Date of Disclosure (source): April 3, 2025
Date Reported as Actively Exploited (source): April 4, 2025
CVE-2025-22457 is a critical stack-based overflow vulnerability with a CVSS score of 9.0, affecting the following Ivanti products:
- Ivanti Connect Secure before version 22.7R2.6
- Ivanti Policy Secure before version 22.7R1.4
- Ivanti ZTA Gateways before version 22.8R2.2
If successfully exploited, this vulnerability allows a remote unauthenticated attacker to achieve remote code execution.
This vulnerability is known to be actively exploited and was added to CISA’s Known Exploited Vulnerabilities (KEV) catalog on April 4, 2025. Ivanti noted in their April Security Advisory that they are aware of a “limited number of customers whose Ivanti Connect Secure appliances have been exploited at the time of disclosure.”
According to Mandiant’s Incident Response team, exploitation attempts were first detected in mid-March 2025. Analysis of compromised systems revealed the presence of multiple malware families, including two that were previously unknown: TRAILBLAZE, which operates exclusively in memory, and BRUSHFIRE, a passive backdoor. They also identified the SPAWN malware framework, which has been linked to UNC5221. This threat actor, believed to be operating out of China, has a history of targeting edge devices with zero-day exploits since at least 2023.
Affected instances of Ivanti Connect Secure have been patched in version 22.7R2.6. A patch (22.7R1.4) is scheduled for Ivanti Policy Secure on April 21, 2025, and a patch (22.8R2.2) for ZTA Gateways is scheduled for April 19, 2025. Users of Pulse Connect Secure (EoS) are instructed to contact Ivanti to migrate their instances. Additional instructions and information regarding this vulnerability is available in Ivanti’s April Security Advisory.
| Field | Details |
|---|---|
| CVE-ID | CVE-2025-22457 – CVSS 9.0 (critical) – assigned by Ivanti |
