Vulnerability Description
CVE-2024-54085 is a critical vulnerability affecting the American Megatrends Inc. (AMI) MegaRAC SPx firmware package for baseboard management controllers (BMCs). Attackers can bypass authentication in the Redfish Host Interface by modifying the X-Server-Addr or Host header in HTTP requests, tricking the BMC into believing requests originate from the host system itself. Exploitation does not require authentication.
BMC vulnerabilities are particularly dangerous due to the privileged scope in which BMC firmware operates. It exists outside the host operating system’s control and has full access to system resources. Traditional network controls offer little protection once a BMC is compromised, given its position in the system hierarchy.
Threat Activity
This vulnerability was added to CISA’s Known Exploited Vulnerabilities (KEV) Catalog on June 25, 2025. According to Eclypsium’s writeup, this marks the first instance of a BMC vulnerability being added to the KEV catalog.
| Field | Details |
|---|---|
| CVE-ID | CVE-2024-54085 – CVSS 10.0 (Critical) – assigned by AMI |
| Vulnerability Description | Authentication bypass via the Redfish Host Interface in AMI MegaRAC SPx |
| Date of Disclosure | March 11, 2025 |
| Date Reported as Actively Exploited | June 25, 2025 (Added to CISA KEV) |
| Affected Assets | Devices running AMI MegaRAC SPx firmware with the Redfish Host Interface exposed |
| Vulnerable Software Versions | AMI MegaRAC SPx versions 12.0-12.6 and 13.0-13.4 |
| PoC Available? | Eclypsium published a detailed writeup describing how a weak filtering check in /usr/local/redfish/extensions/host-interface/host-interface-support-module.lua allows attackers to modify the X-Server-Addr or Host fields in HTTP requests. By exploiting this vulnerability, an attacker can trick the BMC into treating malicious requests as if they originated from the host system, thereby bypassing authentication to the Redfish Host Interface. |
| Patch Status | Patched in MegaRAC SPx versions 12.7 and 13.5, per AMI’s security advisory |
Censys Perspective
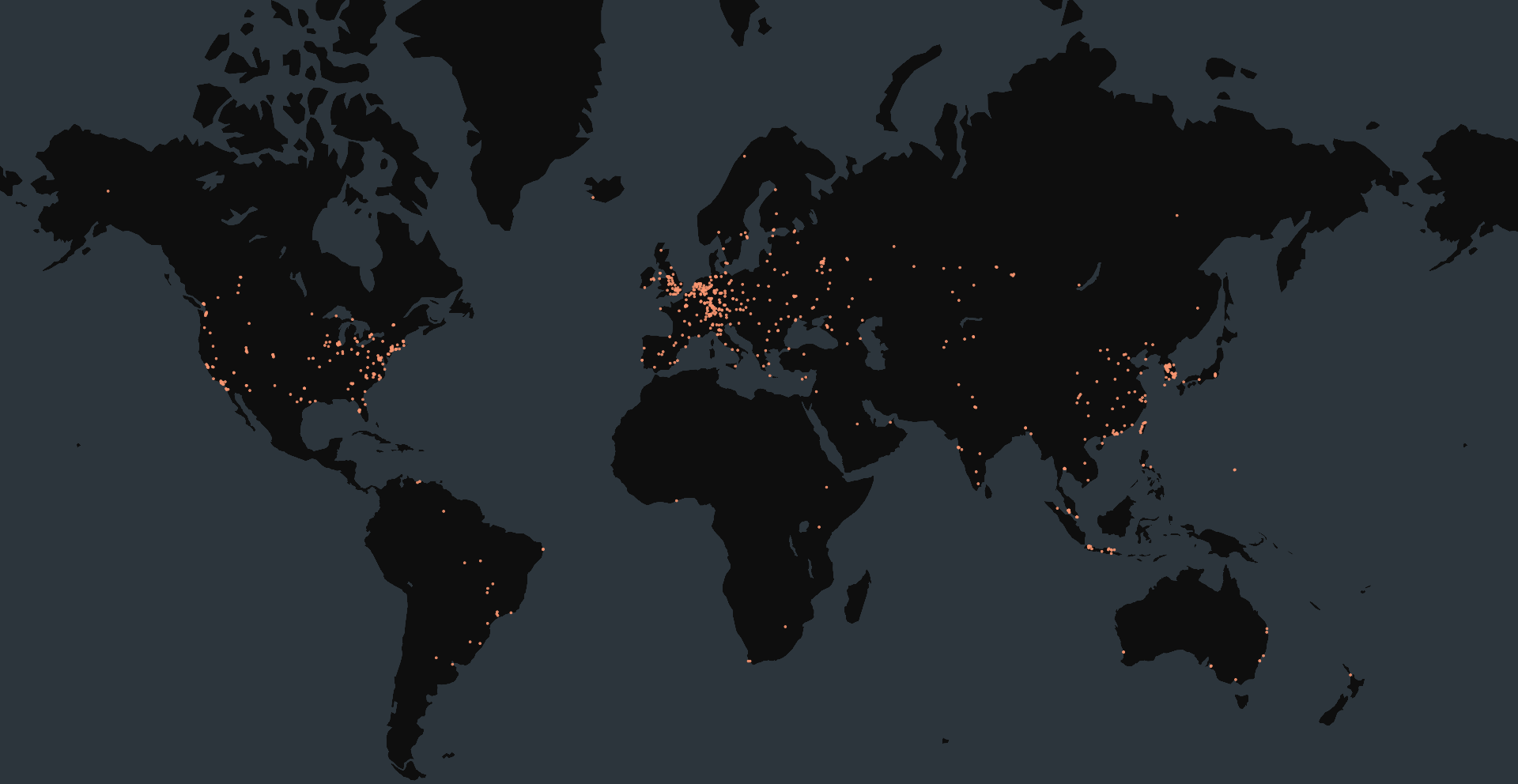
At the time of writing, Censys observed 4,110 exposed devices that we infer are running MegaRAC SPx firmware. This inference is based on the presence of TLS certificates believed to be issued by AMI.
While we lack definitive version information, it is straightforward to determine whether the Redfish API is exposed. Accessing https://[BMC-IP]/redfish will return a response like the one shown below if Redfish is active and exposed on the device.

host.services.software: (vendor: "ami" and product: "megarac_spx") or web.software: (vendor: "ami" and product: "megarac_spx")
host.services.software: (vendor="AMI" and product="MegaRAC SP-X") or web_entity.instances.software: (vendor="AMI" and product="MegaRAC SP-X")services.software: (vendor="AMI" and product="MegaRAC SP-X")