Vulnerability Description
CVE-2025-10573 is a critical (CVSS 9.6) stored Cross-Site Scripting (XSS) vulnerability that allows a remote unauthenticated attacker to execute arbitrary JavaScript in the context of an administrator session. This can lead to session hijacking, privilege escalation, and potential compromise of the Ivanti Endpoint Manager (EPM) interface.
This vulnerability affects Ivanti Endpoint Manager versions prior to 2024 SU4 SR1 (11.0.6.2248). Version 2024 SU4 SR1 was released on December 9, 2025 and fixed the issue.
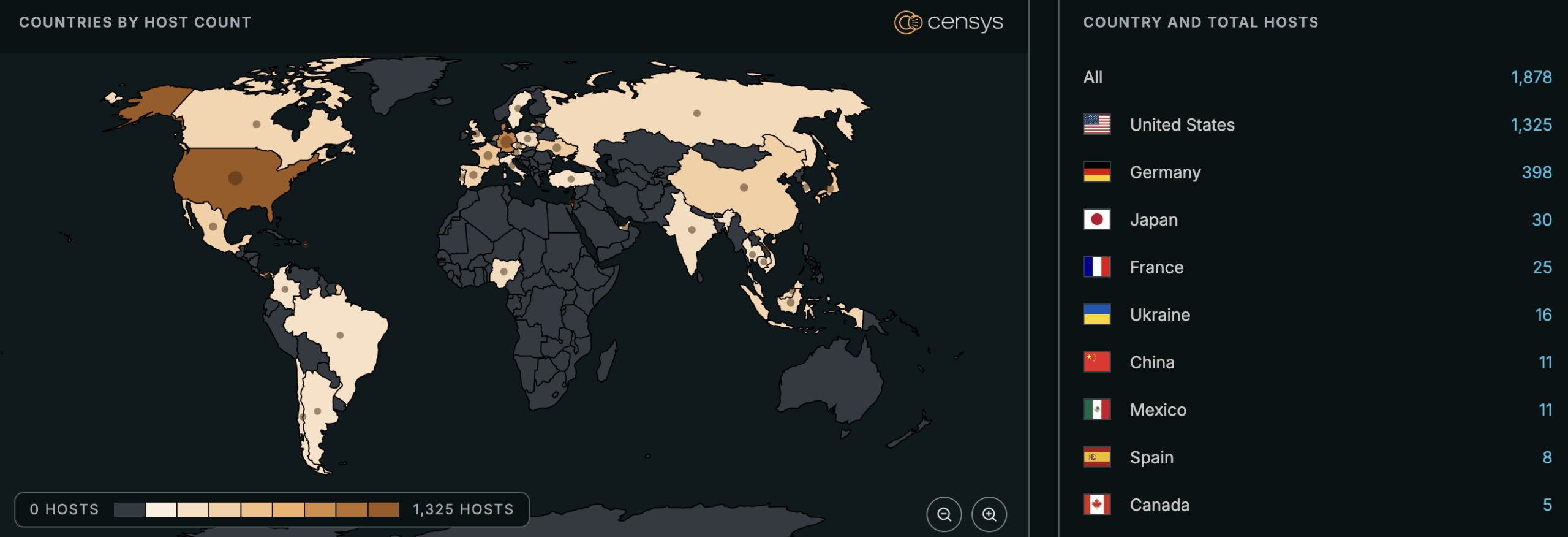
See the full breakdown by country in Censys Platform →
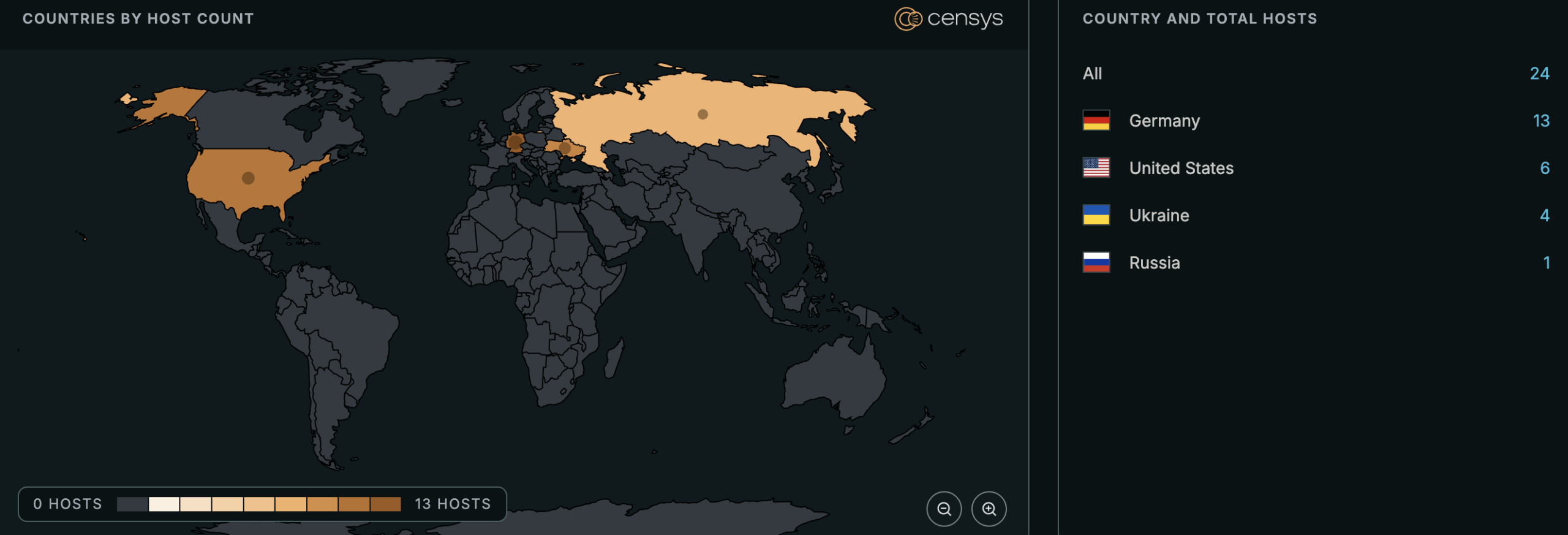
See the full breakdown by country in Censys Platform (requires Starter or above license) →
| Field | Description |
| CVE-ID | CVE-2025-10573 — CVSS 9.6 — assigned by Ivanti |
| Vulnerability Description | A stored Cross-Site Scripting (XSS) vulnerability that allows a remote unauthenticated attacker to execute arbitrary JavaScript in the context of an administrator session. This can lead to session hijacking, privilege escalation, and potential compromise of the Ivanti EPM interface. |
| Date of Disclosure | December 9, 2025 |
| Affected Assets | Ivanti Endpoint Manager (EPM) |
| Vulnerable Software Versions | Ivanti EPM instances running versions prior to 2024 SU4 SR1. |
| PoC Available? | Rapid7’s post on this issue contains the technical details for exploiting this vulnerability. |
| Exploitation Status | No known exploitation at time of writing, though attack complexity is rated “Low.” |