| Vulnerability Description | A stack-based buffer overflow in Ivanti Connect Secure before version 22.7R2.6, Ivanti Policy Secure before version 22.7R1.4, and Ivanti ZTA Gateways before version 22.8R2.2 allows a remote unauthenticated attacker to achieve remote code execution. |
| Date of Disclosure | April 3, 2025 |
| Affected Assets | Ivanti Connect & Policy Secure and ZTA Gateway. |
| Vulnerable Software Versions |
|
| PoC Available? | We did not observe any public exploits available at the time of writing. |
| Exploitation Status | This vulnerability is known to be actively exploited and was added to CISA KEV on April 4, 2025. |
| Patch Status | This vulnerability has been patched and instructions for applying the fix are available in Ivanti’s April Security Advisory. |
Censys Perspective
At the time of writing, Censys observed 32,249 exposed instances of Ivanti Connect Secure online. Due to its role as a network access control solution, Ivanti Policy Secure is typically deployed internally and not exposed to the internet. While we can detect Ivanti ZTA gateways, the number of exposed instances is negligible (fewer than 10).
Note that not all instances observed are necessarily vulnerable as we do not always have specific versions available.
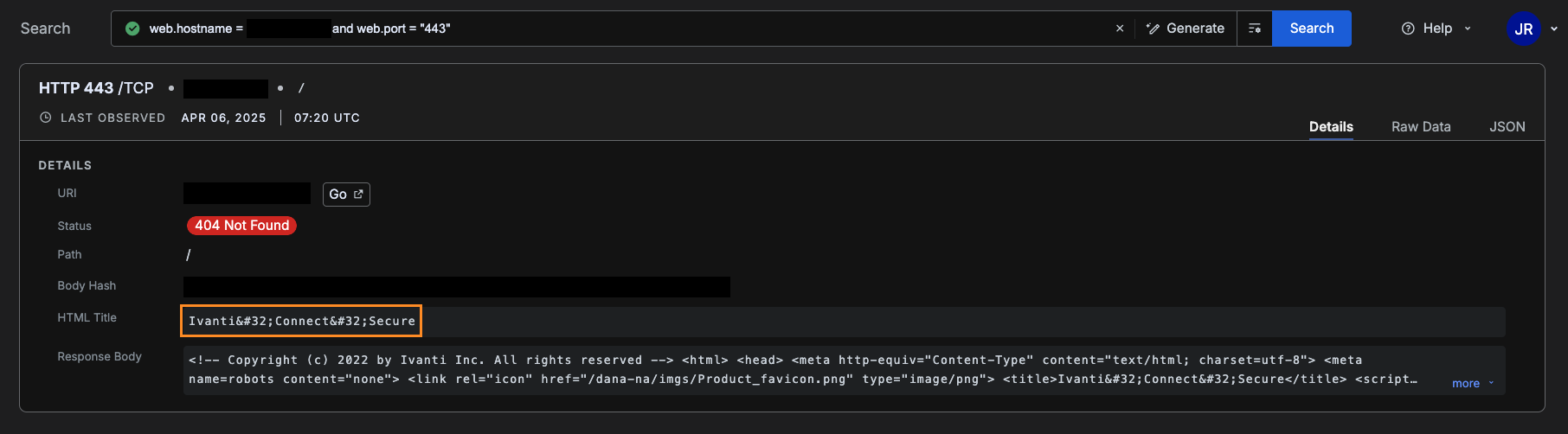
Map of Exposed Ivanti Connect Secure Appliances:
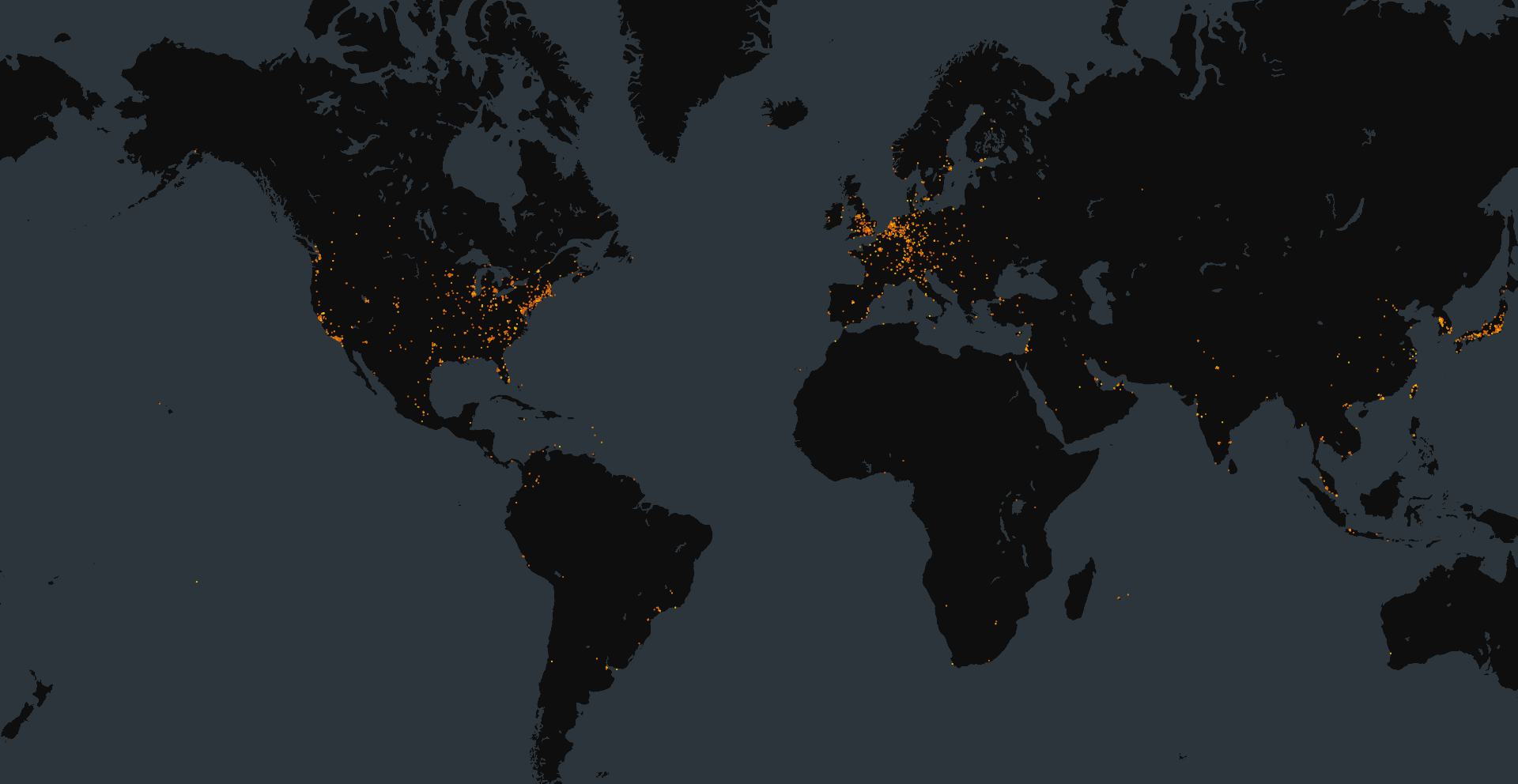
The queries below can be used to identify exposed instances of Ivanti Connect Secure, but they are not necessarily vulnerable to the exploit.
host.services.software: (vendor: “Ivanti” and product: “Connect Secure”)
services.software: (vendor= “Ivanti” and product= “Connect Secure”)
host.services.software: (vendor= “Ivanti” and product= “Connect Secure”)
The query below can be used to identify exposed instances of Ivanti Connect Secure that are vulnerable to the exploit.
risks.name = “Vulnerable Ivanti Connect Secure Application [CVE-2025-22457]”





