we do not always have specific versions available.
Map of Exposed CrushFTP Instances:
The queries below can be used to identify exposed instances of CrushFTP, but they are not necessarily vulnerable to the exploit.
host.services.software: (vendor:”CrushFTP” and product: {“CrushFTP”, “CrushFTP Web Interface”})
services.software: (vendor=”CrushFTP” and product: {“CrushFTP”, “CrushFTP Web Interface”})
host.services.software: (vendor=”CrushFTP” and product: {“CrushFTP”, “CrushFTP Web Interface”})
The query below can be used to identify exposed instances of CrushFTP that are vulnerable to the exploit.
risks.name = “Vulnerable CrushFTP [CVE-2025-2825, CVE-2025-31161]”





