Vulnerability Description
A vulnerability in a specific API of Cisco ISE and Cisco ISE-PIC could allow an unauthenticated, remote attacker to execute arbitrary code on the underlying operating system as root. The attacker does not require any valid credentials to exploit this vulnerability. This vulnerability is due to insufficient validation of user-supplied input. An attacker could exploit this vulnerability by submitting a crafted API request. A successful exploit could allow the attacker to obtain root privileges on an affected device.
While this vulnerability was originally disclosed in July of 2025, Amazon reported on November 12, 2025 that they’ve observed an APT group targeting this vulnerability.
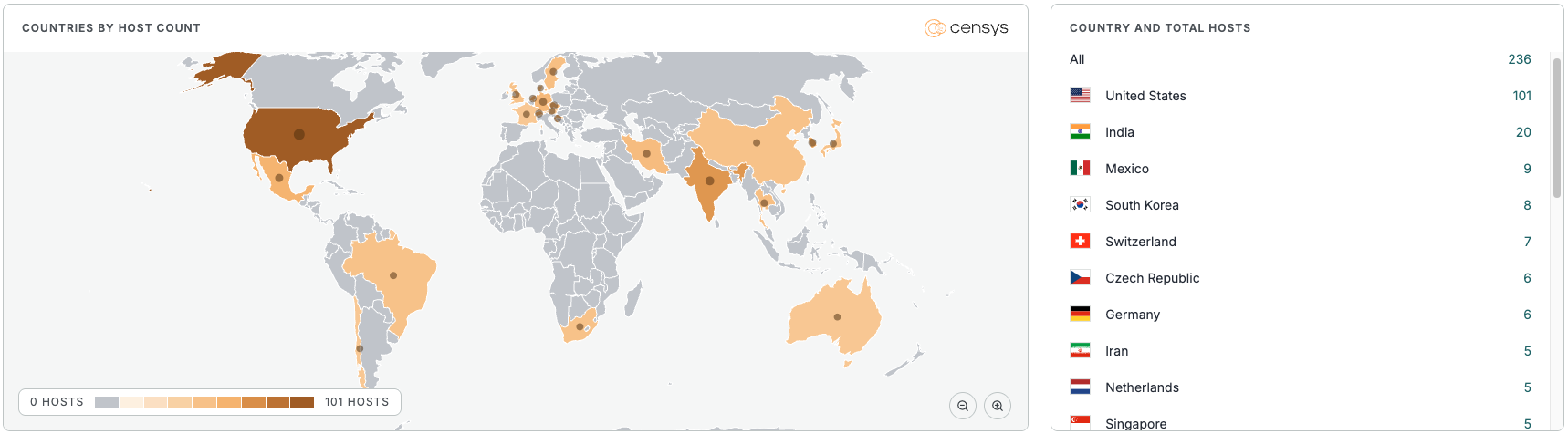
See the full breakdown by country in Censys Platform –>
| Field | Description |
| CVE-ID | CVE-2025-20337 — CVSS 10 — assigned by Cisco Systems, Inc. |
| Vulnerability Description | A vulnerability in a specific API of Cisco ISE and Cisco ISE-PIC could allow an unauthenticated, remote attacker to execute arbitrary code on the underlying operating system as root. The attacker does not require any valid credentials to exploit this vulnerability. This vulnerability is due to insufficient validation of user-supplied input. An attacker could exploit this vulnerability by submitting a crafted API request. A successful exploit could allow the attacker to obtain root privileges on an affected device. |
| Date of Disclosure | July 16, 2025 |
| Affected Assets | CVE-2025-20281 and CVE-2025-20337: These vulnerabilities affect Cisco ISE and ISE-PIC releases 3.3 and 3.4, regardless of device configuration. These vulnerabilities do not affect Cisco ISE and ISE-PIC Release 3.2 or earlier. |
| Vulnerable Software Versions | Cisco ISE and ISE-PIC releases 3.3 and 3.4 |
| PoC Available? | Yes: On November 12, Amazon threat intelligence teams reported a threat actor exploiting this vulnerability. |
| Exploitation Status | Exploited. According to Amazon’s report: On November 12, researchers at Amazon published a report about observed exploitation attempts for CVE-2025-5777, a critical Citrix vulnerability dubbed “Citrix Bleed Two,” that they saw targeting their honeypot service prior to public disclosure. While investigating the Citrix exploits, Amazon’s threat intelligence team discovered the same attackers targeting Cisco Identity Service Engine (ISE) with an unknown vulnerability. They found an anomalous payload exploiting vulnerable deserialization logic in a previously undocumented ISE endpoint. Amazon shared their findings with Cisco, resulting in CVE-2025-20337. Critically, exploitation was occurring in production environments before Cisco had catalogued the vulnerability or released patches across all affected ISE versions. |
| Patch Status | Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability. |
Censys Perspective
The below queries identify all exposed instances of Cisco ISE and ISE-PIC, but not all are necessarily vulnerable, as we have limited visibility into specific versions running on these devices.
(((host.services.software.vendor = “cisco” or web.software.vendor = “cisco”) ) and (host.services.software.product = “identity_services_engine” or web.software.product = “identity_services_engine”)) and not host.services.labels.value = “HONEYPOT” and not web.labels.value = “HONEYPOT”
host.services.software: (vendor:”cisco” and product:”identity services engine”) or web_entity.instances.software: (vendor:”cisco” and product:”identity services engine”) and not host.labels:{“honeypot”, “tarpit”} and not web_entity.instances.labels:{“honeypot”, “tarpit”}
services.software: (vendor:”cisco” and product:”identity services engine”) and not labels:{“honeypot”, “tarpit”}