| Patch Status | Fixed in Ivanti EPM version 2024 SU4 SR1 available as of December 9, 2025. Immediately upgrade to Ivanti EPM version 2024 SU4 SR1 or later. |
Censys Perspective
At time of writing, Censys observes 1,898 exposed Ivanti EPM instances and 80 exposed instances running a vulnerable version.
Vulnerable instances can be found using the following queries:
Platform (requires Starter or above license to use regex):
host.services.software: (
product={
"endpoint_manager",
"landesk_management_suite"
}
and version=~"^(([0-9]|10).[0-9]+.[0-9]+.[0-9]+|11.0.[0-5].[0-9]+|11.0.6.([0-9]{1,3}|1[0-9]{3}|20[0-9]{2}|21[0-9]{2}|22[0-3][0-9]|224[0-7]))$"
)
or web.software: (
product={
"endpoint_manager",
"landesk_management_suite"
}
and version=~"^(([0-9]|10).[0-9]+.[0-9]+.[0-9]+|11.0.[0-5].[0-9]+|11.0.6.([0-9]{1,3}|1[0-9]{3}|20[0-9]{2}|21[0-9]{2}|22[0-3][0-9]|224[0-7]))$"
)ASM:
risks.name = "Vulnerable Ivanti Endpoint Manager [CVE-2025-10573]"services.software: (
vendor={"ivanti", "landesk"}
and product={
"landesk_management_suite",
"endpoint_manager"
}
and version: /.*(([0-9]|10).[0-9]+.[0-9]+.[0-9]+|11.0.[0-5].[0-9]+|11.0.6.([0-9]{1,3}|1[0-9]{3}|20[0-9]{2}|21[0-9]{2}|22[0-3][0-9]|224[0-7]))([^0-9].*)?/
)All exposed Ivanti EPM instances can be seen using the following queries:
host.services.software.product={"endpoint_manager", "landesk_management_suite"} services.software: (vendor={"ivanti", "landesk"} and product={"landesk_management_suite", "endpoint_manager"})




