Vulnerability Description
On December 17, Cisco disclosed an unpatched zero-day vulnerability in AsyncOS, the operating system used by Cisco Secure Email Gateway (ESA). Public reporting and independent researcher commentary indicate that the flaw enables unauthenticated remote compromise, though full technical details remain limited pending a patch. The flaw is being actively exploited in the wild to compromise vulnerable systems. It has been assigned CVE-2025-20393 with a CVSS score of 10.
According to Cisco, this flaw specifically affects “a limited subset of appliances with certain ports open to the internet that are running Cisco AsyncOS Software for Cisco Secure Email Gateway and Cisco Secure Email and Web Manager.” These appliances are only vulnerable when configured with the Spam Quarantine feature (this feature is not enabled by default). The Spam Quarantine feature uses the Management interface and port 6025.
See the full breakdown by country in Censys Platform →
| Field | Description |
| CVE-ID | CVE-2025-20393 — CVSS 10 (critical) — assigned by Cisco |
| Vulnerability Description | An unpatched zero-day vulnerability in AsyncOS, the operating system used by Cisco Secure Email Gateway (ESA), allows unauthenticated remote compromise. |
| Date of Disclosure | December 17, 2025 |
| Affected Assets | Cisco Secure Email Gateway (ESA) appliances running AsyncOS with Spam Quarantine configured. Note that Spam Quarantine is not enabled by default. |
| Vulnerable Software Versions | All releases of Cisco AsyncOS Software are affected. |
| PoC Available? | As of writing, no public proof-of-concept exploit has been released. |
| Exploitation Status | Confirmed active exploitation in the wild per Cisco and third-party reporting. Attacks were observed prior to patch availability. |
| Patch Status | There is no patch available at time of disclosure.Cisco recommends applying temporary mitigations and monitoring guidance until fixed releases are published. |
Censys Perspective
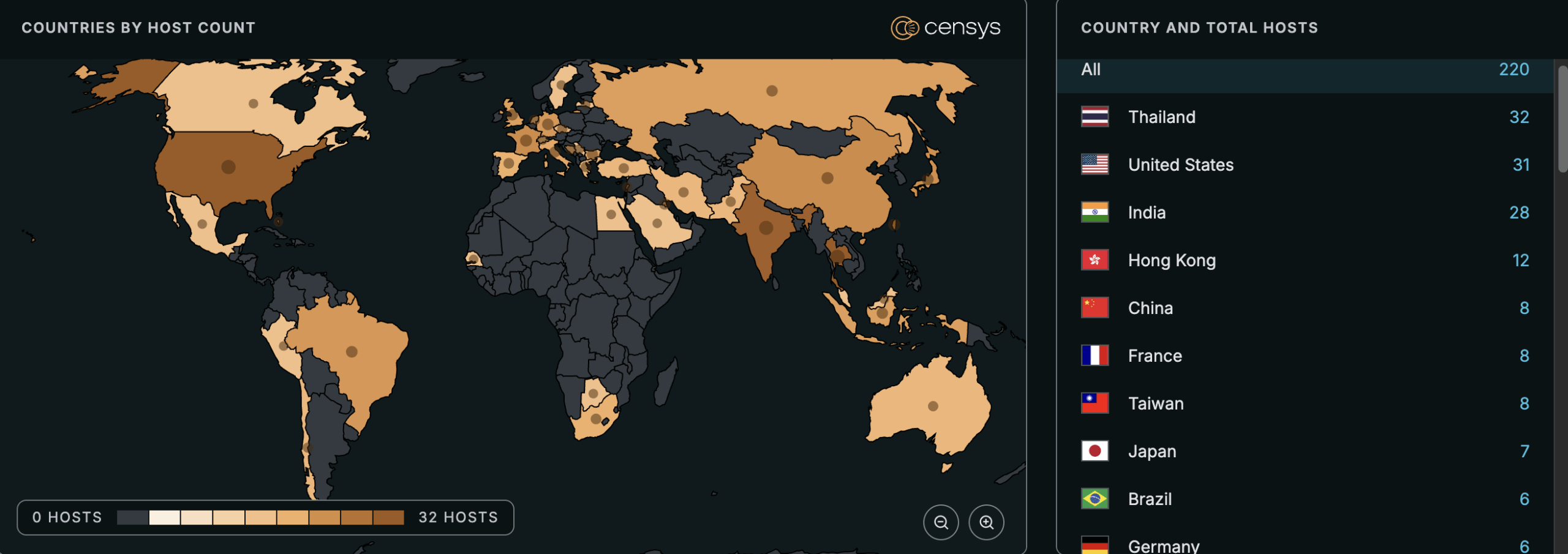
At the time of writing, Censys observes 220 internet-exposed Cisco ESA instances. Not all are vulnerable: only appliances with the Spam Quarantine feature enabled are affected. Review any exposed ESA instances in your environment to determine whether Spam Quarantine is enabled; by default, this feature is associated with TCP ports 80, 82, 83, and 6025. The following Censys queries can be used to track Internet-exposed instances:
host.services.endpoints.http.headers: (key: "Server" and value: "glass/1.0 Python/2.6.4")ASM:
host.services.http.response.headers: (key: "Server" and value: "glass/1.0 Python/2.6.4")services.http.response.headers: (key: "Server" and value.headers: "glass/1.0 Python/2.6.4")




