Vulnerability Description
CVE-2024-27443 is a Cross-Site Scripting (XSS) vulnerability (CVSS 6.1) affecting Zimbra Collaboration Suite (ZCS) versions 9.0 and 10.0.
The issue lies within the CalendarInvite feature of Zimbra’s Classic Web Client interface, where insufficient input validation of the Calender header allows for a stored cross-site scripting (XSS) attack.
An attacker can exploit this flaw by embedding a malicious payload into a crafted calendar header of an email. When a target views the message using the classic interface, the payload executes within their session context, enabling arbitrary JavaScript execution.
Threat Activity
CVE-2024-27443 was added to CISA’s Known Exploited Vulnerabilities (KEV) catalog on May 19, 2025. At the time of writing, no public proof-of-concept (PoC) exploit has been identified.
Recent reporting by ESET researchers suggests that the Sednit group (also known as APT28, Fancy Bear, Forest Blizzard, or Sofacy) may be linked to exploitation of this vulnerability as part of a broader campaign dubbed Operation RoundPress. This campaign targeted webmail platforms to facilitate credential theft and persistent access. For more information, refer to their full analysis.
| Field | Details |
|---|---|
| CVE-ID | CVE-2024-27443 – CVSS 6.1 (medium) – assigned by CISA-ADP |
| Vulnerability Description | A Cross-Site Scripting (XSS) vulnerability exists in the CalendarInvite feature of the Zimbra webmail classic user interface, because of improper input validation in the handling of the calendar header. An attacker can exploit this via an email message containing a crafted calendar header with an embedded XSS payload. When a victim views this message in the Zimbra webmail classic interface, the payload is executed in the context of the victim’s session, potentially leading to execution of arbitrary JavaScript code. |
| Date of Disclosure | August 12, 2024 |
| Date Reported as Actively Exploited | May 19, 2025 |
| Affected Assets | CalenderInvite feature of Zimbra webmail classic user interface of ZCS. |
| Vulnerable Software Versions | ZCS 9.0.0 (patches 1-38)ZCS 10.0.0 – 10.0.6 |
| PoC Available? | We did not observe any public exploits available at the time of writing. |
| Exploitation Status | ESET researchers reported evidence of Sednit Group (also known as APT28, Fancy Bear, Forest Blizzard, or Sofacy) exploiting this vulnerability and it was added to CISA KEV on May 19, 2025. |
| Patch Status | This vulnerability has been patched in ZCS 10.0.7 and 9.0.0 Patch 39. |
Censys Perspective
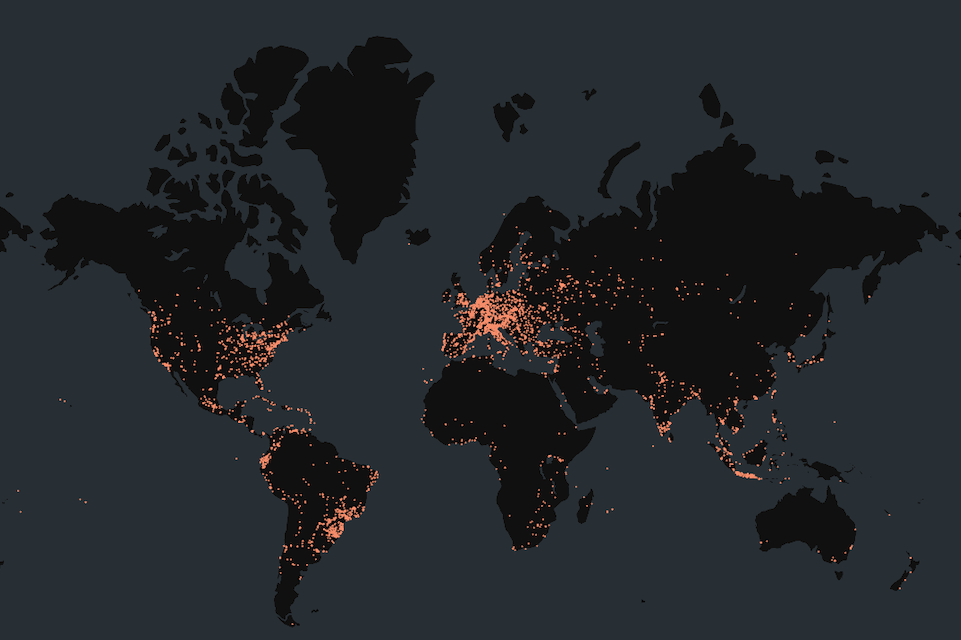
At the time of writing, Censys observed a total of 129,131 exposed ZCS instances that may potentially be vulnerable to this exploit. The vast majority are hosted within cloud infrastructure, distributed across a wide range of providers without any being disproportionately represented.
In contrast, we observed 33,614 on-premises ZCS hosts. These are primarily associated with IPs serving multiple hostnames, suggesting shared infrastructure.
Note that not all instances observed are necessarily vulnerable as we do not have specific versions available, and we are unable to verify if these devices are running the Zimbra webmail classic user interface.
host.services.software: (vendor: "Zimbra" and product: "Collaboration") or web.software: (vendor: "Zimbra" and product: "Collaboration")services.software: (vendor="Zimbra" and product="Collaboration")host.services.software: (vendor="Zimbra" and product="Collaboration") or web_entity.instances.software: (vendor="Zimbra" and product="Collaboration")